Threat actors often use techniques such as phishing, lateral movement, and zero-days to gain and maintain access to systems. The increased sophistication of advanced persistent threat (APT) groups compared to other attackers means that long-term infiltration, careful exfiltration of data, and manipulation of systems without detection is often observed.
Key characteristics of APTs
APTs are often state-sponsored or highly organised cybercriminal groups which aim to conduct espionage, data theft, or sabotage rather than attacks for immediate financial gain. These attacks typically follow a structured attack lifecycle, ensuring maximum effectiveness whilst minimising exposure:
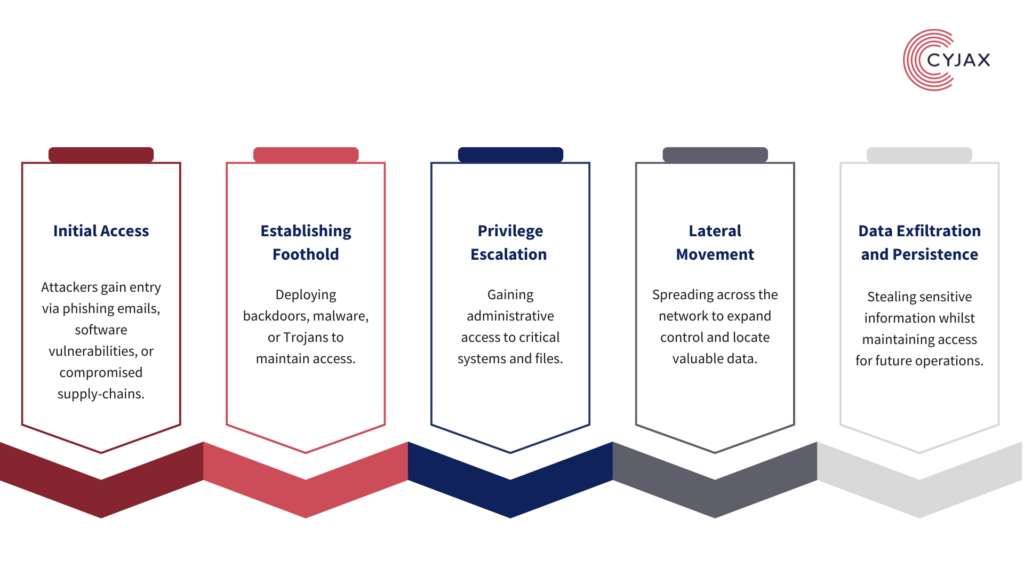
Real-world APT attacks
Dating back to the 1980s, one of the earliest examples of APT attacks involved a German spy working for the KGB who infiltrated US military and research networks. Known as the Cuckoo’s Egg, honeypots and network monitoring were used to track and eventually catch the perpetrator, following its initial discovery in 1986.
Since then, several groups have gained notoriety for their cyberattacks. APT29, also known as CozyBear, and APT28, or FancyBear, are both believed to be linked to Russian intelligence. Both APTs are known for conducting cyberespionage operations. APT28 is known for using spear-phishing and malware to compromise high-profile targets such as the World Anti-Doping Agency (WADA) and NATO. Similarly, APT29 was responsible for a targeted attack against the Democratic National Committee (DNC) in 2016. In this incident, the group infiltrated networks and stole sensitive political data.
Lazarus is another well recognised group which has been linked to North Korea and is responsible for multiple cyberattacks. This includes an attack against Sony Picture in 2014 and campaigns involving WannaCry ransomware in 2017. Meanwhile, a prominent example of cyber espionage against US defence, healthcare, and critical infrastructure sectors is DeepPanda, a Chinese group which has used techniques such as exploiting vulnerabilities in VPNs and cloud environments.
These incidents further highlight the adaptive nature of cybercriminals, who use increased precision and stealth to bypass traditional security measures.
Defending against Advanced Persistent Threats
A strong defence against APTs requires an intelligence-driven approach which integrates threat intelligence, proactive defence mechanisms, and automation. Threat intelligence can be used to provide early warnings and actionable insights, detecting threats through Indicators of Compromise (IOCs) such as malicious IPs and attack patterns. By analysing global threat feeds and dark web activity, threats can be identified before escalation occurs and swift responses can mitigate them.
Understanding tactics, techniques, and procedures (TTPs) can help security teams to anticipate attacker behaviour and strengthen defences. AI-powered monitoring can be used to detect network anomalies, reducing false positives whilst addressing real threats. Additionally, scanning dark web forums uncovers stolen data and planned attacks. This allows proactive threat hunting before significant damage can occur.
Threat intelligence also enhances incident response through Security Orchestration, Automation, and Response (SOAR) tools. These tools can be used to automate containment processes such as blocking malicious domains and isolating compromised devices. By integrating automation with intelligence-driven strategies, organisations can reduce the impact of an attack and stay ahead of evolving APT threats.

Tracking threat actors is a crucial component of an intelligence-driven defence. By continuously monitoring their activities, organisations can gain deeper insights into TTPs. Cyjax’s Threat Actor Tracking provides real-time intelligence on adversary behaviour, uncovering emerging threats before they escalate. Stay ahead of APTs with actionable intelligence. Find out how Cyjax can strengthen your security posture here.
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
