Introduction
The latest data leaks site (DLS) Cyjax has identified is titled RALord, which constitutes one of 14 new DLSs identified in March 2025 alone. This Ransomware-as-a-Service (RaaS) group appears to be sophisticated and professional, providing services including affiliates, data ransoms, and dark web advertisements. It has been reported that the group is active on at least one cybercriminal forum under the username ‘ForLord’.
As of late March 2025, RALord is not known to be associated with any other threat actors. However, the group claims that its product is not a new product and that it has experience with RaaS programs. Because of this, it is possible that the group has links to the similarly named ransomware group RAWorld, which is also known as RAGroup. The known RAWorld DLS links are currently unavailable, and the group has not posted any new victims since December 2024. It is also possible that RALord is simply using the name to hijack the group’s existing reputation and appear more established.
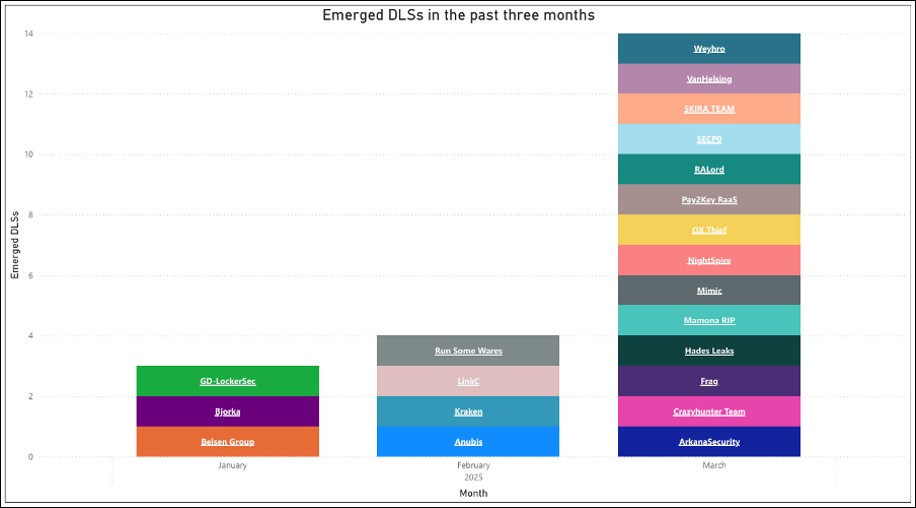
Figure 1 – DLS sites which have emerged in 2025 by month.
Key Takeaways
- The RALord DLS emerged in late March 2025. Its first victim, an engineering and industrial services company, was named on 22 March. Only three victims have been named on the site as of 28 March 2025.
- The group runs a RaaS program where affiliates are offered 85% of profits made from ransom payments. In return, RALord takes 15% of the profit.
- RALord offers a variety of services, including the sale of data, advertising services on Tor, and offering its encryption tool for a price without having to subscribe to the RaaS program.
- All the victims listed on the group’s DLS appear to be original and have not been named by other known ransomware groups tracked by Cyjax.
- It is possible that RALord has connections to other already established ransomware groups such as RAWorld, though this is currently unconfirmed.
Context
Extortion groups commonly use DLSs to further extort victims, typically proceeding in multiple stages. The first threat is that the victim’s name and news of a successful attack against it will be published on the extortion group’s website. Should this fail to motivate a victim to pay a ransom, the group’s next step is typically to provide proof of the successful theft of its data, such as screenshots of internal file trees, samples of employee or customer PII, or other sensitive documents. The group may add a countdown at this stage, noting that should the victim fail to pay by the conclusion, it will make available to DLS visitors all stolen data, either for free or at cost.
The RALord DLS
The RALord DLS first emerged in late March 2025 and has content written in both Russian and English. It is comprised of several sections, including a main page where its alleged victims are listed.
