Introduction
In 2024, Cyjax observed the emergence of 72 extortion and ransomware group data-leak sites (DLSs). As of mid-April 2025, Cyjax has identified DLSs for 27 new groups this year, as noted in recent blogs on Morpheus, GD LockerSec, Babuk2, Linkc, Anubis, Arkana, Frag, and RALord.
The latest DLS Cyjax has identified is titled ‘anthrax14’, which constitutes one of six new sites identified in April 2025.This group appears to operate independently as an extortion operation rather than running a Ransomware-as-a-Service (RaaS) model, making no mention of hiring affiliates or encrypting servers anywhere on its DLS or on cybercriminal forums. The group is active on Russian-language cybercriminal forum Exploit. Additionally, it is also active on English-language cybercriminal forum BreachForums under the same name. As of mid-April 2025, anthrax14 is not known to be associated with any other threat actors.
It is currently unclear whether anthrax14 is a group or a single threat actor. The repeated use of first-person personal pronouns such as “I” or “me” on its DLS would suggest that it is the latter, though this could be an attempt to confuse researchers. As such, until definitive evidence emerges to suggest otherwise, Cyjax will refer to anthrax14 as a group.
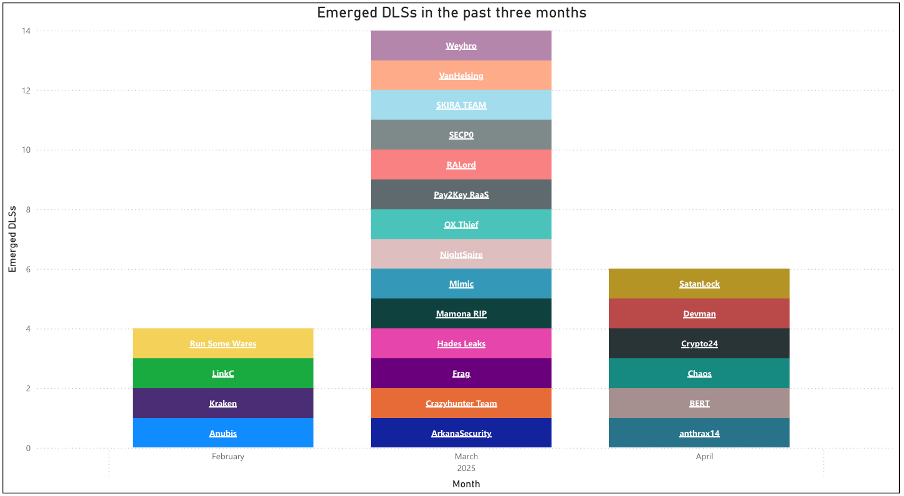
Figure 1 – DLS sites which have emerged in the past three months.
Context
Extortion groups commonly use DLSs to further extort victims, typically proceeding in multiple stages. The first threat is that the victim’s name and news of a successful attack against it will be published on the extortion group’s website. Should this fail to motivate a victim to pay a ransom, the group’s next step is typically to provide proof of the successful theft of data, such as screenshots of internal file trees, samples of employee or customer PII, and other sensitive documents. The group may add a countdown at this stage, noting that should the victim fail to pay by the conclusion, it will make available all stolen data to DLS visitors, either for free or at cost.
The anthrax14 DLS
The anthrax14 DLS first emerged in mid-April 2025, with its first post stating that the website and blog have finally been “established for future/past projects.” Its DLS is operated via Clearnet rather than the usual onion sites which ransomware or extortion groups often opt to use.
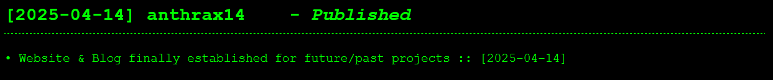
Figure 2 – First post on anthrax14’s DLS.
The site appears to be relatively unsophisticated. It is a single page which can be scrolled through, with the group’s contact details listed at the top. Its posts are in chronological order, with the newest update appearing at the top of the page.
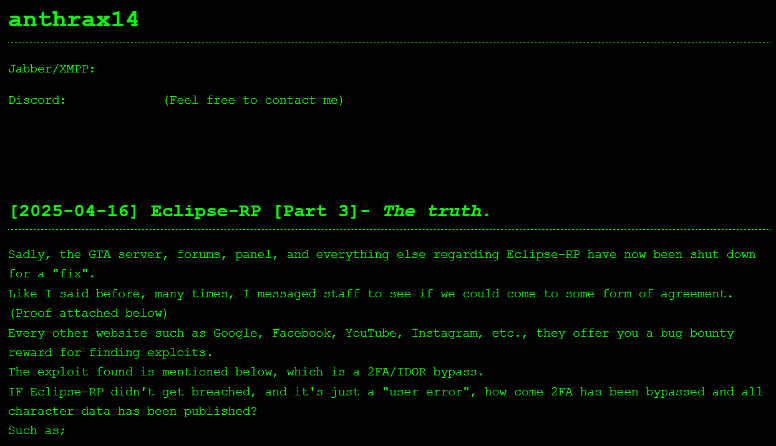
Figure 3 – Top of the main page on anthrax14’s DLS.
