Introduction
Following the emergence of data-leak sites (DLSs) for extortion groups Morpheus and GD LockerSec in January 2025, Cyjax has discovered a DLS which claims that the infamous Babuk ransomware group has returned. Read on to find out what we know so far.
Key takeaways
- The Babuk ransomware group originally emerged in December 2020 and continued its operations throughout the first half of 2021.
- A new DLS claiming to be the Babuk group has emerged, with researchers naming the site ‘Babuk2’ or ‘Babuk-Bjorka’.
- There are doubts surrounding the legitimacy of the group’s return within the cybersecurity community.
- Evidence pointing to this being a copycat is that Babuk2 appears to be simply posting recycled ransomware victims and data from other ransomware groups and threat actors.
- It is likely that the site’s current administrator ‘Bjorka’ is using the Babuk name to further their legitimacy whilst having no real connection to the original ransomware group.
- Several of the posts on the site have been linked to Bjorka, who has their own separate clearnet site for selling data stolen in attacks. This user also has accounts on the prominent cybercriminal forum BreachForums and Telegram. At least three data sets previously leaked by Bjorka match new listings on the Babuk2 DLS.
Context
Extortion groups commonly use DLSs to further extort victims, typically proceeding in multiple stages. The first threat is that the victim’s name and news of a successful attack against it will be published on the extortion group’s website. Should this fail to motivate a victim to pay a ransom, the group’s next step is typically to provide proof of the successful theft of its data, such as screenshots of internal file trees, samples of employee or customer PII, or other sensitive documents. The group may add a countdown at this stage, noting that should the victim fail to pay by the conclusion, it will make available to DLS visitors all stolen data, either for free or at cost.
History of Babuk
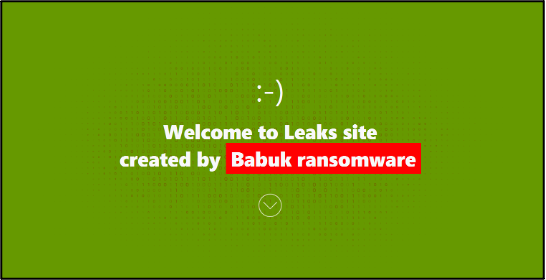
The Babuk ransomware was first uncovered in December 2020 and was active through the first half of 2021 before it ceased operations. Its DLS stayed online with no new victims until late February 2024, when it went offline. It operated as a Ransomware-as-a-Service and was known to have a strong encryption mechanism. Originally, the group leaked victim data on the now-defunct English-language cybercriminal forum Raid Forums, before pivoting towards creating its own dedicated data-leak site (DLS). Here, it would name victims who refused to pay the group’s ransom demands.
In September 2021, the Babuk’s source code was leaked by a disgruntled member of the group to a Russian-speaking cybercriminal forum. The developer was allegedly a 17-year-old from Russia who had been diagnosed with stage-4 lung cancer and decided to the leak the entire Babuk source code for the Windows, ESXi, and NAS versions. Prior to this, in June 2021, the builder for the Babuk ransomware was also leaked online. This could allow users to create custom versions of Babuk and encrypt organisations’ files and the decryptor needed to recover the files.

The group rebranded in June 2021, changing its name to Payload.Bin before going back to the name Babuk soon after. In May, the cybercriminals outlined a plan to start a hub for ransomware operators to host their leaks if they did not have a site of their own, launching Payload.Bin shortly after. It could be that the Payload.Bin venture proved relatively unsuccessful, so the group returned to conducting its own data-theft-extortion attacks under its original name.
The Babuk ransomware operators were also responsible for launching the RAMP Russian- and English language cybercriminal forum, which was originally designed and dedicated for use by ransomware groups. This was due to ransomware posts being banned or restricted on other large forums such as XSS and Exploit. The purge of ransomware posts from forums began in 2021 when users started to worry about the negative implications of selling ransomed data on the forums. Since taking down ransomware operations is such a heavy focus for law enforcement agencies globally, there was fear among forum users that having ransomware on cybercriminal forums would attract more attention from legal entities. As such, banning ransomware posts and accounts was undertaken to help avoid potential legal repercussions.
