Introduction
In 2024, Cyjax observed the emergence of 72 extortion and ransomware group data-leak sites (DLSs). As of late February 2025, Cyjax has identified DLSs for six new groups in 2025, as noted in recent blogs on extortion groups Kraken, Morpheus, GD LockerSec, Babuk2, and Linkc. The latest DLS which Cyjax has identified is named Anubis. This Ransomware-as-a-Service (RaaS) group appears to be sophisticated and professional, providing services including affiliates, data ransoms, and access monetisation.
There is no known connection between the Anubis threat group and the stealer of the same name.
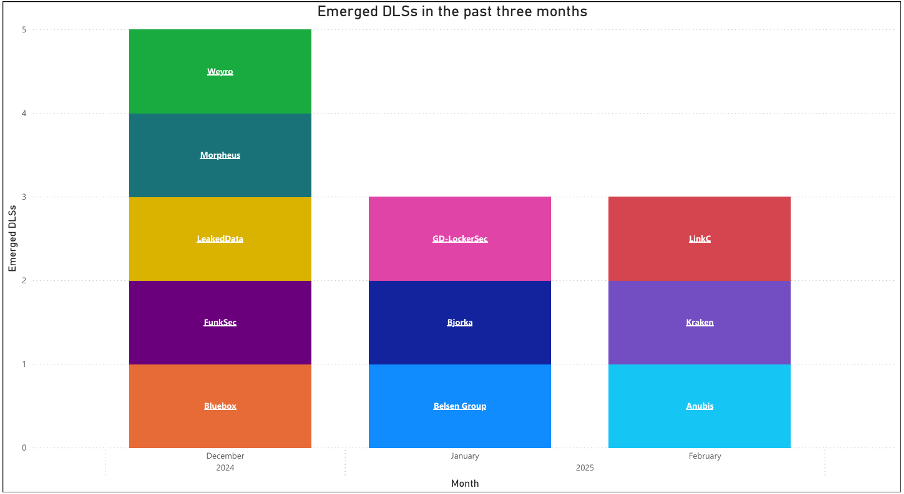
Figure 1 – New extortion and ransomware groups Cyjax has observed over the last 3 months.
Key takeaways
- The group’s DLS has four victims as of 25 February 2025. The detailed blog entries contain each alleged victim and a description of the files that have been leaked.
- Anubis has posted DLS listings for organisations in the United States, Peru, and Australia. One of its victims, namely First Defense Fire Protection, has confirmed a data breach.
- The group has accounts on two prominent cybercriminal forums, as well as an X (formerly Twitter) account. The forum accounts have been active since September 2024.
- Anubis’ forum accounts have previously been used to sell fullz, which are complete sets of personal information likely gained from data leaks.
Context
Extortion groups commonly use DLSs to further extort victims, typically proceeding in multiple stages. The first threat is that the victim’s name and news of a successful attack against it will be published on the extortion group’s website. Should this fail to motivate a victim to pay a ransom, the group’s next step is typically to provide proof of the successful theft of its data, such as screenshots of internal file trees, samples of employee or customer PII, or other sensitive documents. The group may add a countdown at this stage, noting that should the victim fail to pay by the conclusion, it will make available to DLS visitors all stolen data, either for free or at cost.
Victimology
As of 25 February 2025, four victims have been listed on the Anubis DLS. These victims include the US-based First Defense Fire Protection and Summit Home Health, INC, the Peru-based Comercializadora S&E Perú, and Australia-based Pound Road Medical Centre. Information included in these leaks include “fullz” which typically refer to complete banking information, building plans, personal data, and internal documents.
The group’s main advertisement was posted on a prominent ransomware-focused cybercriminal forum on 23 February 2025. Within this post, Anubis stated that it does not target ex-USSR and BRICS countries, networks encrypted less than 12 months before an attack would take place, and the education, government, and non-profit sectors. However, the group does target the US, Europe, Canada, and Australia, and other countries after it studies the targets.
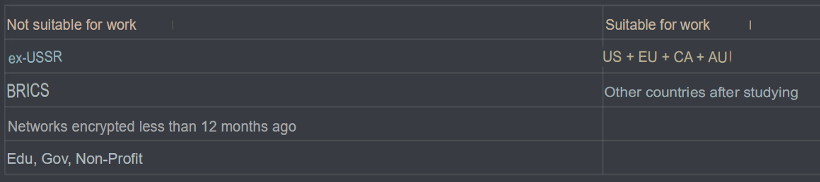
Figure 2 – Cybercriminal forum post containing Anubis’ victimology. (Translated from Russian)
For each listed victim, Anubis provides a detailed analysis of the leaked data. The group highlights points of interest such as screenshots of the data and related information, as seen in Figure 3. Cyjax has examined these documents and found mentions of other organisations, such as the First Defense Fire Protection leak containing references to Siemens. There does not appear to be a countdown indicating when the data will be released, as is common on other extortion group DLSs.