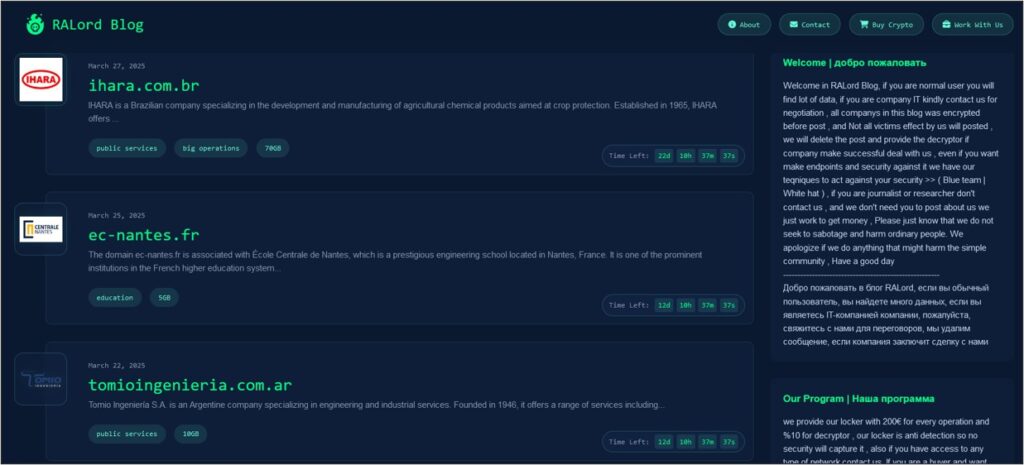
Figure 2 – The main page of the RALord DLS.
Each victim has its own subsection which includes details such as the organisation’s name and a description of its business. These subsections also include a list of the type of data stolen and where applicable, purported samples.
The victims also currently have countdown timers, which highly likely indicates
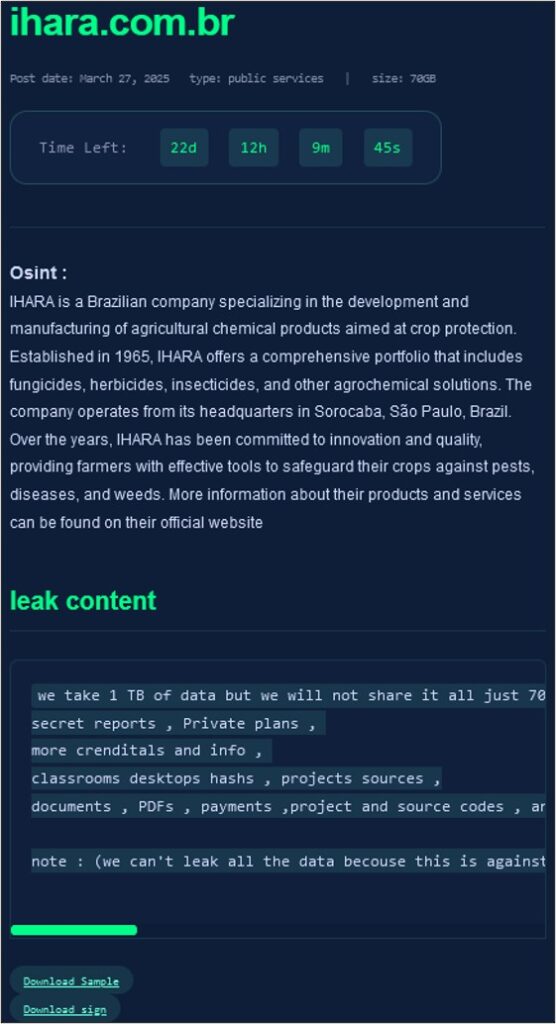
Figure 3 – An example of a victim subsection on the RALord DLS.
The DLS also has a “Contact” page where its Tox and Session IDs are listed.
Figure 4 – The contact page on the RALord DLS.
RALord has also dedicated a section to describing its alleged RaaS program, data brokerage, and advertising services.