New DLS emerges
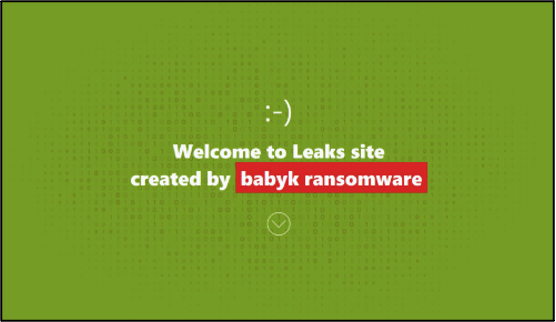
A new data-leak site bearing the name Babuk ransomware has emerged. It has been used to state that the group has returned, with researchers naming the DLS Babuk2 or Babuk-Bjorka due to the new administrator of the blog being known as ‘Bjorka’ on forums and Telegram. There has been scepticism about this return from the cybersecurity community, with researchers stating that this site is an impersonation of the group and is not real. Consequently, some researchers have claimed that the original Babuk group has not returned. This opinion has been formed due to the victims listed on the site having already been listed by extortion groups RansomHub, FunkSec, and original the Babuk group in the past.
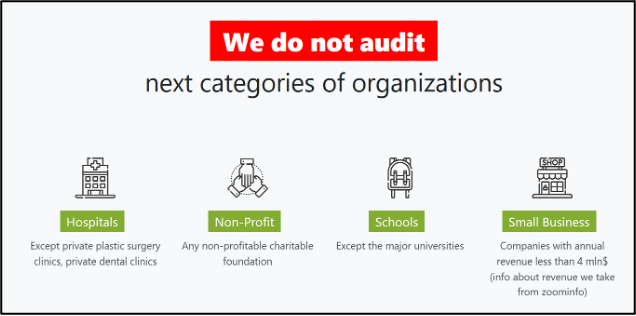
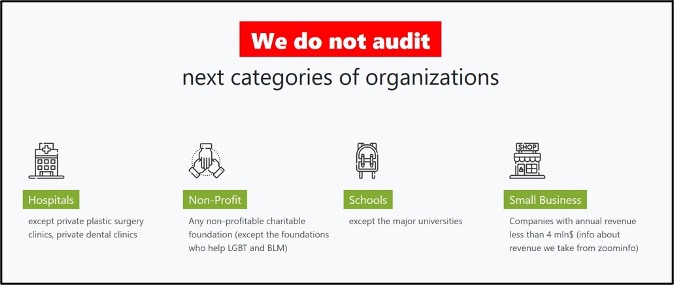
The new “Babuk ransomware” DLS looks nearly identical to the original one. The page welcomes the user to the site, following which it states that it does not target hospitals, non-profits, schools, and small businesses, except for plastic surgery or dental practices and major universities. One difference is that the group’s original page stated that it would still target charities that support the LGBT and BLM communities, whilst the new one states that all charitable organisations are off limits.
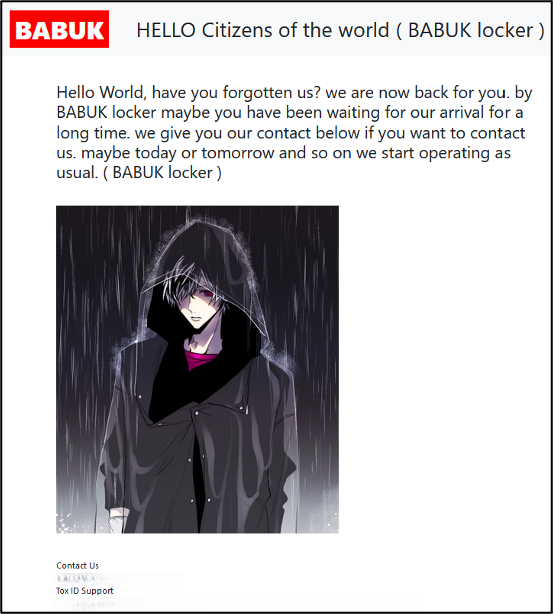
On 27 January 2025, the group released a new post on the DLS proclaiming its return providing people with a Tox chat ID that can allegedly be used to contact the group.
