Living Up to Its Name: Alleged Extortion Group LeakedData Begins to Leak Data

Data leaks sites (DLSs) commonly debut with a small number of claimed victims. When Cyjax discovered them, newly found DLSs for extortion groups FunkSec and Kairos claimed 11 and six victims, respectively. In contrast, a newly identified possible extortion group which aptly calls itself ’LeakedData’ has emerged onto the scene with an alleged total of 41 victims. The group, which was first observed in mid-December 2024, claims to have leaked the data of 30 organisations, with a further 11 to be leaked. Researchers have questioned LeakedData’s legitimacy as an extortion entity and have suggested that it is in fact operating as landing page for a watering hole attack which targets security researchers.
In this blog, Cyjax will explore the new LeakedData extortion group and its DLS. It will detail its operation and analyse the group’s legitimacy as an entity which conducts extortion operations.

Context
Extortion groups commonly use DLSs to further extort victims, typically proceeding in multiple stages. The first threat is that the victim’s name and news of a successful attack against it will be published on the extortion group’s website. Should this fail to motivate a victim to pay a ransom, the group’s next step is typically to provide proof of the successful theft of its data, such as screenshots of internal file trees, samples of employee or customer PII, or other sensitive documents. The group may add a countdown at this stage, noting that should the victim fail to pay by the conclusion, it will make available to DLS visitors all stolen data, either for free or at cost.
Known locations
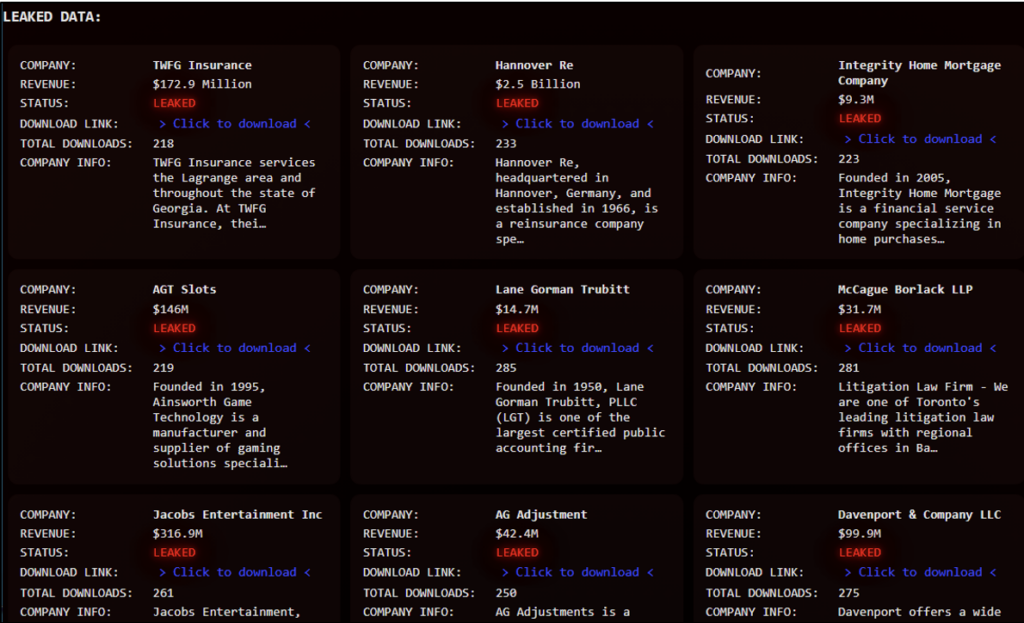
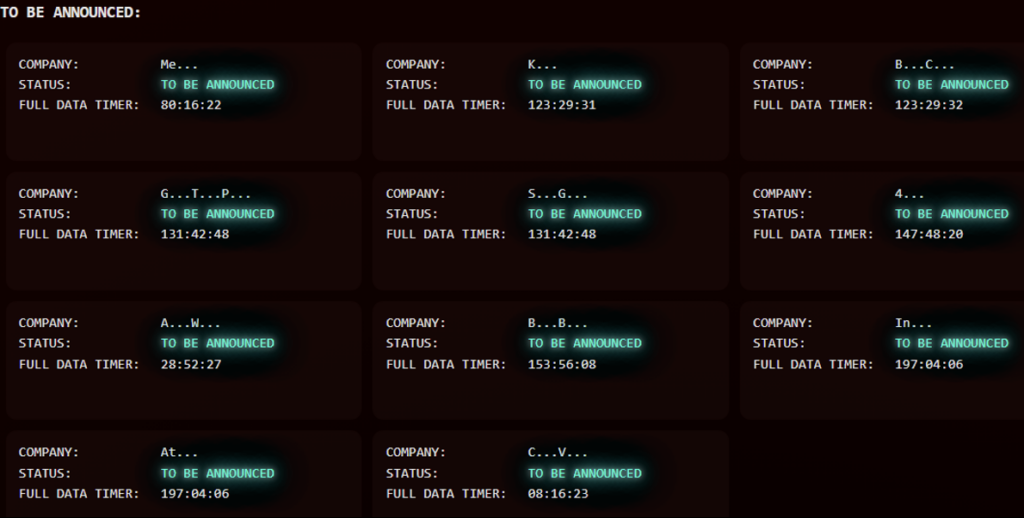
LeakedData’s DLS is a rudimentary offering, consisting of only a single page hosted on the clear web. The use of only clear web is unusual, with most extortion groups debuting with Tor-based sites. The site lists no rules, contact details for the group, or manifesto. This singular page is split into two distinct parts, one listing organisations for which the group claims to have leaked data, as shown in Figure 2, and the other hosting countdowns for leaking the data of yet unnamed victims, which is depicted in Figure 3. It appears that each claimed victim is originally listed with its name partially redacted and, after a pre-defined timer expires, the organisation’s identity is disclosed and a download link for its stolen data is shared. These links redirect to an open directory on the domain ep6pheij[.]com for file download.
The site itself appears to use Round-Robin DNS, having multiple A records pointing to different IP addresses. This works as an effective load-balancer. These IP addresses are distributed across a number of hosts in countries including Bosnia and Herzegovina, Malaysia, Mexico, Iran, and Argentina. This is commonly used to help distribute traffic, as a light anti-DDoS measure. However, in this case, it may have been implemented to add a level of obfuscation to the site’s operation.