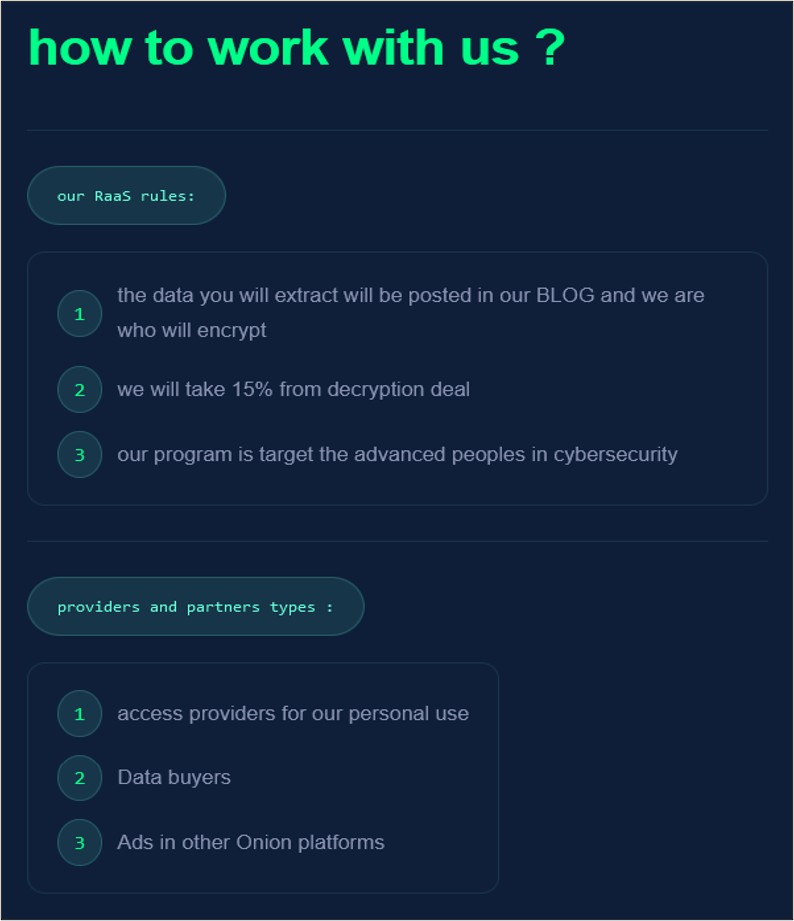
Figure 5 – The RaaS page on the RALord DLS.
ALord’s DLS also has a section which advises site visitors on how to purchase cryptocurrency, with the group accepting BTC, XMR, and LTC. The group likely provides this information to ensure that its victims, who may be unaware of cryptocurrency, are still able to pay. This means that victims cannot use a potential lack of understanding as a reason not to pay the ransom demand.
The group also allegedly accepts certain bank transfers and offers an escrow service. This is where a payment is held by a third-party, such that both the seller and buyer are satisfied with the transaction. Though they are more common on cybercriminal forums, escrows may be used by ransomware groups to ensure victims are satisfied that the provided decryptor works. In this case, the ransom payment is then released to the group.
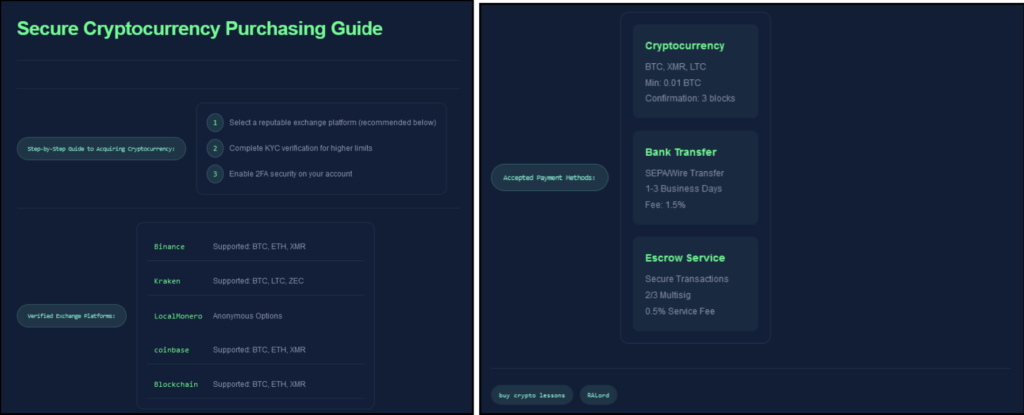
Figure 6 – The cryptocurrency purchase page on the RALord DLS.
