Kairos extortion group turns to initial access brokers

Cyjax recently identified a new financially-motivated extortion group going by the name Kairos, which shares data stolen from its victims on a data-leak site (DLS).
An alleged spokesperson for the group, named ‘KairosSup’ made a bid on an initial access broker (IAB) listing on a prominent Russian-language cybercriminal forum. It is of note that the spokesperson’s name is likely styled after the representative of prolific ransomware group LockBit, who is called ‘LockBitSupp’. IABs are threat actors that gain an initial foothold in corporate networks which they sell on to other threat actors, including ransomware groups, APTs, and data brokers.
This provides a simple and effective way for extortion groups to gain access to organisations, perform reconnaissance, and exfiltrate sensitive information for ransom. IABs both lower the barrier of entry to cybercrime and specific organisations, whilst also increasing speed and efficiency of attacks.
This observation indicates that Kairos likely purchases these accesses to conduct its attacks.

Figure 1 – IAB listing for Canada-based organisation which Kairos sought to buy.
On 13 November 2024, an IAB initiated a Russian- and English-language thread on a prominent Russian-language cybercriminal forum titled “Access to VPN Forti Canada 6.9KK Admin” (partially translated from Russian). In their initial post in the thread, the broker advertised VPN access to an unnamed Canada-based construction organisation with a revenue of $6.9 million and 51 employees. The broker listed the access under the auction format, in which there was a starting price of $1,000, subsequent bids at $200 increments, and a blitz price of $2,000 to bypass the auctions process.
The broker then replied to the thread and decreased the prices, after which KairosSup made a starting bid of $500 on 15 November.
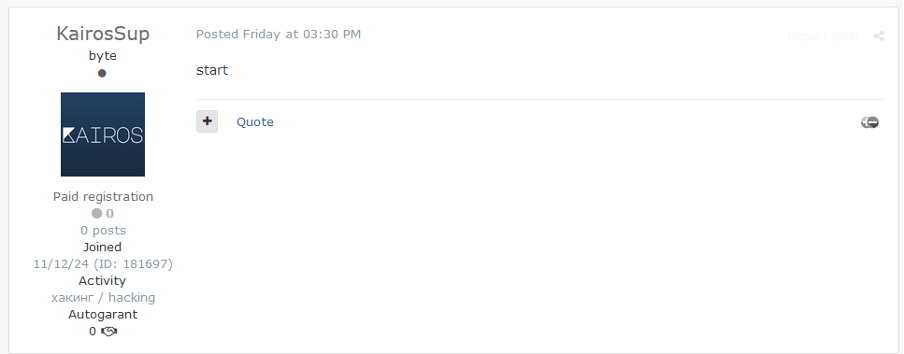
Figure 2 – KairosSup reply to IAB listing.
Notably, on 17 November 2024, the IAB responded again to the thread stating that KairosSup did not respond within 24 hours of the auction ending. As such, the access was once again listed for sale. KairosSup joined the forum on 12 November 2024 and has no other recorded activity as of 18 November 2024. Due to the lack of activity, the user has a reputation score of zero.
Why would Kairos use an IAB?
Kairos likely seeks to purchase access from IABs for three reasons. Firstly, purchasing access from an IAB decreases the level of technical capability required to compromise organisations. Secondly, this saves time for the attacker, who does not need to identify a victim worth attacking or search the internet to find exposed devices or credentials to compromise them. Finally, with information provided in IAB listings, it is possible to determine the victim organisation, as well as geographical location, sector, and revenue. Extortion groups can use this information to target specific types of sectors and countries, possibly even specific organisations. The IAB market remains a prominent sphere of the threat landscape, providing accesses for ransomware and extortion groups, APTs, and data brokers. It is equally likely that as Kairos develops its capabilities, it will continue to utilise IABs, whilst also compromising organisations themselves.
It is important to note that the emergence of Kairos is just one of many this year. Extortion groups are emerging at an increasing rate, with a relatively high rate of emergence in 2024, resulting in higher probability of attacks. This increase also provides threat actors like IABs an expanding market of buyers to purchase their offerings.
Cyjax has conducted analysis of the IAB market for 2024 Calander Q1, Q2, and Q3, providing insight into the market, how they operate on cybercriminal forums, and their effect on the landscape.
Cyjax will continue to monitor the various data-leak sites operated by extortion groups for new emergences, trends, and significant attack announcements.
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
Get Started with CYJAX CTI
Empower Your Team. Strengthen Your Defences.CYJAX gives you the intelligence advantage: clear, validated insights that let your team act fast without being buried in noise.