Validity of Claimed Attacks
When LeakedData was first discovered, a security researcher shared a post on X (formerly Twitter) claiming that it was in fact a fake data extortion group. Instead, they claimed that the sole aim of the group was to deliver the Ursnif banking Trojan to researchers in a watering-hole style attack. This is a type of attack where a threat actor uses a website commonly visited by a specific target to deliver malware. In this case, a new DLS would attract researchers looking to analyse the group and deliver malware to them. The researcher then shared a screenshot of an AnyRun report which showed that ep6pheij[.]com was flagged as being connected to Ursnif and stealer malware activity.
Cyjax has conducted further investigation of the maliciously flagged URL, analysing a number of files on the DLS. From our analysis, it appears that the download URL was operated on infrastructure previously linked to Ursnif.
Cyjax conducted some dynamic analysis of this by also using the AnyRun platform. The platform flagged a Microsoft Edge process as malicious and connected to Ursnif. When looking closer at the network requests within this process, each request made to and from the IP address 186.123.165.48 was marked either as “Connects to the CnC server” or “Contacting a server suspected of hosting an CnC”.
Because of this communication, AnyRun flagged the interaction as connected to Ursnif. However, from looking at the DNS requests within the same process, it appears to be one of the Round Robin DNS resolutions for the ep6pheij[.]com domain. Looking further at the process lists, no other obvious malicious activity is present, even in instances where Word documents and PDFs are loaded.
Overall, this link between LeakedData and the distribution of Ursnif is not entirely clear. It is realistically possible that the group has used less-than-reputable hosting providers that other attackers have previously used to distribute Ursnif. It is also possible that the group itself has used, or continues to use, this infrastructure to distribute the malware.
In the absence of other corroborating factors, Cyjax cannot verify either hypothesis. However, Cyjax has not identified any other activity which looks like the delivery of Ursnif. As such, it is likely that this connection mostly comes from reported shared infrastructure between LeakedData and a previous Ursnif C2.
Despite this, the delivery of malware via criminal or unreputable data sources is not uncommon. Consequently, it is vital that safety precautions are in place to protect researchers conducting analysis.
Victimology
LeakedData’s purportedly named victims are mostly based within the United States, with a focus on the legal and financial services sectors. It is not clear if any of these organisations have confirmed attacks from LeakedData. The graphs in Figure 4 and Figure 5 show the breakdown of this victimology by country and sector.
