Introduction
As 2025 progresses into its second week, it has not taken long for a new data-leak site (DLS) for an extortion group to emerge. December 2024 saw the emergence of LeakedData, FunkSec, and Bluebox. This week, the new group goes by the name Morpheus. Read on to find out what Cyjax knows about this new entrant into the extortion scene so far.
Key Points
- Cyjax has discovered a DLS for a new extortion group going by the name Morpheus, which is believed to have emerged on or prior to 12 December 2024.
- Via its DLS, Morpheus claims to have stolen data from two victims so far:
- Australia-based pharma Arrotex Pharmaceuticals on 12 December 2024
- Germany-based electronics manufacturer PUS GmbH on 20 December 2024.
- The group offers to sell data stolen from these allegedly impacted organisations, and buyers must contact the group by creating an account on the DLS.
- A security researcher has claimed that Morpheus deploys ransomware which is similar to the one used by the Hellcat extortion group.
- However, Cyjax has not identified definitive evidence that the group deploys ransomware, or any links between Morpheus and Hellcat.
Context
Extortion groups commonly use DLS to further extort victims, typically proceeding in multiple stages. The first threat is that the victim’s name and news of a successful attack against it will be published on the extortion group’s website. Should this fail to motivate a victim to pay a ransom, the group’s next step is typically to provide proof of the successful theft of its data, such as screenshots of internal file trees, samples of employee or customer PII, or other sensitive documents. The group may add a countdown at this stage, noting that should the victim fail to pay by the conclusion of the count down, it will make available to DLS visitors all stolen data, either for free or at cost. Cyjax continually tracks the emergence of new DLSs and has highlighted their increased rate of emergence in recent years.
Known locations
The Morpheus DLS consists of five main pages, only three of which are accessible to unlogged-in visitors. First is the landing page, where the group names organisations it claims to have attacked. This hosts descriptions of the victim, the information which Morpheus claims to have stolen, samples of the allegedly stolen data, and instructions for how to contact the group to purchase it. The other two pages visible to unlogged-in visitors facilitate creating an account on the DLS and signing into it. Registrants must provide a username and password and complete a human verification CAPTCHA challenge. Interestingly, visitors can also toggle night-mode on and off, making the site more user-friendly.
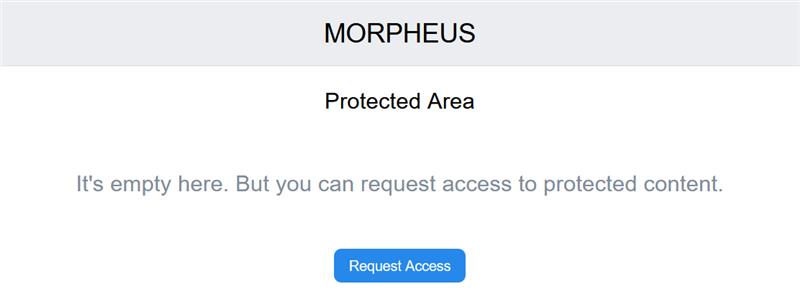
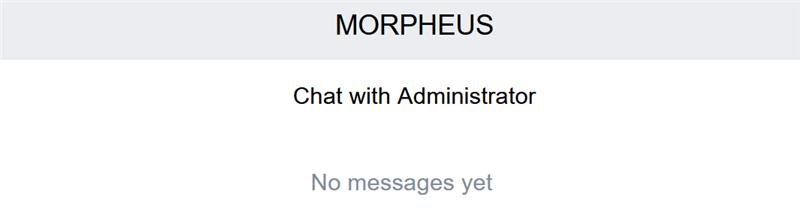
Upon signing in, users have access to two additional areas, namley ’Protected’ and ’Chat’ pages. Via the Protected page, users can request access to protected content. It is unclear to what this exactly refers, though it is likely that users can request download links for more samples of allegedly stolen data than is available via the Feed page. The Chat page appears to facilitate contact with the group’s administrator(s), likely for the purpose of negotiating payment for the advertised data.
At the time of writing, Cyjax has not identified Morpheus’ presence on prominent cybercriminal forums, social media platforms, or Telegram.
