Who broke the Internet? Arkana Security names U.S. broadband provider on new DLS

Introduction
In 2024, Cyjax observed the emergence of 72 extortion and ransomware group data-leak sites (DLSs). As of late March 2025, Cyjax has identified DLSs for 19 new groups this year, as noted in recent blogs on extortion groups Morpheus, GD LockerSec, Babuk2, Linkc, and Anubis. The latest DLS Cyjax has identified is named Arkana or ArkanaSecurity (АрканаСекьюрити), which constitutes one of 12 new DLS’s identified in March 2025 alone. This group appears to operate independently rather than running a Ransomware-as-a-Service (RaaS) model, making no mention of hiring affiliates anywhere on its DLS. Alongside this, Cyjax has not noted the group’s presence on well-known cybercriminal forums.

Figure 1 – DLS sites which have emerged in 2025 by month.
Key takeaways
- ArkanaSecurity’s DLS first emerged in January 2025 with a post about the group, its processes, and contact details.
- As of late March 2025, the group’s DLS lists one victim. The affected organisation is WideOpenWest (WOW!).
- The detailed blog entry contains the name of the alleged victim, a description of the files which have been leaked, a countdown timer, and details about the intrusion itself. It also includes sample images and a video allegedly demonstrating access to the organisation.
- The group does not appear to have any accounts on prominent cybercriminal forums. ArkanaSecurity appears to work independently rather than as an RaaS, with no ties to other cybercriminal groups at the time of writing.
Context
Extortion groups commonly use DLSs to further extort victims, typically proceeding in multiple stages. The first threat is that the victim’s name and news of a successful attack against it will be published on the extortion group’s website. Should this fail to motivate a victim to pay a ransom, the group’s next step is typically to provide proof of the successful theft of its data, such as screenshots of internal file trees, samples of employee or customer PII, or other sensitive documents. The group may add a countdown at this stage, noting that should the victim fail to pay by the conclusion, it will make available to DLS visitors all stolen data, either for free or at cost.
The Arkana DLS
ArkanaSecurity brands itself as penetration testing, data security, and risk management provider. It has claimed that it "specializes in identifying and exposing critical vulnerabilities in company systems". Contact with the group can be made via the encrypted messaging platforms Session or Sonar, with links provided for each one. The group has also listed a public PGP key. This is often used as a means of providing evidence that it is the legitimate group being contacted. Additionally, it can also be used to carry out encrypted messaging. ArkanaSecurity has a main victim blog where it shares its posts, showing details about the victim organisation. This includes its name, revenue, industry, and website, as well as showing a countdown timer for when data from the organisation will be leaked.
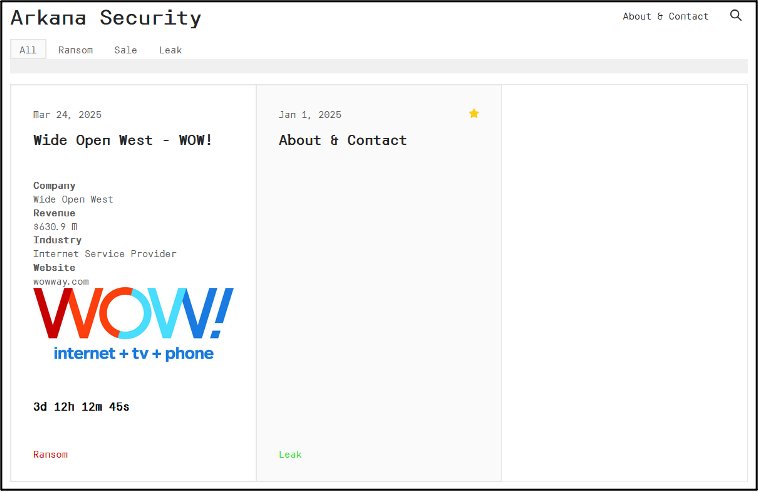
Figure 2 – Main ArkanaSecurity DLS page.
Aside from the victim blog, which currently only lists details from WOW!, ArkanaSecurity's DLS also has a section titled "About & Contact". This section describes at least part of the group's methodology, including a three-phase process it follows.
- “Ransom": The group will attempt to extort its alleged victim following a breach.
- "Sale": If an organisation "fails to act", the group will aim to sell data either via the "dark web" or to the purported victim. The latter is described as the "last chance" for the impacted organisation to prevent data being publicly disclosed.
- "Leak": In the "worst-case scenario", the data will be leaked publicly. This likely occurs if the group is unable to extort the claimed victim or sell the data to other threat actors. The only timer active on the groups DLS is believed to refer when its data will be published.