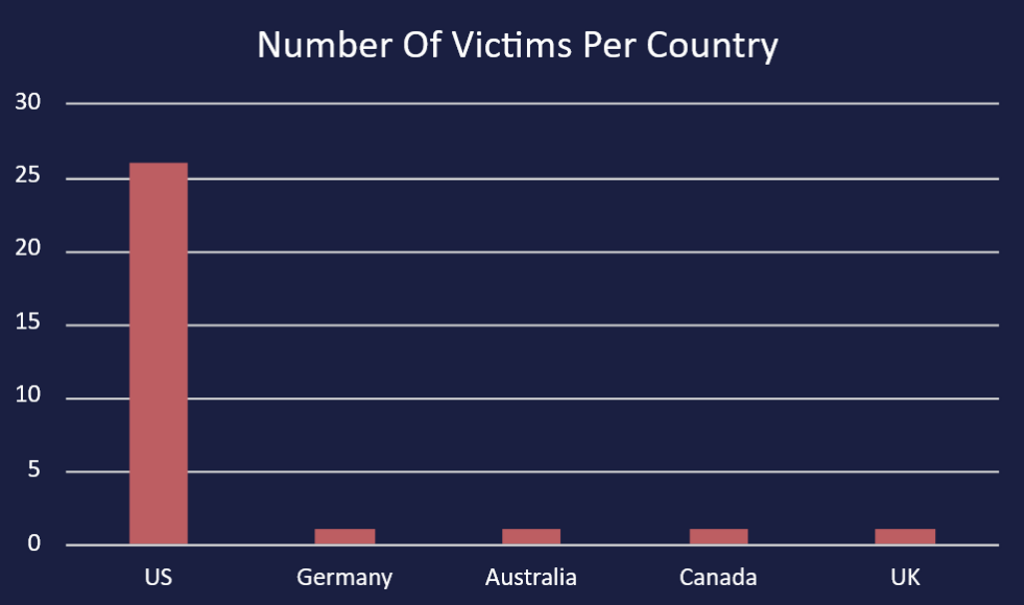

The group has a total of 30 victims that have had their data published, with this information freely available to download for any visitor to the site. Alongside this, LeakedData has 11 further victims which are “waiting to be announced”. As these victims have their names redacted, Cyjax has been unable to analyse these attacks and observe if they fit the existing targeting victimology. The site contains several notable victims, including Marriott International Inc., which has a reported revenue total of $23.713 billion. It is important to note that Marriott International previously suffered data breaches in 2018, 2020, and 2022. However, it is not clear whether the data on LeakedData’s DLS is a copy of any of these previous breaches.
Motivation
The motivation behind the group’s attacks is unclear. Though it operates a DLS, there is currently no clear evidence or even claims that the group demands a ransom. Given that LeakedData has no public manifesto, beyond the lack of targeting of organisations located in the Commonwealth of Independent States (CIS), no political motivations can be ascribed. LeakedData’s lack of contact information is very unusual when compared to other threat actors. It is unclear how exactly a victim would contact LeakedData to pay any ransom.
Threat assessment
The beginning of LeakedData’s operation has been impactful upon the threat landscape. The group has allegedly built a significant of attacks, claiming breaches against numerous US companies which operate in industries such as legal and finance on its clear web data leaks site. Despite few details being known about LeakedData’s TTPs and operation, it appears to be operating with a medium to high degree of success. However, it is not clear whether any ransoms have been paid or if any purported victims have confirmed any attacks.
As for the potential links to Ursnif and other stealers, this may affect its ability to conduct operations. If the group is legitimately sharing data, many may now be uncomfortable downloading the data or sharing it on other platforms. This would reduce the impact of the exposed data. Furthermore, this negative image may cause the group to respond publicly; however, given its lack of known social media accounts, it is not clear if this will take place. Overall, LeakedData follows the trend of many new data extortion group and is expected to potentially increase in notoriety in the following months particularly if it does conduct more attacks.
Staying Safe
This case highlights the potential dangers of operating and exploring cybercriminal locations, including DLSs. It is vital that those visiting these places have the appropriate operational security (OPSEC) posture and use a sandboxed environment to mitigate any infection.
To access our full intelligence repository containing detailed profiles like this one, covering extortion groups, advanced persistence threat groups (APTs), data brokers, hacktivists, initial access brokers, and more, click here to take a test drive of Cymon.
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
Get Started with CYJAX CTI
Empower Your Team. Strengthen Your Defences.CYJAX gives you the intelligence advantage: clear, validated insights that let your team act fast without being buried in noise.
