The MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) framework was developed in 2013 to document the tactics and techniques used by adversaries in cyberattacks. Initially an internal tool for threat detection, it became publicly available in 2015 to support the cybersecurity community. Over time, it has evolved into a comprehensive resource that describes adversary behaviours during attacks.
Regularly updated to reflect emerging threats, MITRE ATT&CK enhances threat intelligence, incident response, and proactive cybersecurity measures. By mapping adversary behaviours, it helps organisations to identify attack patterns and accelerate containment and recovery during a cyberattack.
Key Components of the MITRE ATT&CK Framework
The MITRE ATT&CK framework is divided into three main matrices, each focusing on different operational domains:
- Enterprise matrix: Describes adversary tactics and techniques within corporate networks and modern IT infrastructures including Windows, macOS, Linux, and cloud systems.
- Mobile matrix: Focuses on securing mobile platforms such as iOS and Android fromunique vulnerabilities and attack methods.
- ICS (Industrial Control Systems) matrix: Details tactics and techniques used to compromise industrial processes and physical systems like energy, manufacturing, and transportation.
The framework further organises cyber threats into categories, aiding collaboration and analysis:
- Tactics: High-level goals of adversaries during an attack.
- Techniques: The methods adversaries use to achieve these goals, with sub-techniques offering more detailed variations.
- Procedures: Real-world examples of how techniques and sub-techniques are implemented.
- Groups: Known threat actors associated with specific techniques.
- Software: Tools or malware adversaries use to execute techniques.
- Mitigations: Defensive measures to reduce the impact of techniques.
- Data Sources: Logs and information sources to detect adversary activities.
This structured approach provides a common language for security professionals, simplifying threat analysis and improving defences.
How is the MITRE ATT&CK Framework used?
MITRE ATT&CK is used by a range of users, including academics, government agencies, and CISOs to enhance understanding and defence against cyber threats. Its practical applications include:
Threat Intelligence
Providing a standardised way to map adversary tactics and techniques to attacker profiles, the framework helps organisations better predict behaviour, track trends, and enhance threat hunting. It also improves collaboration by offering a common language for intelligence sharing.
Defence Evaluation and Planning
By mapping defences to ATT&CK, threat intelligence teams can identify gaps in detection and mitigation strategies, prioritise defence planning, and validate security tools to ensure alignment with real-world adversary behaviours.
Red and Blue Team Exercises
Red teams use ATT&CK to emulate real-world adversary tactics. In contrast, blue teams structure detection and response strategies based on the framework. This shared approach strengthens collaboration and overall resilience.
Incident Response
ATT&CK allows responders to map observed activities to specific techniques, trace attack progression, and implement countermeasures. This accelerates containment and recovery whilst supporting post-incident analysis to refine defences.
How does MITRE ATT&CK compare to other frameworks?
MITRE ATT&CK excels in its detailed, adversary-focused approach, making it a highly effective tool for threat detection, response, and defence testing. Compared to broader governance frameworks like NIST CSF or post-incident tools like VERIS, ATT&CK is focused on real-time adversary behaviour and proactive defence. Whilst complementary tools like the Lockheed Martin Cyber Kill Chain and CAPEC address specific attack stages or methodologies, ATT&CK offers granularity in mapping techniques to practical applications.
