CVE discovery, PoC Development, IAB Listings, to Ransomware Attacks: How Cybercriminal Forums Facilitate the Lifecycle

By Olivia Betts and Adam Price
In July 2024, CloudFlare identified that it can take cybercriminals as little as 22 minutes to weaponise a publicly available Proof-of-Concept (PoC) exploit following its release. The IT services management company noted an increase in scanning for disclosed Common and in attempts to weaponise available PoCs across 2023 and 2024. During the reporting period, the most frequently targeted vulnerabilities were CVE-2023-35082 in MobileIron, CVE-2023-50164 and CVE-2022-33891 in Apache products, as well as CVE-2023-29298, CVE-2023-38203, and CVE- 2023-26360 in Adobe Coldfusion.
The speed at which threat actors can move from discovering a PoC exploit, which is typically shared on code sharing and management platforms such as GitHub, to identifying exposed instances vulnerable to the CVE and exploiting them is alarming. One location that likely assists cybercriminals in this endeavour is the Bugtrack (translated from Russian) section on prominent, mostly Russian-language, cybercriminal forums. These popular discussion sections see forum users share vulnerability news and analysis, PoCs, exploit code, guides, and scanners. They also see more experienced users troubleshooting issues which less experienced users encounter when attempting to exploit these vulnerabilities.
Cyjax routinely monitors these sections and observed various threads in which users discussed some of the vulnerabilities identified by CloudFlare. These threads are also visible to initial access brokers and ransomware affiliates.
Bugtrack discussion

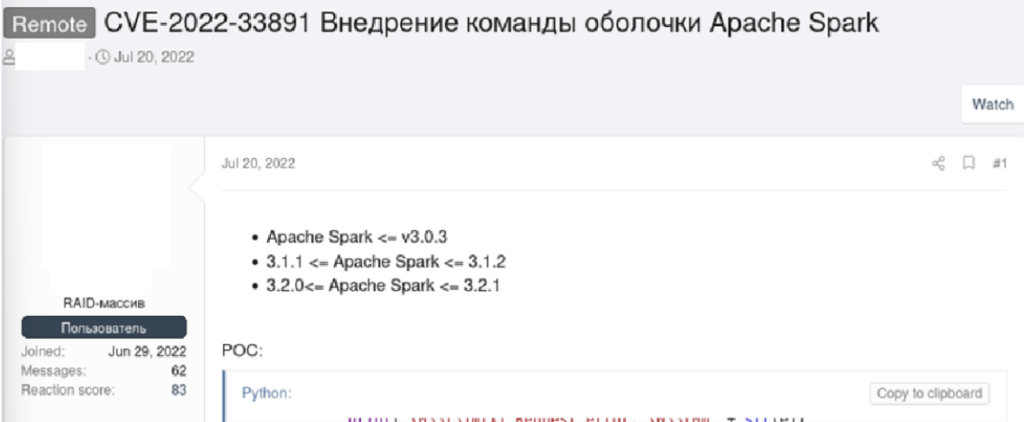
On 18 July 2022, GitHub user W0lfh4cker created a repository containing a PoC for CVE-2022- 33891, a vulnerability affecting the Apache Spark user interface (UI). On 20 July, a user of a Russian-language forum posted a link to this repository, along with further information on the vulnerability. This post generated a significant level of discussion amongst forum users. One of these shared links to two additional PoCs for CVE-2022-33891, which were both created on 19 July.
Discussion of this vulnerability was not only limited to that thread. On 08 September 2022, a reputable forum user contributed to an existing thread about to share one for exploiting CVE-2022-33891. Metasploit is an open-source penetration testing framework which can be used to create and deploy exploit code. Modules can be imported into a managed ecosystem designed for conducting attacks, allowing a vulnerability to be easily exploited with the aid of the software.
Within the space of two months, the barrier to entry for exploiting this flaw dropped significantly. Initially, a threat actor would have had to develop their own code before making use of the existing PoC. Finally, a threat actor will often use a pre-written module within a well-known and documented framework as opposed to needing the technical knowledge to create it themselves.
Another Apache vulnerability also received a fair amount of attention, namely CVE-2023-50164, which aZects Apache Struts. On 07 December, the developers announced that an update for the software would be made available to address this flaw. It gained more attention during that week, with a PoC posted on GitHub on 13 December. Two articles were then published on 14 and 15 of that month, respectively. Only a day later, a user on an English-language cybercriminals forum posted links to both the repository and the articles. At the time of writing, it has over 2,500 views.
