Stealer Malware and Stealer Logs Explained

Stealer logs and the infostealers that harvest them form a key part of the threat landscape and cybercriminal ecosystem. Infostealers, which are also referred to as stealer malware, are deployed by threat actors to facilitate data theft from compromised devices. This data typically contains sensitive and valuable personal information including credentials, hardware or software information, IP addresses, browser cookies, and more. Attackers can then use logs from stealer malware in their own attacks or sell it on established stealer log marketplaces. This introductory blog provides insight and overview of infostealers and the logs they harvest, exploring how the malware strains work, what logs contain, where they are sold, and what attackers can do with them.
What are infostealers?
Description
Infostealers are strains of malware that once deployed on victim devices, are designed to harvest sensitive data from the device whilst remaining undetected.
This data is often staged and then exfiltrated to attacker-owned infrastructure, allowing threat actors to use the information for further malicious activity. This may include financial fraud and identity theft. Alternatively, threat actors may choose to sell logs of the malware as raw information outputs from the infected device. Whilst one set of credentials is valuable to cybercriminals, when bundled with other infected devices and accounts, logs can become extremely highly valued. This is because they contain significant amounts of personal data that can be maliciously repurposed to fully impersonate a victim online.
Common stealers
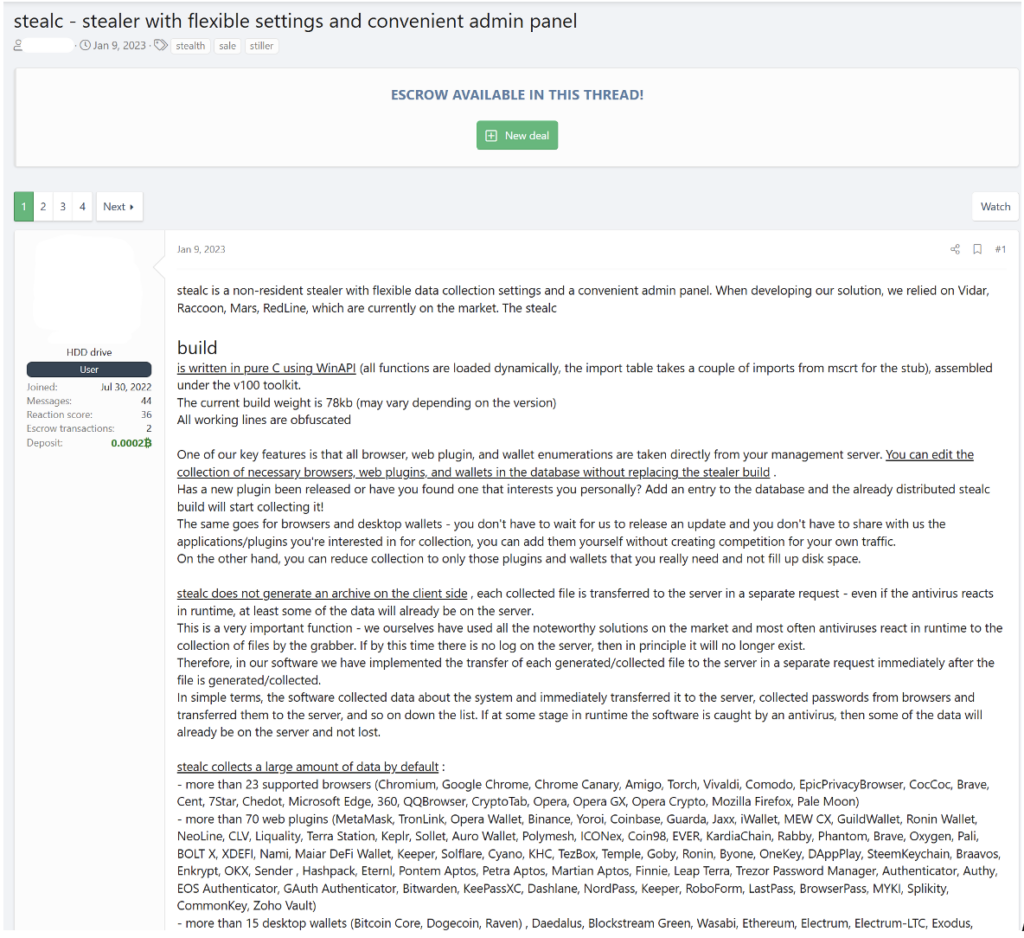
Commodity malware strains are often available for sale on hidden services such as cybercriminal forums and vary widely in capabilities and prices. Notable examples of these strains include Redline and Vidar. Many vendors operate under the Malware-as-a-Service (MaaS) model, in which access to the malware is available on a monthly or yearly subscription basis, with differing levels of access.