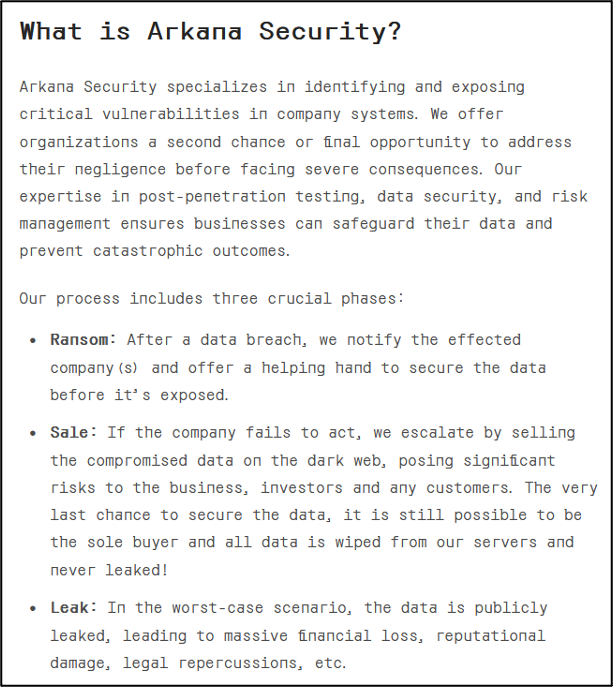
Figure 3 – ArkanaSecurity’s description of itself and its processes.
As of March 2025, ArkanaSecurity is not known to be associated with any other threat actors or cybercriminal forum accounts. As such, it is unclear where on the "dark web" the group would attempt its second phase and sell any purportedly stolen information. Whilst the group does have a “Sale” tab on its DLS, it currently does not show any data.
Figure 4 – ArkanaSecurity’s Sale page on its DLS.
Victimology
ArkanaSecurity has publicly claimed attacks against one organisation, namely telecommunications company WideOpenWest (WOW!). This organisation was listed on the group's DLS on 24 March 2025. WOW! Is the eighth largest cable operator in the US, providing telephone, television, and broadband services to over 1.9 million households and businesses in the country. There is a countdown timer linked to the victim post, which is currently set to expire on 29 March 2025.
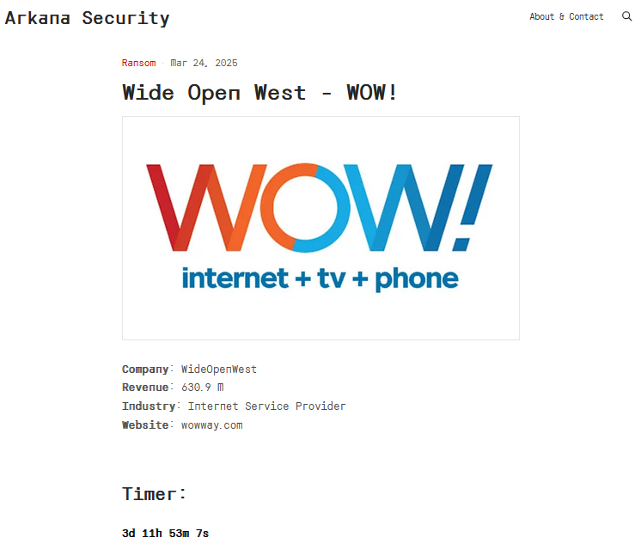
Figure 5 – Part of the WOW! listing on ArkanaSecurity’s DLS.
According to the post on its DLS, ArkanaSecurity claims that it breached Appian Cloud Security and telecommunications solutions provider Symphonica. This breach allowed full access to WOW!'s infrastructure. The group has provided sample images and a video allegedly demonstrating the access on its Tor site.
Through this access, the extortion group has stated that it stole records for around 403,000 WOW! customers. These stolen details purportedly include full names, usernames, passwords, customer and user IDs, and email addresses. It is currently unclear if the stolen passwords are hashed or stored in cleartext.
The group also claimed to have doxed WOW! CEO Teresa Elder, providing alleged details such as a physical address; Social Security number; identifiers such as email addresses and phone numbers; and relative names on its DLS. The names of other WOW! directors have also been listed. This is likely used to place further pressure on the victim to pay the ransom, combining this with public shaming tactics that can affect the organisation’s reputation.
Threat Assessment
As of late March 2025, there is little public information regarding the group and its operations apart from what it claims on its DLS. Whilst WOW! has not publicly confirmed an attack, the group’s post is very thorough, listing not only the types of data stolen but also “incident details” such as the access type gained from the compromise of Appian Cloud and Symphonica products used by the organisation. The threat actor has also posted images and a video showing the allegedly compromised victim infrastructure, which adds credibility to its claim. ArkanaSecurity has also displayed that it is willing to leak private information, including SSNs, from key C-suite employees within an organisation. Since this is only the first known claim by this group, it is highly likely that it will continue to conduct attacks and threaten to publish data.
To access our full intelligence repository containing detailed profiles like this one, covering extortion groups, advanced persistence threat groups (APTs), data brokers, hacktivists, initial access brokers, and more, click here to take a test drive of Cymon.
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
Get Started with CYJAX CTI
Empower Your Team. Strengthen Your Defences.CYJAX gives you the intelligence advantage: clear, validated insights that let your team act fast without being buried in noise.
