Another week, another extortion group data-leak site emerges.
Cyjax has continued to observe the emergence of data-leak sites (DLSs) for extortion and ransomware groups. New groups FunkSec, ContFR, Argonauts, Kairos, Chort, and Termite appeared in December and November 2024 alone, bringing this year’s total up to 69. On 11 December 2024, Cyjax identified the emergence of a Tor-based DLS belonging to a new data-leak extortion group going by the name ’Bluebox’. This group has claimed just two victims so far. Its name likely derives from the phreaking tool of the same name that was popularly used for circumventing charges for long distance calls in the 1960s and 1970s.
Read on to find out what Cyjax knows so far about this new threat group.
Context
Extortion groups commonly use DLS to further extort victims, typically proceeding in multiple stages. The first threat is that the victim’s name and news of a successful attack against it will be published on the extortion group’s website. Should this fail to motivate a victim to pay a ransom, the group’s next step is typically to provide proof of the successful theft of its data, such as screenshots of internal file trees, samples of employee or customer PII, or other sensitive documents. The group may add a countdown at this stage, noting that should the victim fail to pay by the conclusion, it will make available to DLS visitors all stolen data, either for free or at cost.
Known locations
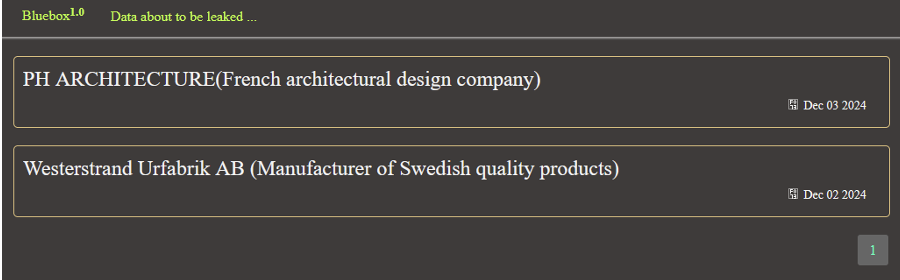
Emerging in early December 2024, the Bluebox DLS is minimalistic and consists of two main pages. The home page hosts a list of victims from which the group claims to have stolen data. Clicking on victim names directs to a specific page for each one. This page provides a description of the victim, the size, description, and filenames of the allegedly stolen data. Additionally, it also includes links for downloading samples of the data. A countdown indicates the remaining time victims have to pay a demanded ransom, after which the group claims it will release the full stolen dataset.
Elsewhere, a “Data about to be leaked” tab simply links back to the main page. The site contains footers and, unusually for a DLS, does not list any contact details. As of 11 December 2024, Cyjax has not identified accounts on other platforms such as cybercriminal forums or Telegram that are likely operated by the same entity.
Victimology
So far, the group has claimed attacks against two victims:
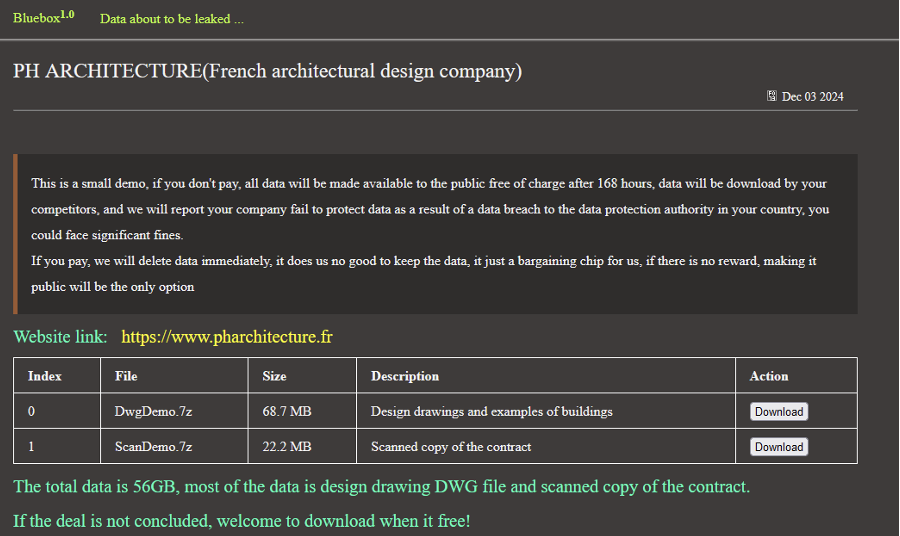
- Small France-based architectural design company PH Architecture.