While there are many active stealer strains, with some vendors offering profit shares for use of their own ’native’ stealers, the main commercially available malware strains are Redline, Lumma, Stealc, Risepro, Vidar, and Racoon.
Redline
Redline is a stealer used to harvest login details, cookies, and other personally identifiable information (PII) by threat actors, which is often later sold on darknet log markets. The stealer is often distributed through cracked software and games. Redline is also used to collect information on victims’ PCs such as running processes, antivirus products, installed programs, the Windows product name, and more. The stealer maintains persistence through Windows tools found on the device. Stolen data is converted to XML format and exported via SOAP messages.
Vidar
The Vidar infostealer was first identified in 2018 and has since become popular among threat actors. Vidar is thought to be a variant of the Areki malware family, which includes other infostealers such as Mars and Oski.
The malware is used to harvest diverse types of information including banking details, passwords, IP addresses, browser history, login credentials, and crypto wallets. Information stolen by Vidar Stealer is most often used for fraudulent activity.
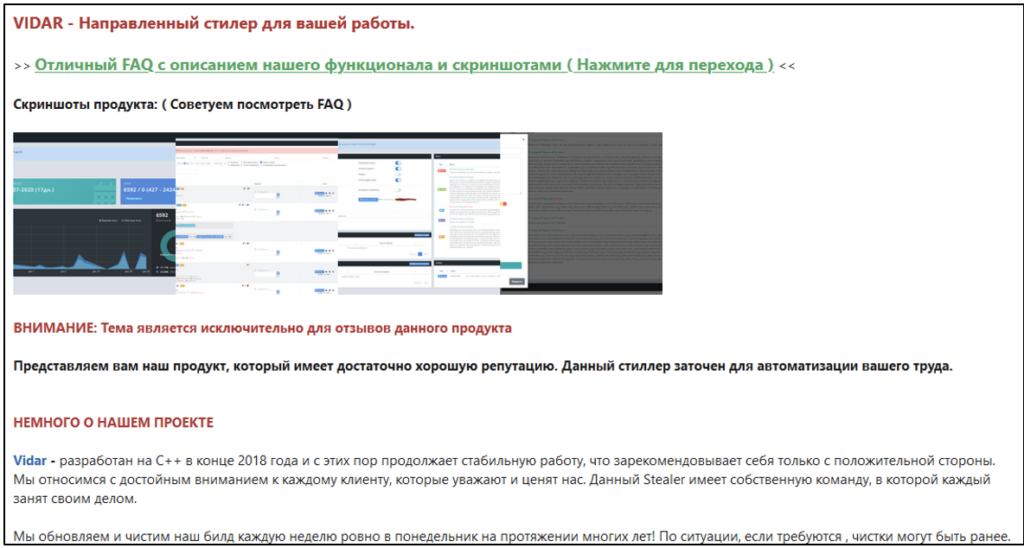
Partial translation from Russian:
“VIDAR is a directional stealer for your work.
>> Excellent FAQ with a description of our functionality and screenshots (Click to go) <<
Screenshots of the product: (We recommend you look at the FAQ)
ATTENTION: The theme is exclusively for reviews of this product
We present to you our product, which has a fairly good reputation. This stealer is designed to automate your work.