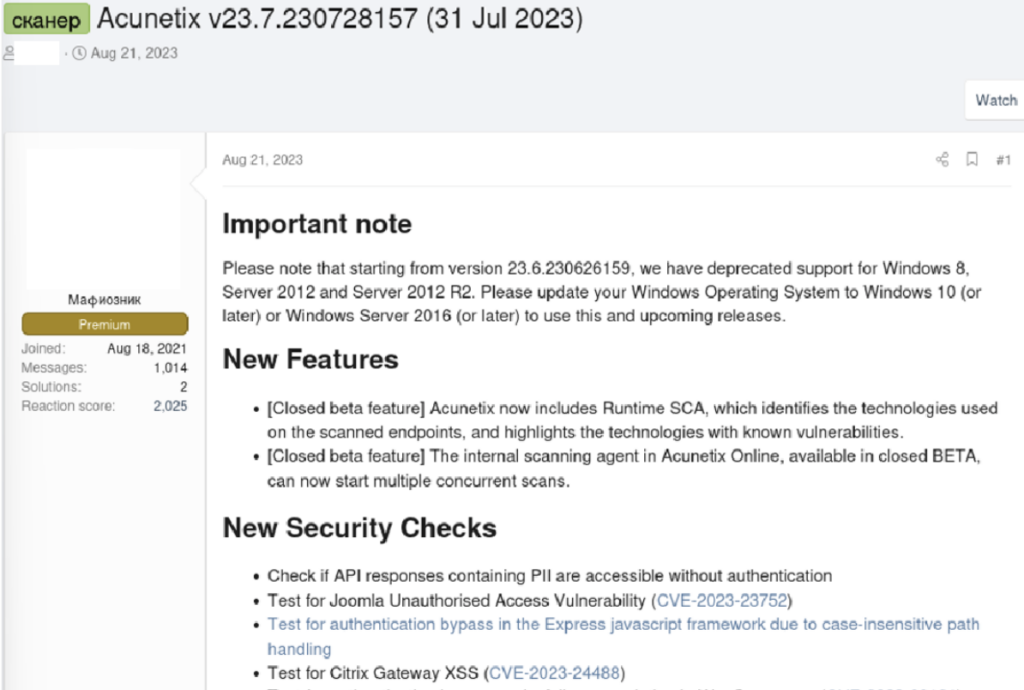
Several other commonly targeted vulnerabilities were discussed on underground forums, particularly in the context of Acunetix, a popular web security scanner. This is a tool which can automate the ability to scan endpoints for known vulnerabilities. Often used as part of a penetration test, these tools allow endpoints to be tested for thousands of vulnerabilities within a short timeframe. This aids in understanding how secure an endpoint is. For cybercriminals, these tools allow them to quickly and efficiently determine which targets they may be able to exploit for their own personal gain, saving them time in the process. Russian- and English-language forums host threads where users can download a cracked version of the scanner. When Acunetix receives a software update, introducing new checks for new vulnerabilities, these threads are updated.
Unlike the sharing of GitHub repositories, which often happens days after a vulnerability was made public, updates on cracked Acunetix software often happen weeks after the fact. For example, the update for CVE-2023-26360 came out on 09 May 2023, though forum users did not begin publicly discussing the flaw until 02 June. Equally, the software received an update to scan for CVE-2023-29298 on 31 July 2023, but again cybercriminals did not materialise until 31 August. The relatively large delay between the discovery of vulnerabilities and cracks of the Acunetix updates being released is likely due to the work required to carry this out. However, the fact that this work is put in with an apparent regularity demonstrates that there is an audience for it on cybercriminal forums. Though there is currently no public chatter on these locations around GitHub exploits or PoCs for these vulnerabilities, there is clear evidence of cybercriminal forum users scanning systems for them.
Initial access broker listings
The information in the Bugtrack sections is of course available to initial access brokers (IABs), who also operate on these forums. IABs form a key part of the cybercriminal ecosystem and facilitate access for ransomware groups, data leakers, and advanced persistent threat groups (APTs) into corporate networks. They are likely to find the vulnerabilities, such as those identified by CloudFlare, to be highly valuable. Upon successful exploitation, IABs gain significant access into targeted networks, which it can then list for sale to other forum users. Whilst there is no indication that any IAB listings directly relate to the vulnerabilities discussed earlier, initial access brokers have often listed accesses to organisations through one of the affected products in the vulnerabilities, namely Apache.