Ransomware-as-a-Service and encryption offering
RALord claims to operate its encryption malware, which allegedly has “anti-detection” capabilities. The site states that threat actors and groups can purchase use of this malware for €200 per attack, with the group claiming 10% of any successful ransom gained by offering a decryptor. Subsequently, posting data on the group’s blog will cost users an additional €20.
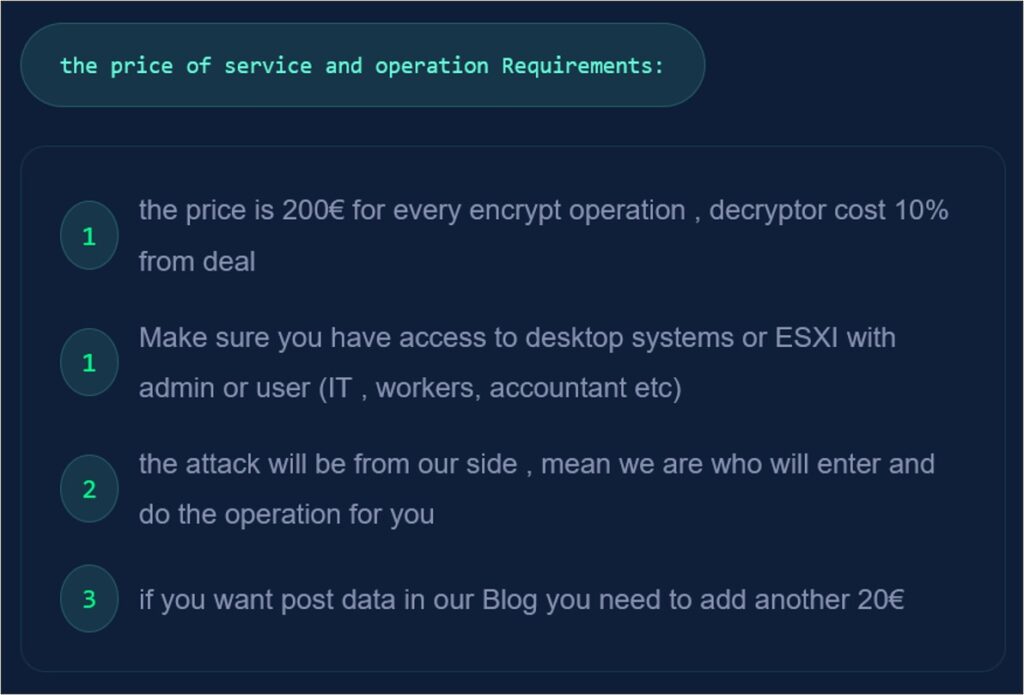
Figure 7 – The service rules given by RALord.
The group also claims to operate a Ransomware-as-a-Service (RaaS) offering. As per its DLS, any successful extortion attempt results in an 85 to 15 percent split of the payment in favour of affiliates. However, RALord states that it will conduct any encryption of impacted systems itself, with affiliates effectively operating as an initial access broker (IAB).