The group’s “About Us” page and its payment rules and instructions on using the decryptor remain the same as the old DLS. The group states that Babuk ransomware is a “Non malicious, specialized software, created with purpose to show the security issues inside the corporate networks.” This page also clarifies to victims that payment must be made in Bitcoin.
Victimology
The new DLS lists over 65 victim organisations from various geographies and sectors. Allegedly affected countries include Germany, the US, UK, Brazil, South Africa, Jordan, Mexico, Colombia, Montenegro, Kenya, Pakistan, Mongolia, North Macedonia, Uzbekistan, Australia, Zambia, Romania, Slovakia, Indonesia, Canada, Italy, El Salvador, Norway, and Malaysia. Whilst no Russian organisations have been listed on the site, there are victims from Commonwealth of Independent States (CIS) countries such as Uzbekistan.
Victims are from a variety of sectors including energy, manufacturing, IT, manufacturing, professional services, transportation, telecommunications, agriculture, government, healthcare, education, hospitality, and finance.
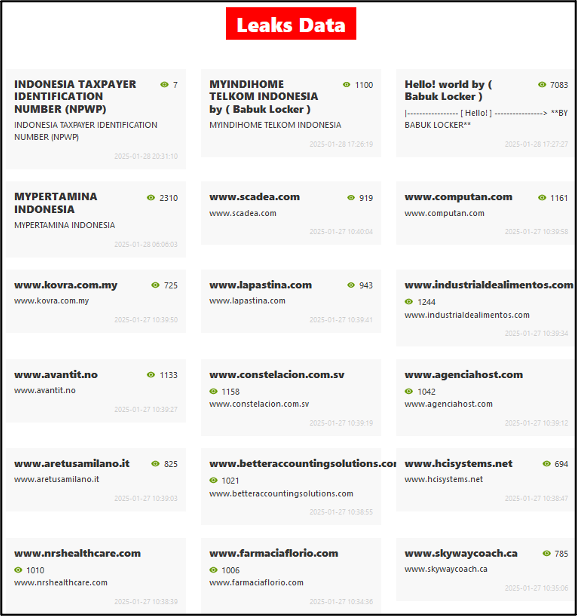
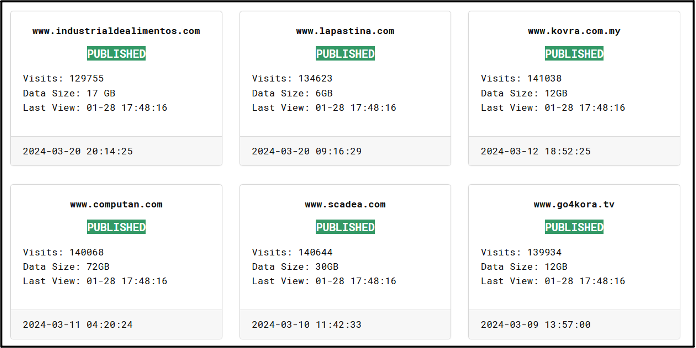
Most of the currently listed victims were uploaded between 27 and 28 January 2025, though four of the listed victims are dated 1 February 2021. These four victims from 2021 are the original four victims which were named by the Babuk ransomware group on its DLS when it was created.
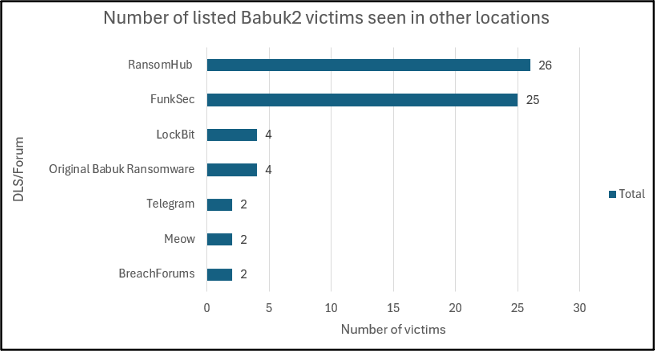
All the remaining organisations have also been claimed as victims in other ransomware attacks. The majority pertain to RansomHub (26 victims) and FunkSec (25 victims), with others being linked to ransomware groups LockBit (4 victims) and Meow (2 victims).
