UK Election – The Hacktivism Perspective

By Jake Keast
Introduction
The UK General Election marks a monumental time in UK politics. There has been a lot of internal tension regarding the future of the Conservatives, with a large majority of individuals voting to ensure that the party did not continue its 14 years in power. On 5 July 2024, Labour won the General Election in a major landslide victory for the party, putting them in power for the first time since 2010. This general election marked one of the biggest events in the UK this year, and hacktivist groups have been observed taking a great interest in it.
Pro-Russian hacktivist response
The United Kingdom has been publicly supporting Ukraine in the Russia-Ukraine war, which has resulted in the country becoming a regular target of pro-Russian hacktivist groups. The United Kingdom is one of the largest donors to Ukraine alongside the United States and Germany, pledging a total of £12.5 billion since February 2022.
The country is regularly targeted by pro-Russian hacktivist groups who rotate targeting frequently, reacting to the changing geopolitical landscape. This has been proven with the activity of groups like NoName057(16), which focuses on specific countries in several day-long attack campaigns. These campaigns typically consist of distributed denial-of-service (DDoS) attacks against organisations within the targeted country. To publicly show its success within a DDoS attack, hacktivists often use a technique known as CheckHost reporting. These reports are service reports for a given website, meaning when a threat actor takes down a site it can use this outage report to suggest a successful DDoS attack within that period. It should be noted that CheckHost reporting is not definitive proof that a DDoS attack has occurred and is only an indication of the status of a website.
Cyjax monitors the dark web including Telegram for CheckHost reports. Below is a graph showing the percentage of CheckHost reports based in a given country between 4 and 5 July 2024, which aligned with the start of exit poll reporting.
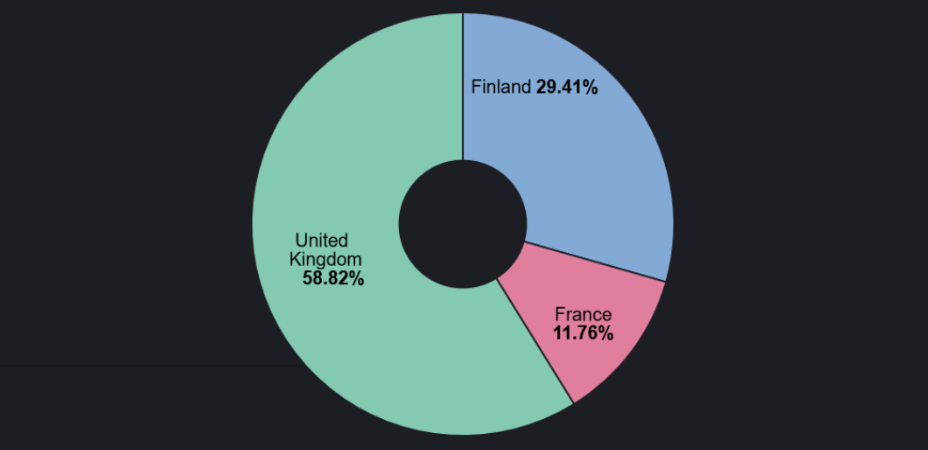
As shown, the United Kingdom accounts for 58.82% of total claimed DDoS attacks in the last 48 hours. For comparison, here is the targeting data for the monitoring period between 2 and 3 July 2024:
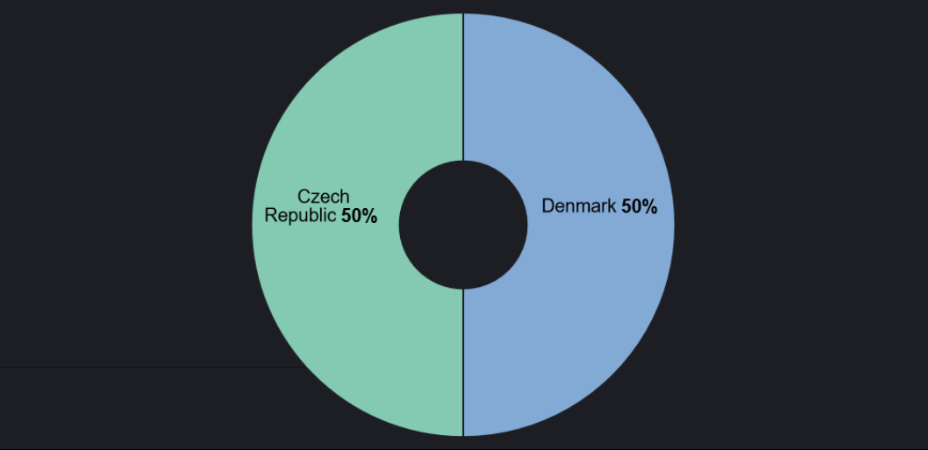
These graphs correlate to the reactionary nature of hacktivism and rotational targeting. This is a significant surge in targeting against the UK and a major shift in the overall targeting focus.
On 4 July 2024, Russian hacktivist group NoName057(16) put out a “call to arms” for hacktivist groups to attack the United Kingdom, which can be seen in Figure 3.