Of the four alleged victims, First Defense Fire Protection was the only organisation that has published a recent data breach notification. The organisation has stated that a breach occurred on 25 April 2024, with impacted individuals being notified on 22 January 2025.
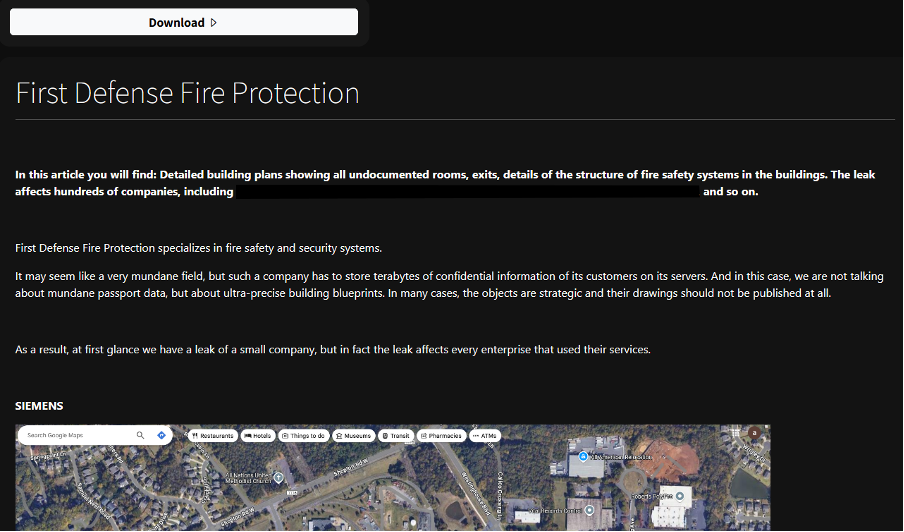
Figure 3 – A section of the Anubis DLS listing for First Defense Fire Protection.
The Anubis DLS
Anubis’ DLS is well made, quick to load, and has suffered no downtime in the time period Cyjax has attempted to access the site. There are five main pages. The main landing page includes blogs for each alleged victim, with the other pages being “news”, “FAQ”, “About”, and “Rules”.

Figure 4 – Anubis’ DLS landing page.
The news page has two notifications as of 25 February 2025, which state that FDFP has confirmed the data breach and that every leak is also published on X. These notifications are dated from December 2024, highlighting the group’s existence and activity prior to public advertisement of the DLS.
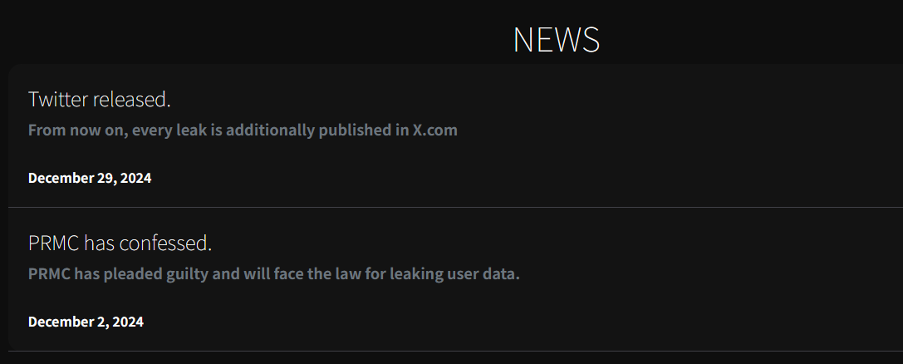
Figure 5 – News section of Anubis’ DLS.
The FAQ section includes information regarding the group’s operations, stating “We specialise in disseminating company data leaks supplied to us by our anonymous sources”. Anubis states that a file tree access system with download functions becomes available after a “timed period of time” after the original blog is released. However, further details are not provided.
Figure 6 – FAQ section of Anubis’ DLS.
The About page contains details regarding how victims can contact the group to remove published data leaks, how other threat actors can partner with Anubis and potential media relations.
Figure 7 – About section of Anubis’ DLS.
Finally, the Rules page contains contact details for the group’s X profile and an account on a cybercriminal forum.
Figure 8 – Rules section of Anubis’ DLS.