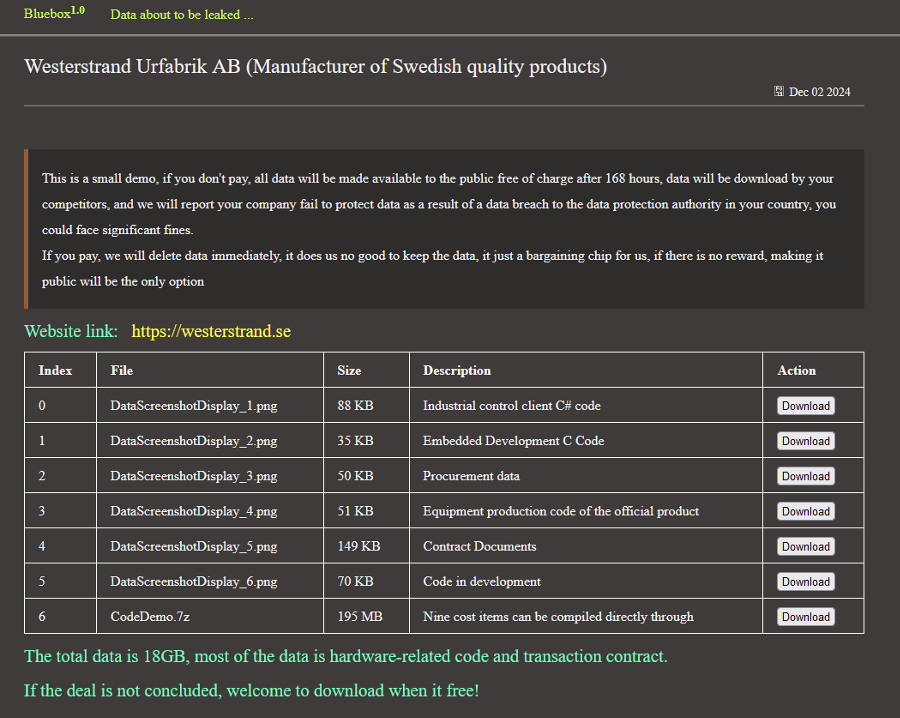
- Medium-sized Sweden-based time systems manufacturer Westerstrand Urfabrik AB.
The relevant posts for these victims list the dates as 2 and 3 December 2024, respectively. However, it is unclear whether these dates refer to when Bluebox named these victims on its DLS or when an attack occurred. Bluebox claims it has exfiltrated 56GB of data from PH Architecture and 18GB from Westerstrand Urfabrik AB. This data allegedly contains intellectual property, including source code and design blueprints, personally identifiable information (PII), contractual documents, and procurement information. The group states that should the victims not comply with its ransom demands, it will make this data freely available for download to visitors of the DLS. As of 11 December 2024, neither alleged victim has publicly acknowledged any recent cyber incidents.
Motivation
The group has so far indicated only financial motivation. It has not published any manifesto detailing its goals or ascribed geopolitical ideology. In its posts, Bluebox has promised to alert data protection authority in the victim’s country to further pressure them into paying a ransom. The group promises to delete the victim’s data following successful ransom payment, noting “it does us no good to keep the data”. Given the lack of references to encryption on the Bluebox DLS, Cyjax does not believe that the group operates as a ransomware operation at this time.
Tactics, techniques, and procedures (TTPs) and Associations
As of 11 December 2024, Cyjax has not identified any known TTPs for Bluebox or any associations it may have with other threat groups.
Threat assessment
Bluebox has claimed attacks against one small and one medium-sized business. It is realistically possible that the group has conducted additional successful attacks which it has not disclosed due to victims paying the ransom in the first instance. None of its claimed victims have publicly confirmed the legitimacy of any breaches. Bluebox operates a well-functioning but basic DLS. There are currently no known TTPs associated with the group, and so it is unclear to what extent it is technically capable. As such, it is not presently clear to what extent Bluebox presents a significant or credible threat.
To access our full intelligence repository containing detailed profiles like this one, covering extortion groups, advanced persistence threat groups (APTs), data brokers, hacktivists, initial access brokers, and more, click here to take a test drive of Cymon.
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