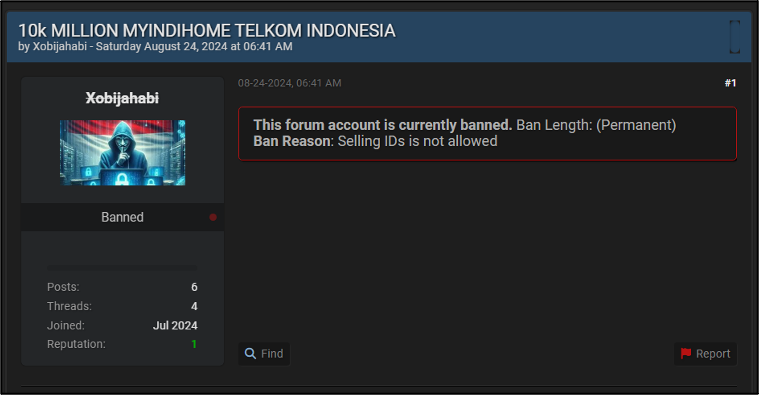
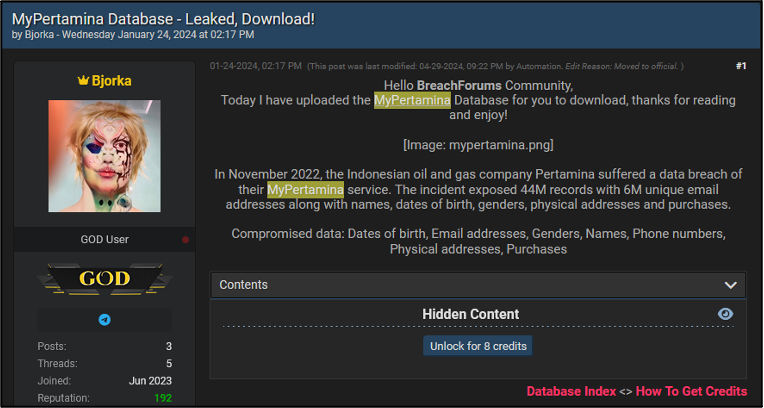
There are currently also two listed victims on the site which had their data previously leaked on English-language cybercriminal forum BreachForums. One such victim had their data leaked by a user known as ‘Xobijahabi’ in August 2024, though the post was later banned for selling data that is not allowed on the forum. A second victim was listed on BreachForums by a user named ‘Bjorka’ in January 2024. Additionally, two more victims were previously listed by the same user, Bjorka, on a Telegram channel. Bjorka is the current administrator of the Babuk2 DLS and appears to be posting their own data on the site. This is alongside data that has been downloaded from other ransomware groups.