| Framework | Comparison |
| Lockheed Martin Cyber Kill Chain | The Cyber Kill Chain is more linear and better suited for understanding attack progressions. However, by focusing on the stages of an incident, MITRE supports more granular mapping of attacker behaviours. This allows defenders to focus on specific techniques. |
| Diamond Model of Intrusion Analysis | The Diamond Model is focused on understanding the broad view of an intrusion. By analysing the relationships between adversaries, capabilities, victims, and infrastructure, it provides less concrete techniques and practical detail than MITRE. |
| NIST Cybersecurity Framework (CSF) | The NIST CSF is a broader, more comprehensive framework for risk management. This makes it more suited to broader cybersecurity governance and risk management. ATT&CK allows for focused, real-time threat detection, whereas CSF provides a long-term strategic framework for cybersecurity. |
| Attack Surface Management (ASM) | ASM is more focused on prevention rather than active defence, helping organisations manage vulnerabilities and entry points. Both complement each other. Specifically, ATT&CK helps detect active threats, whilst ASM works to reduce overall exposure. |
| CAPEC | MITRE ATT&CK provides more granular detail in terms of how adversaries implement specific techniques. In contrast, CAPEC is focused on the methodology of attacks, while ATT&CK addresses real-world behaviours and how they evolve. CAPEC is less focused on defence strategies, detection, and response, which are key strengths of ATT&CK. |
| VERIS Framework | VERIS is useful for quantifying and analysing incident data, making it more suited for post-incident analysis. ATT&CK helps actively improve defences by focusing on proactive threat identification. |
Each framework serves a distinct purpose and perspective to cybersecurity. In most cases, organisations can use them in combination to offer the most robust approach. Cybersecurity encompasses prevention, detection, response, and recovery. As such, only by using multiple frameworks can organisations address vulnerabilities, monitor threats, and develop incident response plans effectively.
The EMB3D™ Threat Model
The MITRE EMB3D™ Threat Model is a cybersecurity framework designed to protect embedded devices in critical infrastructure sectors such as energy, healthcare, and aerospace. Released in May 2024, it builds upon existing models like MITRE ATT&CK®, CWE, and CVE, with a specific focus on embedded systems security.
EMB3D provides a structured approach to identifying and mitigating cyber threats by categorising device properties, potential attack methods, and security measures. It defines device properties, including hardware, software, and network interfaces, and maps them to associated security risks. The framework also outlines threat properties, detailing how adversaries exploit vulnerabilities, the technical aspects they target, and the potential impact of their attacks.
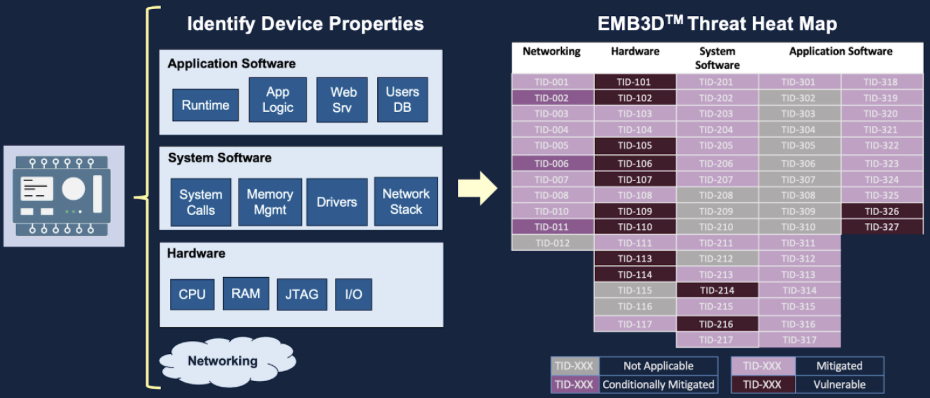
To help organisations strengthen security, EMB3D offers tiered mitigation strategies, categorised as Foundational, Intermediate, and Leading, based on their complexity and effectiveness. As an evolving, open-source resource, EMB3D enables manufacturers, asset owners, and researchers to collaborate on improving the security of embedded systems against emerging cyber threats.
Building your cybersecurity strategy

The MITRE ATT&CK framework offers a detailed, adversary-focused approach to help understand and counter cyber threats. By mapping real-world tactics, techniques, and procedures, the framework can help organisations to develop actionable threat intelligence, predict adversary behaviour, and enhance defences.
This intelligence-driven approach is critical for identifying and mitigating risks in real-time, streamlining incident response, and addressing gaps in security strategies. Whilst the strength of the ATT&CK framework lies in its practical application for threat detection and response, its integration into a broader strategy ensures organisations are well-equipped to anticipate, counter, and recover from evolving threats.
Learn more about the challenges of building a comprehensive cybersecurity strategy, and how to overcome them here.
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