Victimology
The group has only listed one victim on its DLS, though it has released three posts about the organisation. Eclipse RP is a Grand Theft Auto V roleplay server equipped with voice chat so that players can interact and communicate with each other.
This threat actor named Eclipse RP as a victim on its site on 14 April 2025, with claims that the organisation’s staff and developers “are incompetent and computer illiterate.” The group claims to have compromised thousands of accounts, bypassed two-factor authentication (2FA) on the server panel, and found a possible vulnerability in the organisation’s wiki page. It has released a list of members along with their usernames as proof of the attack.
It is also currently offering to sell the 2FA and insecure direct object references (IDOR) exploit on the site. Additionally, anthrax14 is selling access to panel accounts which have credit or items on them. However, the group has offered free account access to any “GTA YouTuber who needs or wants accounts for YouTube videos on Eclipse (trolling, exposure videos, etc).” The group claims that it will also abuse some accounts itself in an attempt to find in-game vulnerabilities.
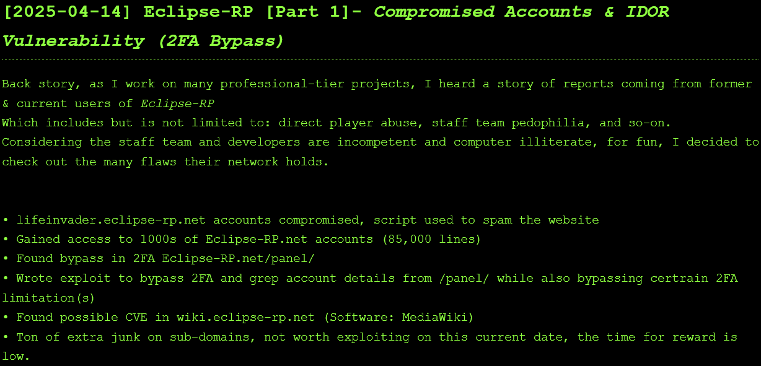
Figure 4 – Part one of the Eclipse RP data leak listing on anthrax14’s DLS.
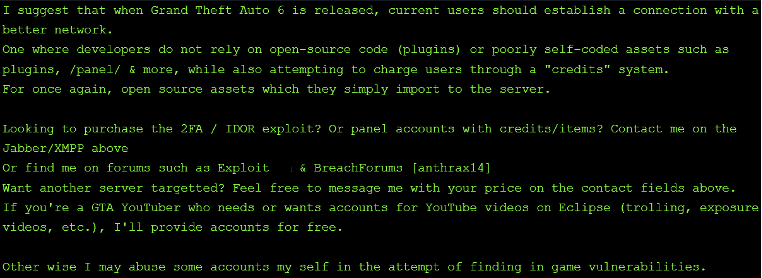
Figure 5 – Part one of the Eclipse RP data leak listing on anthrax14’s DLS.
In part two of the Eclipse RP series, the group leaked various information which it claims to have stolen. This includes 500,000 lines of data which have working login details with 2FA bypassed, 85,000 lines of stealer logs, 1,800 unique email addresses, and the IDOR/2FA exploit that it offered to sell in the first post.
The group claims that it made a support ticket to inform Eclipse RP staff of the IDOR vulnerability in the system. However, anthrax14 retracted the offer to share the information because the organisation would not provide payment. It then showed that it had access to user data and was subsequently banned from the site, resulting in the leak.
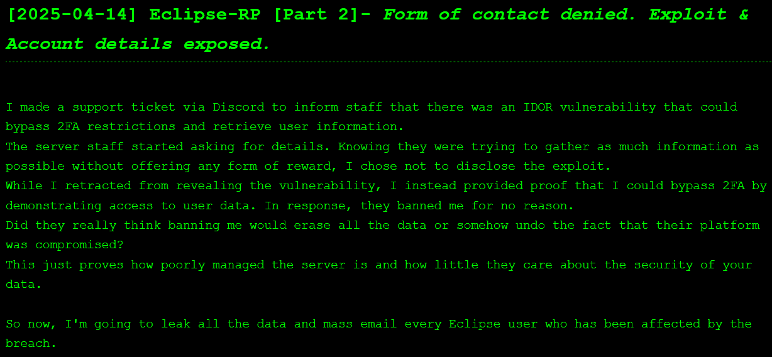
Figure 6 – Part two of the Eclipse RP data leak listing on anthrax14’s DLS.
