Just days after Cyjax observed the emergence of a data-leak site (DLS) for new extortion group Kairos, DLSs for two more new English-speaking groups, Chort and Termite, have debuted.
Key takeaways
- Tor hosted data-leak sites (DLS) have emerged for new ransomware and data leak extortion group Chort and new extortion group Termite.
- A sample related to Chort’s ransomware was observed on 21 October 2024, with the group naming victims on its DLS on 29 October.
- Chort has named six victims so far and has mainly targeted the US education sector, with two victims confirming network disruption in late September and early October.
- Chort’s TTPs likely include running PowerShell commands for execution and to avoid detection, as well as deleting shadow copies to inhibit recovery.
- Termite is a data extortion group that allegedly steals data from its victims and threatens to publish them on its DLS if a ransom is not paid.
- It has so far named five victims on the DLS, which are based in the US, France, Oman, Germany, and Canada.
- Though Termite is yet to release any sensitive data, one organisation the group claims to have attacked confirmed that it experienced a cyber incident in mid-October 2024.
Chort
History
Chort, which means “Devil” in Russian is also known as ’Chort RS Group’, ‘Chort Ransomware’, and ‘ChortLocker’. It is a ransomware group which practices double extortion, exfiltrating sensitive data from its victims before encrypting files and directories. It demands a ransom for the decryption and safe return of stolen data.

Figure 1 – Chort Ransomware Blog homepage.
The group has likely been in operation since at least September 2024, with some victims declaring cyber incidents that month. Based on the date of the earliest victim posts on the Chort DLS, the site was created on 29 October at the latest. The group created its Telegram channel on 15 November, which at the time of writing, has roughly 30 subscribers.
Victimology
At the time of writing, Chort has named six organisations on its DLS at the time and has mainly targeted the US education sector:
- US-based educational organisation Texas Can Academies.
- US-based educational organisation Edwardsburg School Foundation.
- US-based manufacturer Tri-Tech Electronics.
- US-based Bartow County School System.
- Kuwait-based Public Authority of Agriculture Affairs & Fish Resources (PAAF).
- US-based Hartwick College.
Of these victims, Chort has made data for Tri-Tech Electronics, Bartow County School System, and PAAF freely available for download for visitors to the DLS. Hartwick College is “awaiting decision”, which likely means that the group is currently awaiting or engaged in negotiations surrounding payment of a ransom. However, Cyjax cannot currently confirm this.
Two victims have publicly announced that they have suffered cyber incidents. On 30 September 2024, the Edwardsburg School Foundation stated it had suffered a “network outage” that lead to classes being cancelled. On 18 October, Bartow County School System announced that it had suffered a week-long outage following an attempted by “an unauthorised external source” to access part of its “information systems”. Neither statement listed the identity of the alleged attacker. As such, Cyjax cannot currently confirm that these incidents are related to Chort’s claims.
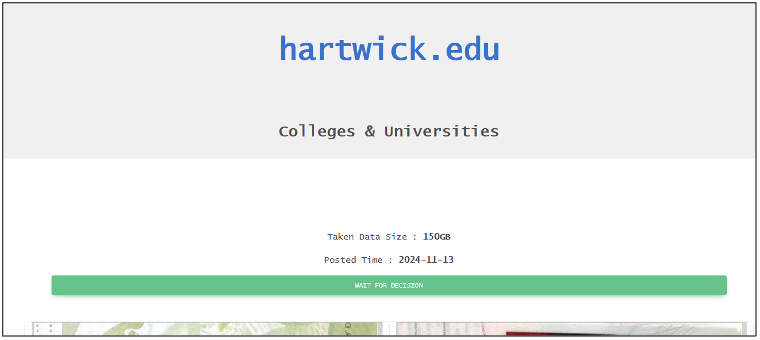
Figure 2 – Chort victim page for Hartwick College.
Motivation
Chort appears to be principally financially motivated, having posted no political or social manifesto or set of rules, and listing its victims as simply “companies [who] wouldn’t want to be safe [sic]”.