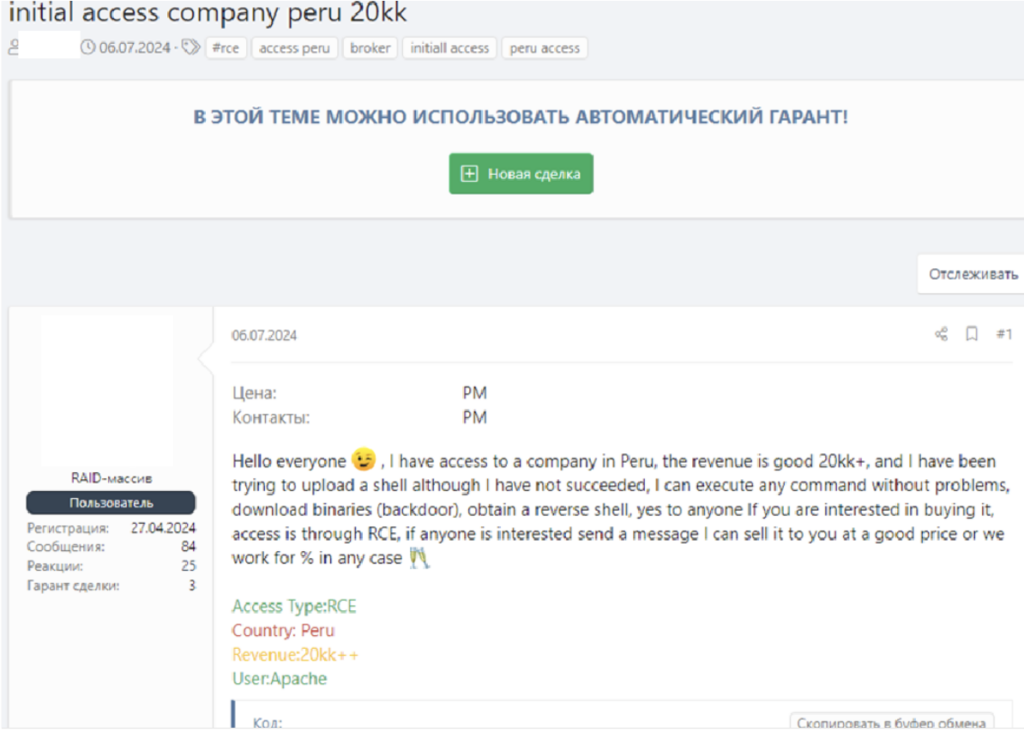
In early June 2024, an IAB advertised access on a prominent Russian-language cybercriminal forum to an unnamed Peru-based organisation with a revenue of over $20 million. This was accessed via remote code execution (RCE) with the user level written as “Apache”. From this information, it is highly likely that the IAB exploited a vulnerability in Apache to gain the ability to execute code remotely.
In January 2024, another IAB on a different prominent Russian-language cybercriminal forum advertised access to a Pakistan-based government organisation via web shell. The listing stated that the web shell was through an Apache server on a Windows-based machine, which may reasonably have been obtained via a vulnerability on this server. Web shells are commonly delivered as initial-stage payloads when vulnerabilities such as unrestricted file upload or SQL injection are found. They allow a shell-like interface for the threat actor to interact with the server behind the website, which is commonly facilitated through malicious PHP or ASP.NET pages.

Other than the several listed accesses with the word Apache included, there are no observable mentions of Coldfusion or MobileIron in the IAB market. IABs often obfuscate access details as much as possible to prevent both the victim organisation and the direct access method from being identified. It is likely that there are more listings which exploited this vulnerability, but the details were not included.
CVE discovery to ransomware attack lifecycle
In a more general perspective, there appears to be a clear correlation between CVE disclosure, cybercriminal discussion, IAB listing, and ransomware attacks.
On 19 February 2024, ConnectWise released a statement disclosing a critical-rated vulnerability in ConnectWise ScreenConnect, a remote support, access, and meeting solution. The vulnerability, tracked as CVE-2024-1709, is an authentication bypass vulnerability that could allow an attacker to remotely access and exfiltrate confidential data from servers, or deploy malware. Active exploitation of the flaw was identified shortly thereafter.
On 22 February 2024, a user on a ransomware-focused cybercriminal forum posted an entire article copied from a researcher’s analysis of the ScreenConnect vulnerability. This post included a link to the public PoC exploit the researchers created. Whilst this thread has no replies at the time of writing, the discussion around the vulnerability, particularly with the PoC linked, may have provided both resources and incentives for ransomware threat actors to conduct attacks using this exploit. On 26 February 2024, the same user posted another article detailing the post-exploitation activity observed by threat actors conducting attacks exploiting the vulnerability. Resharing this activity received positive replies from users, stating that it was “interesting stu* to know how they are working” and a “great topic”. Not only does this provide additional information to other users on the forum, but also portrays to active threat actors what researchers have identified and observed.