A little bit ABOUT OUR PROJECT
Vidar was developed in C++ at the end of 2018 and has been working steadily since then, which proves itself only on the positive side. We treat every customer with decent attention, who respect and appreciate us. This Stealer has its own team, in which everyone is busy with their own business.
We have been updating and cleaning our build every week on Monday sharp for many years! According to the situation, if required, cleaning may be earlier.”
What are stealer logs?
Stealer logs are collections of information which have been harvested by stealer malware. They often contain personal or sensitive information from infected devices. Information in such logs may include usernames, passwords, browser data such as history and cookies, email addresses, additional user information, and further details from documents, clipboard data, Intellectual Property, MAC addresses, and installed software.
Stealer logs are often combined with each other or different leaks that may not be stealer logs. This creates large datasets named combolists, which contain a mix of lines from different campaigns or stealer malware strains to increase the value of sale.
It is important to note that logs typically contain everything an attacker needs to authenticate as the victim. They may even have credentials to access password stores and other sensitive areas and documents to allow attackers to pivot and gain further access. In the case that a machine is infected with stealer malware, the resulting impact may be immense due to the range of malicious activity that can be conducted using its logs.
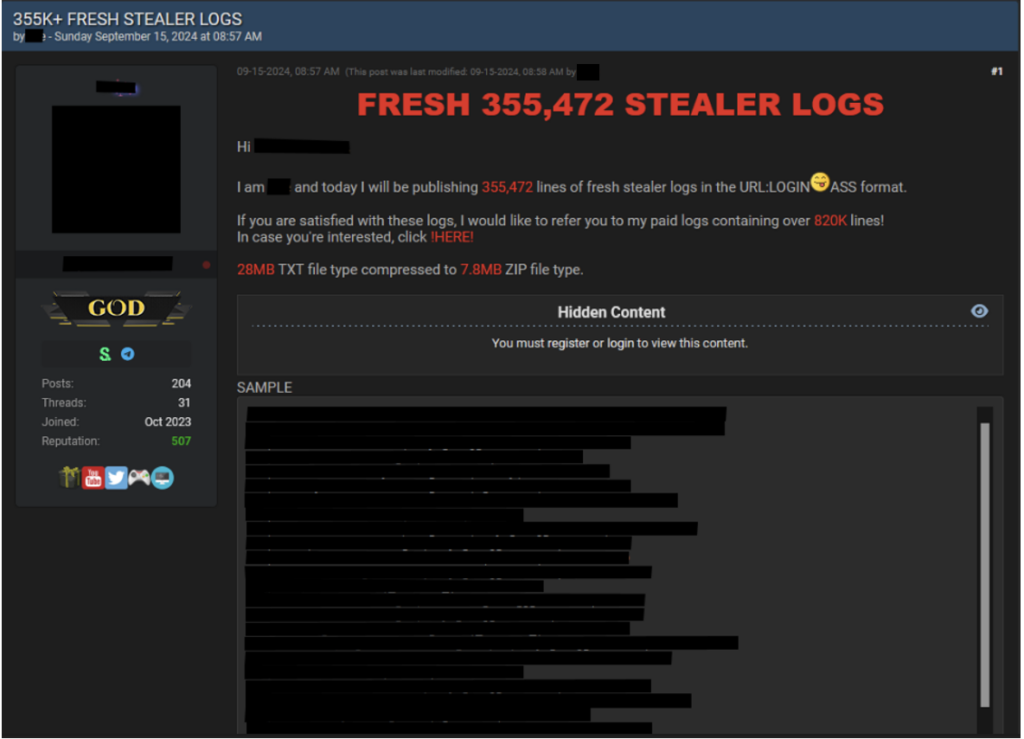
In the below screenshot of a listing post on a prominent cybercriminal forum, a sample was provided showing the format of the logs. In this instance, the description shows that the log format was “URL:LOGIN:PASS”, though the “:P” erroneously formed an emoji. This would appear in the logs as ‘organisationName.com:username:password’. With one entry per line, this would provide 355,472 login credentials to different websites. These logs have been cleaned, meaning all other information collected by the stealer has been removed and credentials for URLs have been left. The logs are also fresh, indicating that they are first source and not old or reshared by the original poster.