Known locations
Chort maintains an English-language DLS. The homepage includes a list of victims which Chort claims to have compromised. Clicking on the logo of the organisation redirects to a specific page for it, detailing its industry sector, amount of data allegedly stolen, and the time at which Chort named the victim on its DLS. For two of the “published” victims, Chort has also embedded images of personably identifiable information (PII), invoices, and other financial documents as proof of the stolen data.
The site functions well and has a numerical CAPTCHA challenge on most pages. A “CONTACT US” page lists the group’s contact details for Tox, Jabber, and Telegram. The Telegram channel duplicates content from the DLS, to which it also hosts a link.
At the time of writing, Cyjax has not identified any significant discussion or adverts for Chort on prominent cybercriminal forums.

Figure 3 – Chort’s Telegram channel.
Tactics, techniques, and procedures (TTPs)
Although Chort is a new group, Cyjax has identified a public sandbox analysis of a PowerShell script which was uploaded on 21 October 2024 and may give insights into the group’s TTPs.
This script, known as ‘AcWinRT.ps1’, contains references to the creation of a registry key, which causes all files with a “.CHORTLocker” extension to have a default icon. It is likely that AcWinRT.ps1 is a component of the wider Chort ransomware used to conduct specific operations to aid successful execution. Though this public analysis did not contain references to the file that would conduct the encryption and append the .CHORTLocker extension to files, this cryptoviral activity would likely come after the execution of the public script. As such, Cyjax is referring the wider malware, including the executable responsible for encryption, as CHORTLocker.
Following the change of registry keys, AcWinRT.ps1 executes the ‘acwinrt.exe’ file. It is interesting to note that this executable is referenced in analysis of other malware, including NukeSped and LOKI. At the time of writing, it is unclear whether acwinrt.exe is available as an off the shelf tool, allowing unrelated threat actors to acquire it, or whether Chort, NukeSped, and LOKI have any closer connections.
The acwinrt.exe executable then runs a PowerShell script titled ‘APP01.ps1’ which subsequently runs nine other PowerShell scripts, each following a similar naming convention. Across these scripts, several malicious activities are conducted. This includes scripts bypassing execution policies, running invisible windows, modifying the registry and access control lists, and hiding prompts from users. Some more notable actions the scripts take include repeatedly disabling Windows Defender and deleting shadow copies, a common technique used by ransomware to inhibit recovery.
IOCs for ChortLocker have been included at the end of this report.
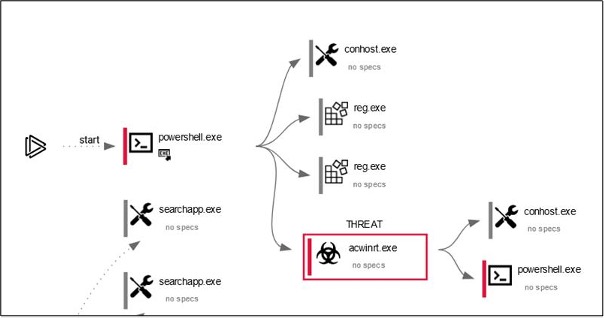
Figure 4 – A section of the “AcWinRT.ps1” behaviour graph (Source: AnyRun)
Threat assessment
Chort has claimed attacks against a reasonable number of victims during its short period of activity, two of which have confirmed that they suffered cyber incidents. It has shared allegedly stolen data from its victims in the form of large files to download and screenshots of PII. Analysis of the Chort script suggests that the group can successfully evade defences and inhibit recovery.
Termite
History and Victimology
Termite is an English-speaking extortion group which allegedly steals data from organisations, threatening to leak this on a TOR-hosted DLS unless a ransom is paid. From analysis of the date of the earliest posts on the DLS, Termite emerged on or prior to 12 November 2024. It has so far claimed attacks against five victims which span a range of geographies and industry sectors:
- US-based auto-parts supplier Nifast Corporation.
- France-based water treatment company Culligan France.
- Oman-based oil company OQ.
- Germany-based NGO Lebenshilfe Heinsberg.
- Canada-based education organisation Conseil Scolaire Viamonde.