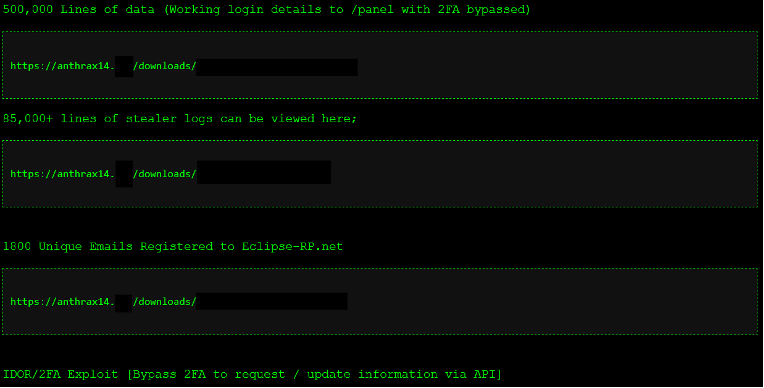
Figure 7 – Part two of the Eclipse RP data leak listing on anthrax14’s DLS.
Part three of the leak, which was posted on 16 April 2025, released further data. This included emails, usernames, passwords, and other backend account information from various users after Eclipse RP allegedly shut down its site to conduct a fix. At the time of writing, the Eclipse RP site is working as normal. The group also released the transcript of its conversation with staff, where they refused to pay a bug bounty.
The group claims that this is likely the last post about the organisation and server. It has asked users for further project ideas and who to target next.
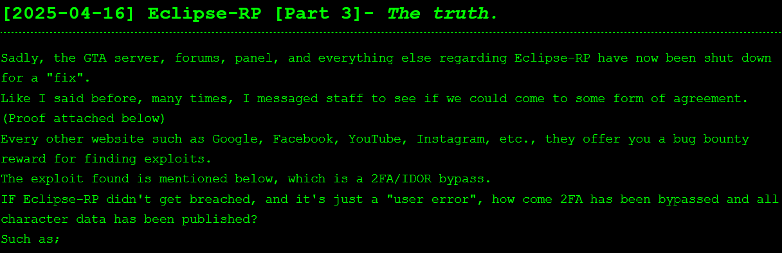
Figure 8 – Part three of the Eclipse RP data leak listing on anthrax14’s DLS.
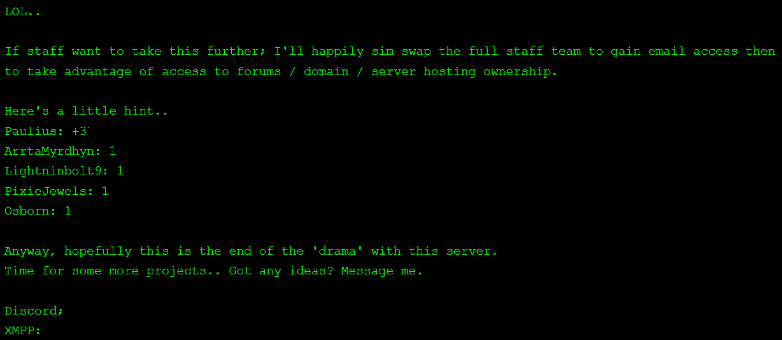
Figure 9 – Part three of the Eclipse RP data leak listing on anthrax14’s DLS.
Gaming industry targeting
The gaming industry can be a lucrative sector for cybercriminals to target. This is due to the vast amount of interconnected information which these companies often hold on users and its status as a billion-dollar profit industry. Users often have personal and financial data saved to accounts, including names, emails, card details, and addresses to allow in-game purchases. Threat actors have been known to compromise these types of accounts for in-game resources, such as purchased items or high levels.
Source code is also a popular target for threat actors because it can be used to create cheats or recreate the game before release, which could result in reputational damage. Threat actors may choose to infect it with malware and release it to unsuspecting individuals or sell it to competitors, among other damaging activity.
In February 2021, Polish game developer CD Projekt Red, which makes games such a Cyberpunk 2077 and The Witcher series, disclosed a ransomware attack by the HelloKitty ransomware group in a high-profile incident. The company refused to pay the ransom demand, resulting in data being leaked online. Several different forum posts discussing the sale of the stolen data were observed at the time, with members being highly interested in the sharing of game source code
In other known instances, US and German game developers Ubisoft and Crytek were both attacked by Egregor ransomware in October 2020. Here, the attackers leaked data from the companies, including the full source code for Watch Dogs: Legion, development tools, and the engine. Japanese game developer Capcom was also compromised by the RagnarLocker ransomware in November 2020. A large amount of personally identifiable information was released about the company’s customers, alongside other corporate documents.