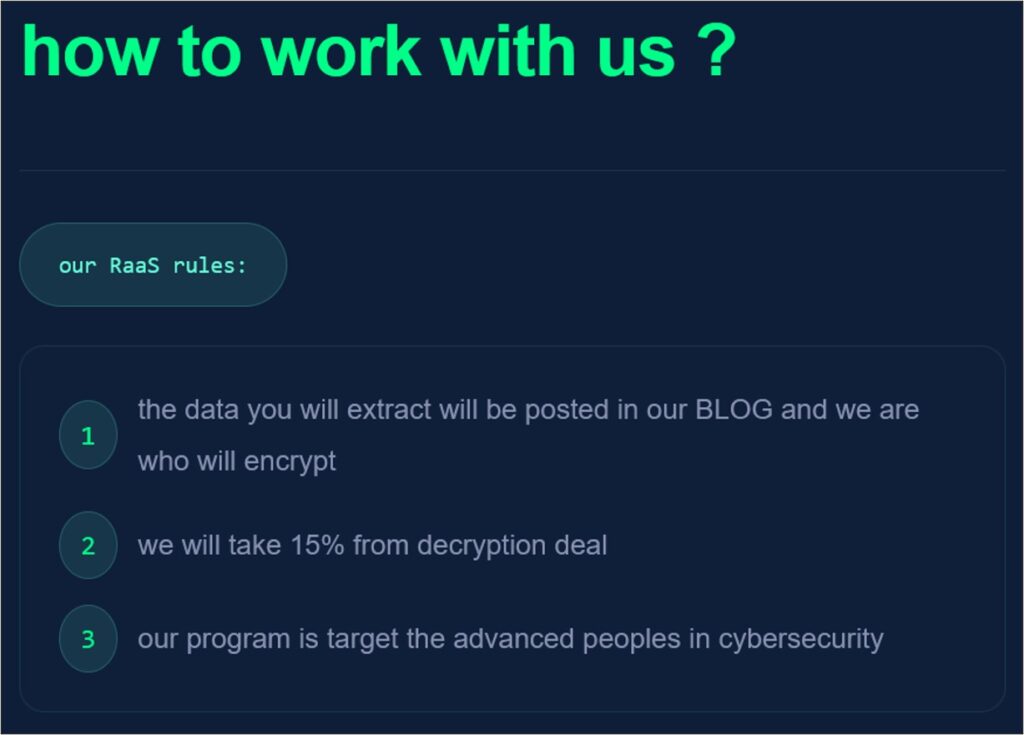
Figure 8 – The RaaS rules given by RALord
It is highly common for RaaS offerings to divide profits from a successful ransom between the ransomware provider and the affiliate using it. In most cases, ransomware affiliates are allowed to keep approximately 70 to 80 percent of profits made from a successful ransom attempt. The ransomware service provider will then take the rest to keep the ‘business’ running. CYJAX recently observed the Anubis RaaS offering an 80 to 20 percent split to its affiliates. In contrast, RansomHub originally offered a generous 90 to 10 percent split in favour of affiliates. However, the group required upfront payment. As of January 2025, RansomHub announced that it would be taking 15 percent of profits due to “rising costs”. Based on these figures, the 85 to 15 percent split offered by RALord appears to be a relatively generous offer for its affiliates.
RALord has also posted a request for initial access brokers (IABs) to make contact with the group. It is common for ransomware groups to work with IABs for ease and convenience. In February 2025, Cyjax assessed that the skill level required to conduct ransomware operations without buying access from an IAB is ten times greater. CYJAX’s full blog regarding IAB and ransomware collaboration can be viewed here.
The extortion group also allows brokers to advertise data on its DLS for €20 and claims to support adverts on the Tor-based site, albeit no price has been listed for the latter. Those looking to purchase the data are also encouraged to contact the group. This is likely RALord’s attempt at selling data privately before leaking it publicly.
Victimology
As of late March 2025, the RALord DLS lists three victims:
- French engineering school École Centrale de Nantes.
- Argentinian engineering and industrial services company Tomio Ingeniería S.A.