Victimology
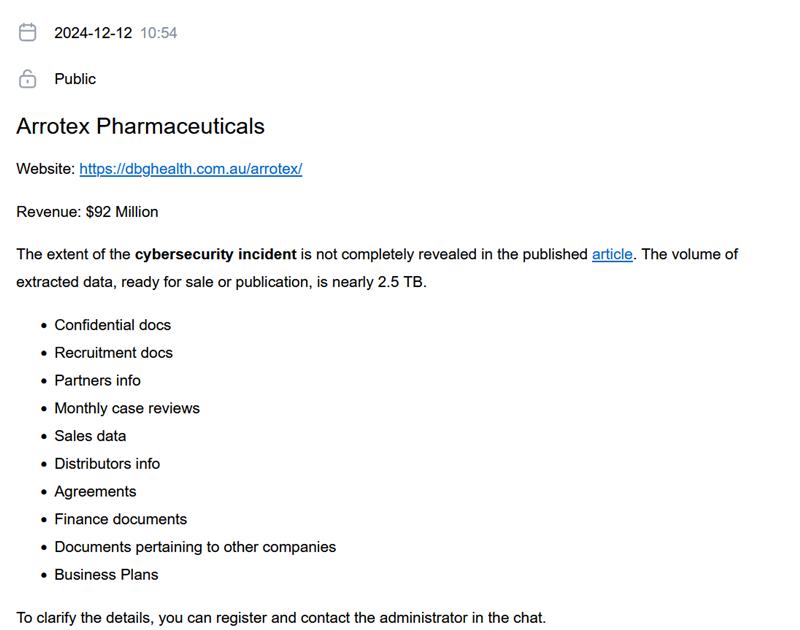
Morpheus has claimed to have stolen data from two victims so far. In a post which is dated 12 December 2024, the group claimed to have stolen 2.5TB of data from Australia-based pharmaceutical company Arrotex Pharmaceuticals, which has a reported revenue of $92 million. Morpheus claimed this data contained “Confidential docs”, “Recruitment docs”, “Partners info”, “Monthly case reviews”, “Sales data”, “Distributors info”, “Agreements”, “Finance documents”, “Documents pertaining to other companies”, and “Business Plans”. In the victim post, the group provided screenshots of samples of personally identifiable information (PII), file trees, and compliance documentation allegedly stolen from Arrotex Pharmaceuticals. Morpheus provided a link to a 29 October 2024 disclosure of a cybersecurity incident, which was released by DBH Global Enterprises Pty Ltd (DBG), of which Arrotex Pharmaceuticals is a business unit. The notice disclosed that on 25 August 2024, DBG “became aware that a malicious third party had obtained unauthorised access to a DBG storage server and had exfiltrated data from that server”. However, the notice did not name an attacker.
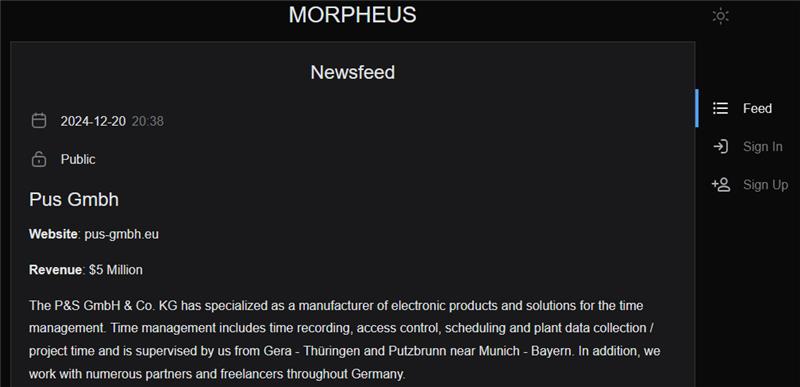
Subsequently, on 20 December 2024, Morpheus claimed to have stolen data from Germany-based electronics manufacturer PUS GmbH. This company has a reported revenue of $5 million. The group did not list how much data it claimed to have stolen, but claimed it includes “Technical and personal documents”, “Customer database [sic]”, and “Backups of customer databases”. In its victim post, Morpheus shared samples of the allegedly stolen data that included PII, invoices, and HTTP server configuration data. At the time of writing, PUS GmbH has not acknowledged any recent cyber incidents.
Associations
One security researcher assessed on 7 January 2024 that Morpheus is linked to the Hellcat ransomware group. Cyjax could not confirm the validity of this claim due to a lack of corroborating evidence. Additionally, a representative of the Hellcat group dismissed the claims, writing “nothing relate us to any other ransomware group [sic]”. It is of note that Morpheus makes no reference to ransomware or encryption on its DLS. As such, Cyjax does not believe that the group operates as a ransomware operation at this time.
Threat Assessment
Morpheus is a very new data-extortion group which has claimed responsibility for attacks against two organisations, one of which is partially confirmed. The group maintains a well-functioning DLS where it has shared samples of allegedly stolen data.
To access our full intelligence repository containing detailed profiles like this one, covering extortion groups, advanced persistence threat groups (APTs), data brokers, hacktivists, initial access brokers, and more, click here to take a test drive of CYJAX.
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