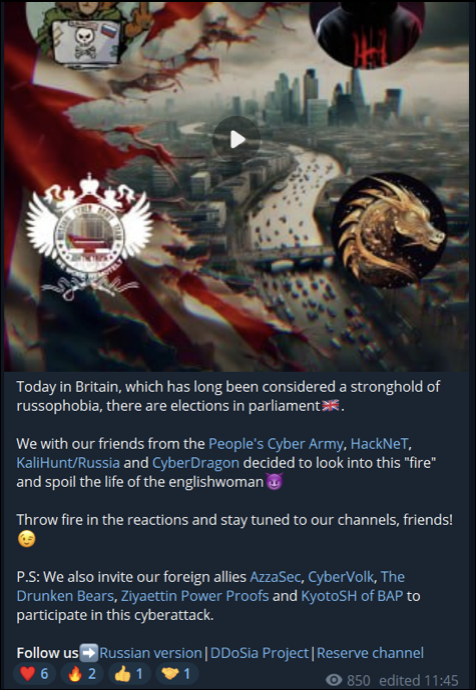
NoName057(16) has been building several alliances in the last few months. Before this post, Cyjax noted affiliations made with AzzaSec, CyberArmyOfRussia_Reborn, CyberDragon, and HackNet. This post confirmed the alliances, as well as the level of influence which NoName057(16) appears to hold over these groups. The groups, colloquially referred to as “friends”, appear to be of Russian origin. This post also confirms some of the foreign allies NoName057(16) has, including AzzaSec, CyberVolk, TheDrunkenBears, PowerProofZiy, and KyotoSH.
It should be noted that CyberArmyOfRussia_Reborn, also known as Narodnaya CyberArmiya or People’s Cyber Army, has believed ties to the state-sponsored group Sandworm.
Since this call to arms, several attack claims have been made against the UK. NoName057(16) has claimed attacks against West Yorkshire Metro, Swift Transportation for Birmingham, Confederation of British Industry, the Money Advice Service, and Leicestershire City Council websites.
HackNet followed suit after NoName057(16)’s public call to arms. The group claimed a DDoS attack against the Scottish National Party’s website. At the time of writing, this is the only claimed attack from HackNet.
CyberArmyOfRussia_Reborn also claimed an attack on the Electoral Reform site following NoName057(16). Whilst no more attack claims have been made, the group announced on 5 July 2024 that it intended to target London in the following days.
CyberDragon, CyberVolk, and KaliHunt have not announced any attacks at the time of writing. However, each group has expressed the intention to follow NoName057(16). TheDrunkenBears and AzzaSec have not publicly responded to the call to arms at the time of writing.
Pro-Palestinian hacktivist response
The United Kingdom has also been a target of pro-Palestinian hacktivist groups which react to news reports surrounding the UK’s decisions regarding aid given to Palestine. Cyjax monitoring suggests that pro-Palestinian groups have not currently responded to the UK general election, indicating a lesser degree of interest than their Russian hacktivist counterparts. This is likely as no explicit mentions of the conflict are present. The pro-Palestinian hacktivist movements also do not have the same level of organisation or cohesion as the Russian hacktivist scene, likely due to the stronger implications of state-sponsored ties within Russian hacktivism as opposed to the pro-Palestinian scene.
It is entirely possible that as the new party settles in and decisions are made on the ongoing conflict, these groups will react accordingly. However, as it currently stands, this area of hacktivism has not reacted.
Conclusion
As evidenced herein, NoName057(16) holds a significant level of influence over other groups within the Russian hacktivist space. Since the reporting of the UK General Elections and exit polls, Russian hacktivist groups have quickly responded with DDoS attacks against several targets within the United Kingdom to cause disruption. The rapid response times from groups like NoName057(16) as these major political events occur helps shape the image of each hacktivist. The purpose of hacktivism is to push an agenda through disruption as a means of forcing the general population to listen. Attacking the United Kingdom at a time of great political importance to the country creates publicity for the group, as it is more likely to be reported on. Hacktivism relishes on public reporting as it inadvertently gives the group more attention, meaning the message of the group is more likely to be heard.
The pro-Russian hacktivism alliances forming behind the scenes raise concern about the level of attacks which could occur in the future. As these groups band together to conduct future attacks, the campaigns will likely increase in diversity, strength and volume, posing a significant threat.
The next months see events of political importance across the globe including elections within Rwanda and Syria (15 July), Venezuela (28 July), Czechia (1 September), ALgeria (7 September), Jordan (10 September), Romania ( 15 September) and Austria (29 September). There will likely be a predictable trend for this quarter as many attacks will follow these political events. However, hacktivist groups will also opportunistically attack entities within those countries in the process, adding an element of unpredictability.
Rapidly growing alliances and quick response times to emerging reports of significant political events highlight the growing threat that organised hacktivism presents across all sectors.
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
Get Started with CYJAX CTI
Empower Your Team. Strengthen Your Defences.CYJAX gives you the intelligence advantage: clear, validated insights that let your team act fast without being buried in noise.