- Brazilian agricultural chemical product developer and manufacturer IHARA.
As of late March 2025, the group’s victims are only located in South America and Europe. Since this is a new group; it is likely that its targeting is opportunistic, and it simply has not listed enough victims to show a varied geography.
Full datasets have not been leaked for any RALord victims, with two victims having countdown timers due to expire on 9 April 2025 and 19 April 2025. Since the group is new, it is unclear what will happen when the countdown expires. Given the use of countdowns on most other DLSs, it is highly likely that this will mark the end of negotiation attempts with the victims. This may result in the full datasets from the victims being leaked. Alternatively, RALord may attempt to sell the data to a private buyer rather than leak it publicly when the timer runs out. The group may also extend the time given on the countdown to elongate negotiations.
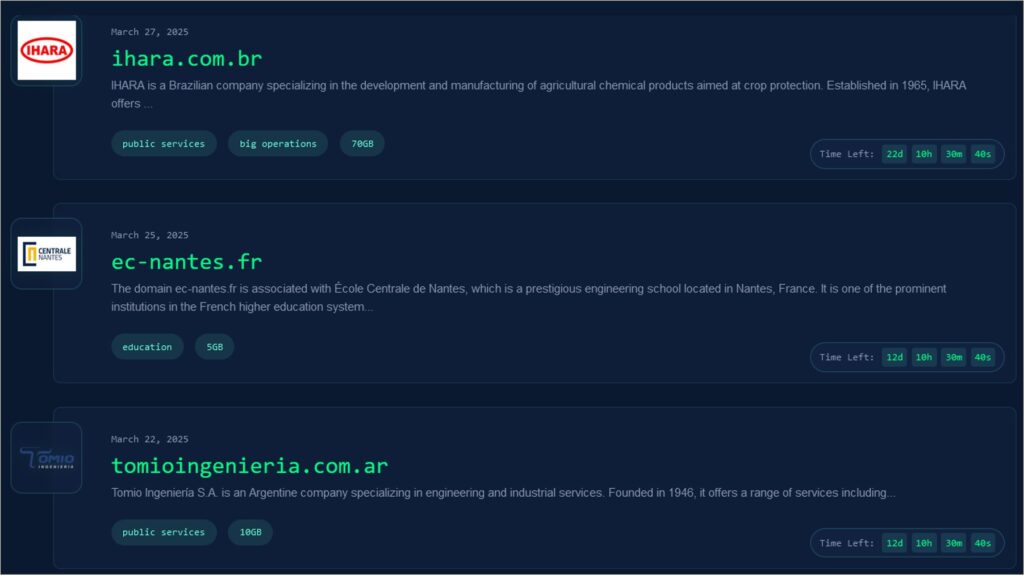
Figure 9 – The three victims listed on RALord’s DLS.
Sources available to CYJAX refer to a fourth victim organisation called Sémaphore Mulhouse Sud Alsace being linked to RALord’s extortion operation. It is a resource centre for citizens of Mulhouse, France. As of late March 2025, it is unclear why the centre is not listed on RALord’s DLS. However, there is a realistic possibility that the organisation is currently in negotiations with the extortion group or its affiliates.
Threat Assessment
Whilst RALord has named several alleged victims, none have publicly confirmed that an attack has taken place as of late March 2025. Despite this, the group’s posts contain detailed information about the types of stolen data, and it provides sample data where applicable. Additionally, the victims appear to be original to RALord and have not appeared on other group’s data-leak sites. This adds credibility to the group’s claims. It is possible that RALord has connections to other already established ransomware groups, such as RAWorld. However, this is currently unconfirmed. RALord has posted three victims in a seven-day period, meaning it is likely that the group will continue its operations in the near future.
Access our full intelligence repository containing detailed profiles like this one, covering extortion groups, advanced persistence threat groups (APTs), data brokers, hacktivists, initial access brokers, and more.