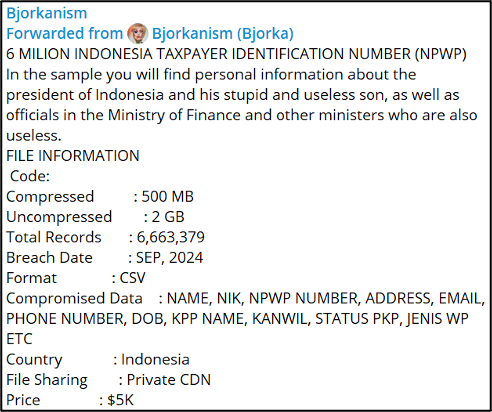
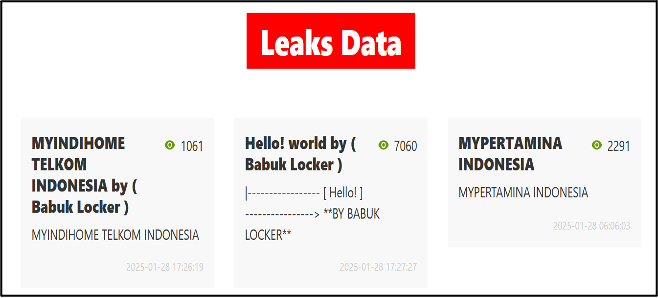
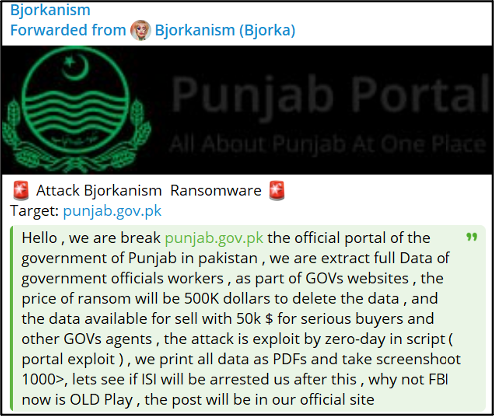
In some of their recent Telegram posts, the user Bjorka, also known as Bjorkanism, refers to their compromises as ransomware attacks. In one instance on 23 January 2025, the user posted to Telegram claiming to have conducted a ransomware attack against a Pakistan government website. Here, the user stated that they had demanded a ransom amount of $500,000 and offered to sell the data to “serious buyers” for $50,000. The user claimed to have conducted the attacks by exploiting a zero-day and then stealing all the data in the form of PDFs, as well as screenshotting. It is currently unclear whether Bjorka uses any encryption on the compromised targets, or whether they simply steal data and extort the victim.
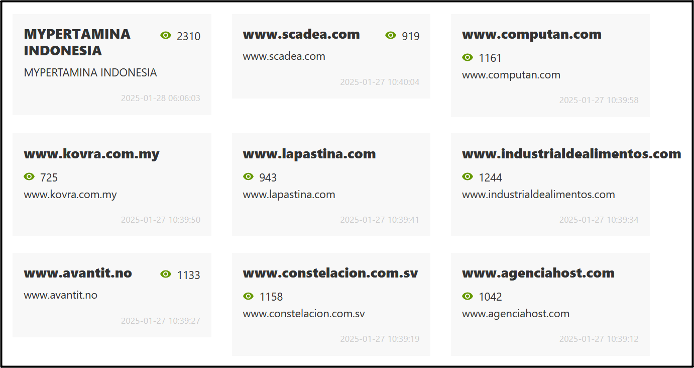
Bjorka also has their own clearnet website where they list their databases for sale, providing varying prices, data samples as proof, and Telegram contact details. Some of the listings on this site also match those which have been posted to the Babuk2 DLS. This includes NPWP, MyIndiHome, and MyPertamina. Whilst the MyIndiHome database on BreachForums, which was mentioned above, was posted by a user known as Xobijahabi, this user has since been banned from the forum. Therefore, it is possible that the user simply rebranded to the name Bjorka, though this is unconfirmed.

Cybercriminal response
At the time of writing, there has been no discussion of the re-emergence of the Babuk ransomware on popular cybercriminal forums.
Threat assessment
At the time of writing, there appears to be no evidence supporting the legitimate return of the Babuk ransomware group. Whilst the new Babuk2 DLS successfully mimics the template and style of the original Babuk ransomware site, all the named victims and leaks that are listed on the new Babuk2 DLS have been taken from known leaks or from other prominent ransomware groups. Additionally, there are no new or original victims have been named or posted on the site.
The user Bjorka appears to be posting some of their own previously offered data leaks on the Babuk2 DLS. Since Bjorka is the site administrator, it is highly likely that this user is simply impersonating the Babuk threat group to reach a wider audience. Since Babuk is a well-known name in the cybercriminal community, Bjorka could be exploiting it for the purpose of appearing like a more credible threat. There is currently no evidence to suggest that Bjorka has any ties to the original Babuk ransomware group.
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