Where stealer logs are found
Stealer log marketplaces
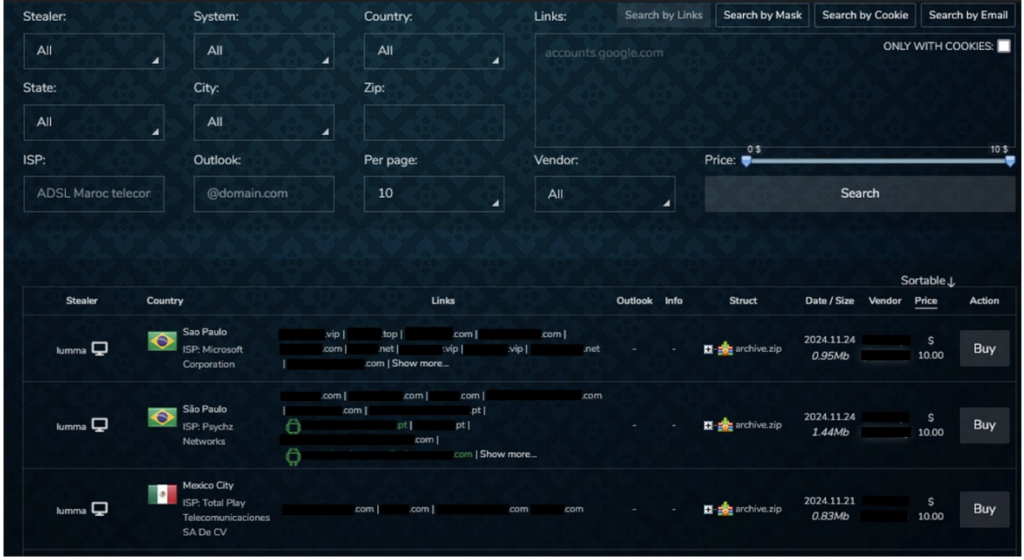
There are both Clearnet and Tor-based sites which are used to host markets for stealer logs. Centralised markets allow users to list logs for sale whilst allowing prospective buyers to use search functions to prove value of sale and potentially increase successful monetary gain. As seen in Figure 5, marketplaces can have highly customisable search settings, allowing visitors to filter for specific logs from particular vendors, malware strains, ISPs, and geolocations.
Cybercriminal forums
Cybercriminal forums facilitate markets for threat actors to sell stealer logs. Log sizes vary widely on these forums, from thousands to millions and occasionally billions of lines, each commonly containing URLs, logins, and passwords. While many are for sale, logs are sometimes available through spending a small amount of forum credits. Occasionally, they are posted for free to potentially allow many different threat actors to access the logs and conduct attacks against a wide range of users. Consequently, the original attacker gains credibility and a positive reputation.

Telegram
Many forum users also advertise their own Telegram contacts, groups, and channels dedicated to stealer log leaks and sales. The channels, which are often advertised via cybercriminal forums, often work as a subscription service in which buyers purchase access to a private channel or ‘logs cloud, where stealer logs are made available to view.

Telegram is often used as a command and control (C2) server to receive logs directly from active malware. This potentially further commercialises the logs as threat actors may sell direct access to these servers and facilitate real-time collection and abuse of information.