These incidents show that the information stolen from gaming companies is valuable to threat actors. In particular, discussions on cybercriminal forums demonstrate the demand for this type of data.
Cybercriminal forums
The group has accounts on two high-profile cybercriminal forums. The first account is found on Russian-language cybercriminal forum Exploit under the name anthrax14. The user created this account on 11 April 2025. Whilst the account has been used to make posts over a dozen times, it currently has a community reputation of 0. This account is mainly used to comment and ask and answer questions on other threads. A small number threads and replies posted by the user host technical discussions around the exploitation of flaws and the buying of various services being sold on the forum.
In one post from 16 April 2025, anthrax14 provided links to the leaked Eclipse RP data which it had already shared on its DLS.
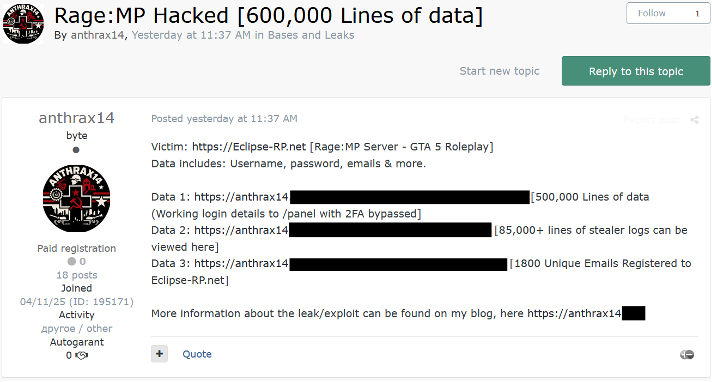
Figure 10 – Eclipse RP data leak listing on Russian-language cybercriminal forum Exploit.
In a separate post from 15 April 2025, anthrax14 asked for recommendations for a service which it could use to send data breach notification emails to 1,800 recipients. This matches the number of email addresses which the group leaked from Eclipse RP. As such, it indicates that anthrax14 is attempting to mass communicate the breach to users since it believes that Eclipse RP will not notify affected victims.
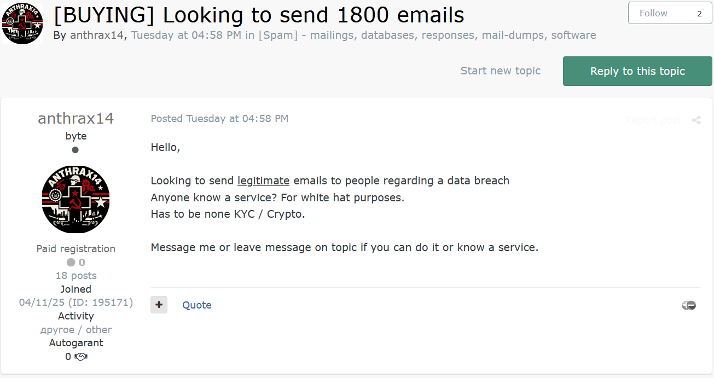
Figure 11 – The group asks for recommendations on services to send data breach notifications.
The group also claims to have an account on English-language cybercriminal forum BreachForums. At the time of writing, Cyjax is unable to confirm this because the forum has been inaccessible for several days, with no public confirmation of the cause. This is despite claims circulating on social media and cybercriminal platforms that the site has been seized by law enforcement again. Additionally, hacktivist group DarkStorm claims to have taken the site offline through a Distributed Denial-of-Service (DDoS) attack. Neither of these claims have been publicly confirmed at the time of writing.
Threat assessment
The anthrax14 group evidently has some technical skill and knowledge, with the ability to infiltrate websites and abuse various vulnerabilities. Despite this, the group makes no mention of operating as a ransomware but has rather leaked data after Eclipse RP refused to pay a bug bounty for a flaw which was exploited to steal user data. This indicates that anthrax14 is purely an extortion group which is operating for the purpose of financial gain.
Whilst the group has a very new account on Exploit, it has participated in several discussions on the forum and has created several posts of its own. This activity and its request for users to suggest new targets indicates that anthrax14 is currently committed to its operation. As such, it will likely continue to conduct attacks and data breaches in the future.
Access our full intelligence repository containing detailed profiles like this one, covering extortion groups, advanced persistence threat groups (APTs), data brokers, hacktivists, initial access brokers, and more.
Click here to take a test drive of CYJAX
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