On 25 February 2024, a thread titled “ConnectWise accesses for sale (Infernal Network)” appeared on a Russian-language cybercriminal forum. In the initial post on the thread, a user advertised access to 31 different organisations, all of which were listed as being through ConnectWise. Listings were posted spanning multiple countries and sectors, with the United States and the United Kingdom being the most target countries, and sectoral targeting of IT, telecommunications, professional services, real estate, healthcare, infrastructure, manufacturing, retail, education, and legal.
Attacks by ransomware groups including LockBit, BlackBasta, and Bl00dy were identified using this vulnerability before deploying their ransomware payloads. Additional threat actors were seen deploying Cobalt Strike and XWorm, both of which are commonly used by attackers and provide remote access capabilities. It is unconfirmed, but possible, that the ransomware threat groups may have obtained initial access from an IAB.
Another notable attack facilitated through ScreenConnect is the breach that took place against Change Healthcare. An affiliate of BlackCat allegedly compromised the organisation and deployed ransomware, resulting in data exfiltration and file encryption. This resulted in the payment of a $22 million ransom. It is uncertain whether CVE-2024-1709 was exploited in this attack. However, it is entirely possible, as the attack took place on 21 February 2024, a day after the first suspicious activity regarding the vulnerability was identified.
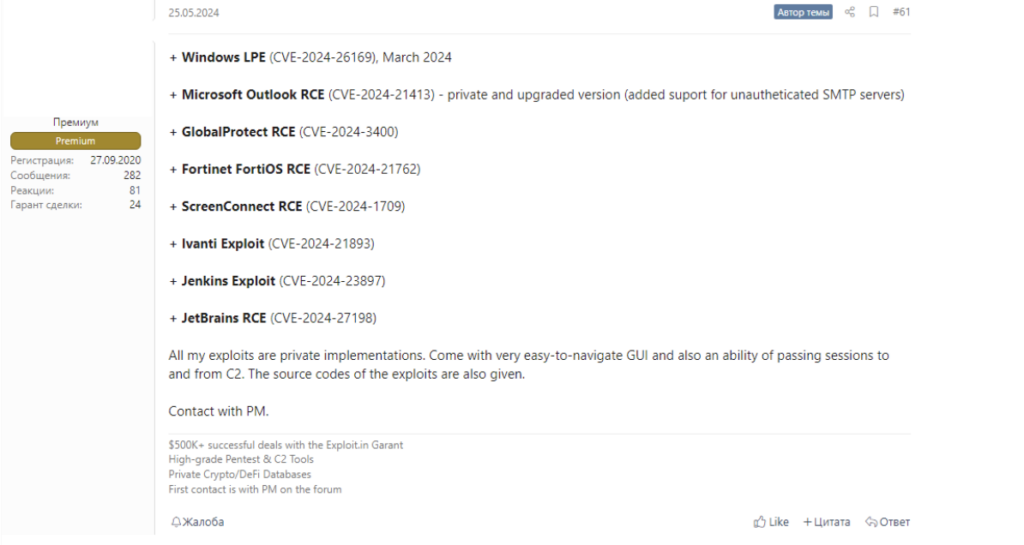
Interestingly, a private implementation of the exploit for CVE-2024-1709 was listed alongside other vulnerabilities in a post on 25 May 2024 by a prominent exploit broker active on a Russian-language cybercriminal forum. This broker did not include a price for the exploit but stated that all listings include “[an] easy-to-navigate GUI and also an ability of passing sessions to and from C2 [sic]”. The patch for the vulnerability was released on 21 February 2024, demonstrating how threat actors continue to consider and exploit the vulnerability months after patches have been released due to the number of devices which go unpatched.
It is important to note that whilst these appear to be related, the only confirmed association is that the vulnerability has been exploited in ransomware attacks and by unnamed threat actors deploying Cobalt Strike and XWorm. However, if these are not connected, it portrays the widespread discussion and use of vulnerability exploits, from the moment they are disclosed to after patches are released. This further displays the risks that vulnerable instances can introduce to an organisation, as IABs can gain and sell initial access to the vulnerable system from which threat groups can deploy ransomware and other malware strains. Due to the prevalence of these exploits, and the widespread existence of both public Proof-of-Concept exploits and private implementations, instances that are left vulnerable remain at risk.
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
Get Started with CYJAX CTI
Empower Your Team. Strengthen Your Defences.CYJAX gives you the intelligence advantage: clear, validated insights that let your team act fast without being buried in noise.