Cloud logs
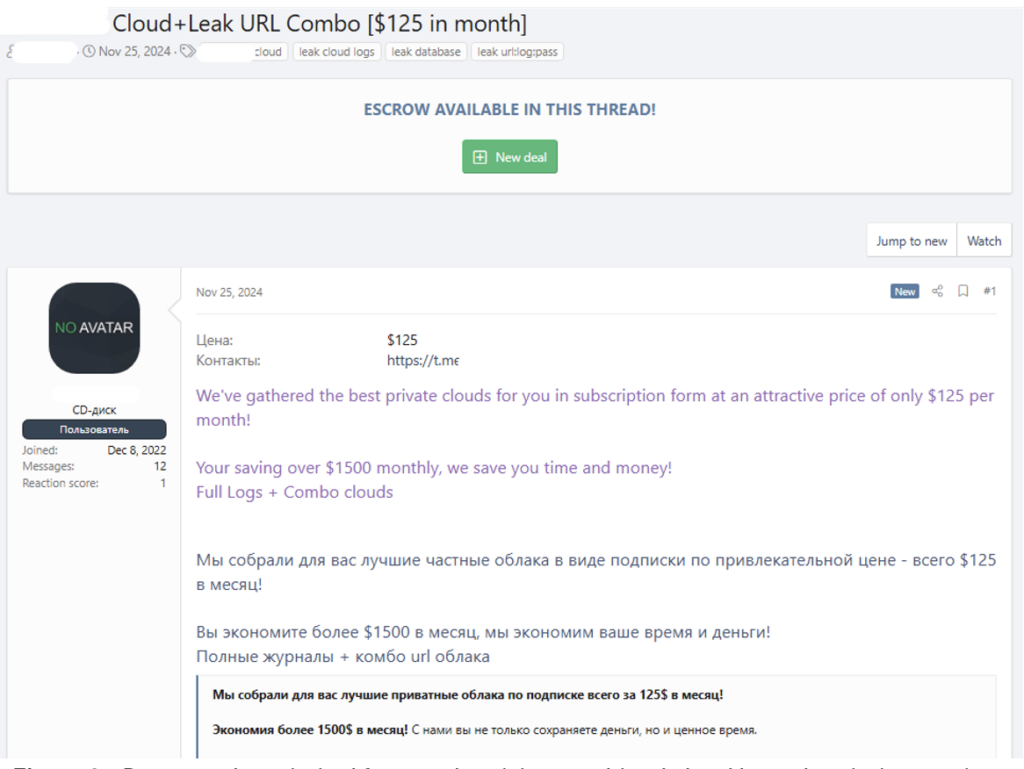
Cloud logs are services often offered under a subscription model which contain stealer logs hosted on cloud services or private online spaces. Whilst direct access to the C2 is not often provided, separate storage areas are used to provide an exploitable resource for extra monetary gain.
As seen in Figure 8, cloud log subscribers may choose to leak or advertise logs to forums behind a credit wall or other subscription cost to increase reputation and monetary gain. However, these are no longer fresh and so there is a lower chance that the logs are active and useful for malicious activity.
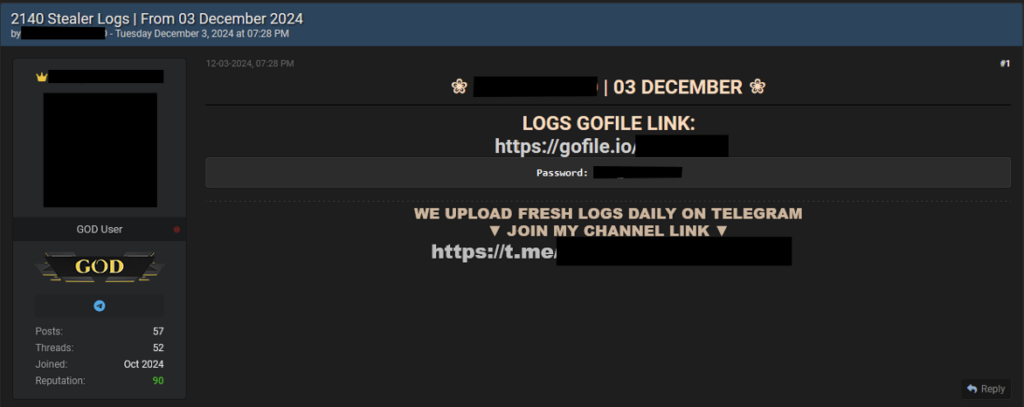
Logs are also often upload to cloud storage and file distribution sites such as gofile.io for easy distribution and avoidance of owned infrastructure detection and attribution. As seen in Figure 9, a forum user has advertised free logs and their Telegram channel which allows access to more logs.