Other locations
Cyjax has identified accounts on prominent Russian-language cybercriminal forums which operate under the names ‘Anubis_media’ and ‘supersonic’. These accounts have been used to advertise Fullz, the group’s DLS, and services offered by the operation.
Anubis advertises an affiliate program with a ransomware binary allegedly capable of high-speed encryption based on ChaCha and ECIES. It has cross-platform capabilities, self-propagation, anti-defence mechanisms, privilege escalation, and more features.
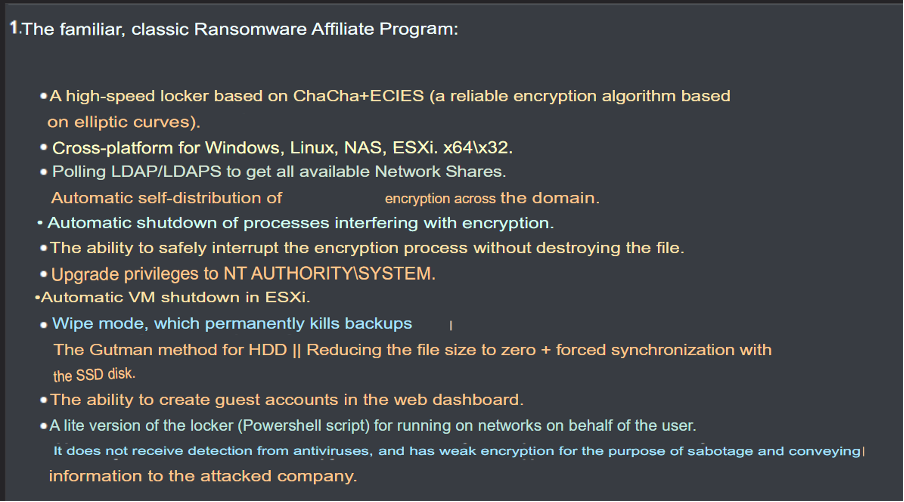
Figure 9 – Anubis affiliate service description (translated from Russian).
It is important to note that whilst Anubis mainly operates as a data leak extortion and RaaS group, it also conducts its operations via partnerships with other threat actors. Attackers can monetise initial access through the group in a 50-50 partnership and data ransom with a 60-40 partnership. This means that Anubis receives 60% of profits derived from the attack. Additionally, the group offers a ransomware operation with an 80-20 partnership, with long-term cooperation possibly resulting in higher percentage profits for the affiliate.
Anubis’ X account, which is called ‘Anubis_media’, was created in December 2024. It has been used to post leak notifications for each of its victims, including details of what data the breach includes.
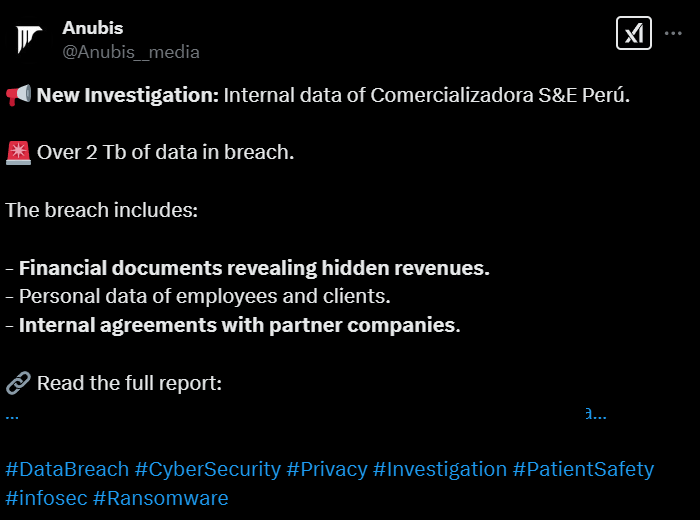
Figure 10 – Anubis’ X post for victim Comercializadora S&E Peru.
Threat Assessment
As of late February 2025, there is significant information regarding the group and its operations in its DLS advertisement. One alleged victim has acknowledged a data breach, though the other three have not. Anubis offers partnerships with other threat actors to advertise and share data leaks, as well as monetising initial accesses and operating a Ransomware-as-a-Service (RaaS) model. It is highly likely that the group will continue to conduct attacks, publish data leaks, and work with other threat actors for malicious activity.
To access our full intelligence repository containing detailed profiles like this one, covering extortion groups, advanced persistence threat groups (APTs), data brokers, hacktivists, initial access brokers, and more, click here to take a test drive of Cymon.
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