Termite has yet to share any data allegedly stolen from these named companies. However, Conseil Scolaire Viamonde confirmed that it suffered a cyber incident on 17 October 2024 which caused disruptions to its IT systems. Currently, Cyjax cannot confirm whether these are related.

Figure 5 – Termite DLS homepage.
Motivation
Similar to Chort, Termite appears principally financially motivated, having posted no political or social manifesto or set of rules. The DLS’s Support page reads “We are ready to help you!”, suggesting that the group may attempt to masquerade as a legitimate penetration testing operation.
Known locations
Termite maintains a well-functioning English-language DLS. The homepage names a list of victims which the group claims to have compromised. Clicking on the logo of the organisation redirects to a specific page for it, which hosts a more detailed description. At the time of writing, the group has not yet made publicly available any data stolen from its alleged victims. A support page hosts a form for contacting the group. It has an input box for “your support token”, which the victim likely receives following an attack. Aside from this, the group has not shared any contact details.
At the time of writing, Cyjax has not identified any significant discussion or adverts for Termite on prominent cybercriminal forums.
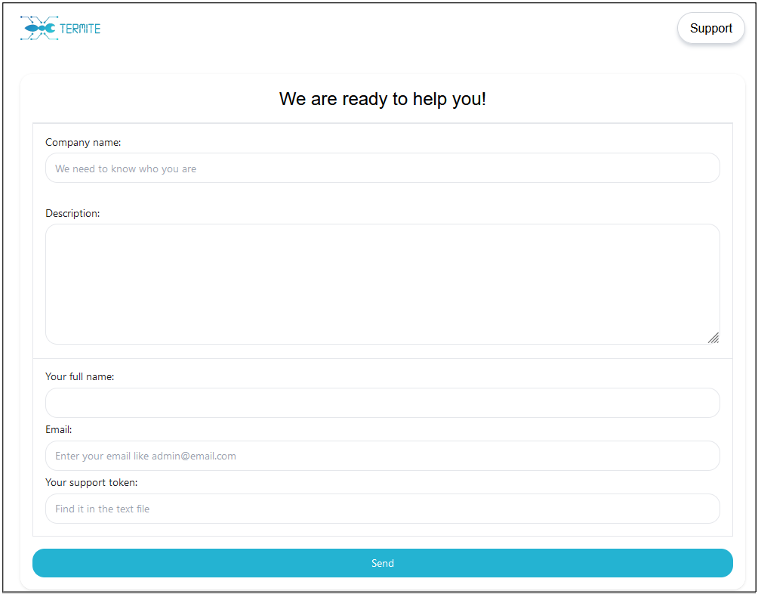
Figure 6 – Termite DLS Support page.
Tactics, techniques, and procedures (TTPs) and Associations
At the time of writing, Cyjax has not identified any known TTPs for Termite or any associations it may have with other groups.
Threat assessment
Termite has claimed a moderate number of victims during its short period of activity. TTPs for the group are so far unknown, and Cyjax cannot assess the group’s level of technical capability. Termite has not yet offered proof for any of its claims, though one victim has announced an incident which matches the timeframe of the attack the group has claimed.
Concluding remarks
Chort and Termite are the latest in a long list of extortion groups that have released DLSs this year, with five new sites emerging in November 2024 alone. This continues the trend of a higher rate of emergence in recent years, which Cyjax reported on in May and August 2024. As the ransomware and extortion group ecosystem continues to expand and mature, Cyjax expects more DLSs to emerge over the short and long-term, as well as an expansion of the market that supports them, including initial access brokers. Cyjax continuously monitors groups and threat actors across the open, deep, and dark web, providing customers with better answeers, faster.
IOCs
Chort
- Extension: .CHORTLocker
- Filename: AcWinRT.ps1
- Filename: acwinrt.exe
- Filename: APP01.ps1
- MD5: 764C43128170E2762E2B5B8D5FB89800
- SHA1: 31E232F33AC925B25B26989E0D41667503ED8E65
- SHA256: 2EC59B8763ADC00F41E18D05C25B425BD212AE788CC00EDA99E9C0CEC5FC2D1E
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