How logs are used
Logs can be used in many ways and are often cheap for threat actors to purchase, typically costing $10 per infected machine. The main impact for victims is that their personal information is exposed and can be utilised in malicious activity.
Personal access
A common form of stealer log abuse is financial fraud. If the logs contain an individual’s credentials to an online banking platform, a threat actor can impersonate the victim and withdraw funds from any active accounts, take out loans, and create more accounts under the victim’s name. As some stealers can also steal cryptocurrency wallet data, including seed phrases, it is also possible to conduct cryptocurrency theft.
Users often reuse credentials across accounts and as such, credentials from one URL may be the same for others. Consequently, attackers can attempt to log in to different services using the same credentials or variations, potentially compromising more than what was originally stolen.
Personal and professional extortion
Personal information can also be used in phishing attempts, as there may be sufficient information to masquerade as the victim to target other individuals. An attacker may also attempt to masquerade as a service the victim is known to use to further extort them.
Logs may also portray the victim’s private activity, providing a potential avenue for blackmail. A threat actor with log access may be able to extort the victim for access to their employer organisation, through the threat of leaking this private activity. This is a form of insider threat and can be particularly impactful to both the victim individual and the targeted organisation.
Direct enterprise access
Finally, there is a threat to companies where the victim is employed. If credentials are reused between personal and professional accounts, a threat actor may be able to gain access to the employer organisation. Alternatively, credentials to the organisation may have been included in the logs if accessed from the infected device. Once such access is gained, the attacker can masquerade as the victim using exposed IP addresses and browser cookies to appear as a legitimate employee.
Many organisations employ BYOD (bring your own device) policies to allow personal devices to connect to enterprise networks and increase connectivity. However, this exposes another initial access vector if these devices are compromised by stealer malware. Cyjax observes this occurring frequently and is evidenced in listings on logs marketplaces.
Threat actors can search log marketplaces, forums, and Telegram channels for particular domains to identify infected machines to authenticate on these domains. If the relevant logs are found, the attacker could gain access to the targeted organisation.
This could potentially expose critical and sensitive enterprise information, Intellectual Property (IP), and data that can be used in supply-chain attacks.
Initial Access Brokers (IABs) sell initial access to organisations through protocols such as RDP and VPN, often through valid credentials. This access is often derived from stealer logs and portrays yet another avenue of commercialisation. Additionally, malware can be deployed inside the organisation’s network, particularly ransomware.

So what?
Stealer malware and logs pose a significant threat not only to affected individuals, but also to organisations due to the potential abuse of exfiltrated data. For example, an attack chain can begin when an employee’s personal device is infected with stealer malware. The resulting logs, including credentials and posture for logging onto enterprise portals, are sold and shared to other threat actors, creating an avenue for initial access to the organisation. This access could then be abused to deploy ransomware.
If an organisation uses BYOD policies or employees reuse their work passwords on their personal devices, it is vital to have visibility into the organisation's stealer log exposure to ensure that the threat can be proactively mitigated.
If you're interested in assessing your organisation's exposure to stealer logs or need expert guidance on proactive threat management, click here to get in touch with Cyjax.
Take action today to protect your business from the evolving cyber threat landscape.
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
Get Started with CYJAX CTI
Empower Your Team. Strengthen Your Defences.CYJAX gives you the intelligence advantage: clear, validated insights that let your team act fast without being buried in noise.
