Introduction
As the threat landscape continues to develop, ransomware and data broker groups constantly emerge, develop, and disband. Cyjax has observed a significant number of new data-leak sites (DLS) emerge in March 2025, with a total of 14 new sites. This is the highest observed number of extortion groups which have emerged in a single month. The second highest number was observed in September 2022, when 10 data-leak sites emerged. Overall, 21 DLSs have been identified in 2025 so far.
Of these identified threat groups, some are entirely new; some were previously active and have now released a Ransomware-as-a-Service (RaaS) offering; and several have published high-profile victim data leaks. This blog aims to examine these emerged sites and highlight the ongoing trends in this area in 2025.
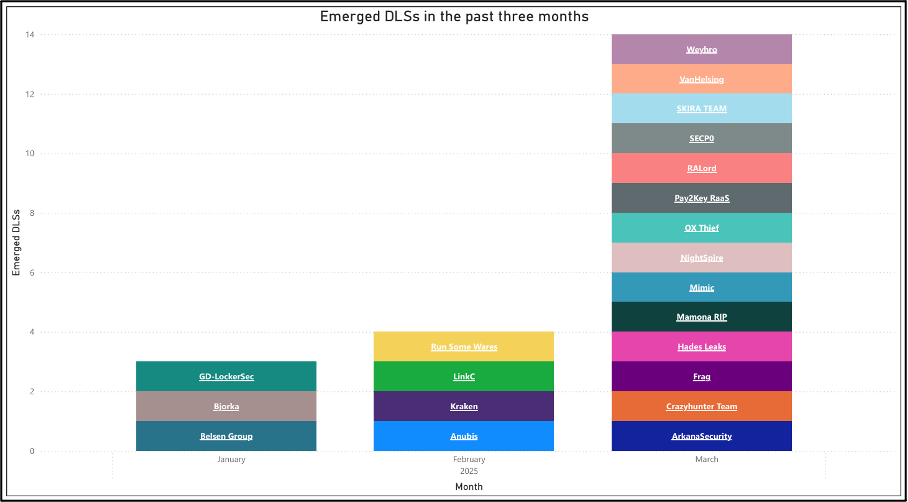
Figure 1 – Graph showing new ransomware groups per month.
Record-breaking month – March 2025
March 2025 saw the emergence of 14 new DLSs. This record-breaking number consists of new groups Mimic, OX Thief, SECP0, SKIRA TEAM, Weyhro, VanHelsing, NightSpire, Hades Leaks, Crazyhunter Team, Mamona RIP, Frag, ArkanaSecurity, Pay2Key RaaS, and RALord.
These extortion groups have collectively listed 86 victims on their DLSs as of late March 2025, highlighting the widespread targeting of organisations. Additionally, it also illustrates the impact of these new groups within the threat landscape.
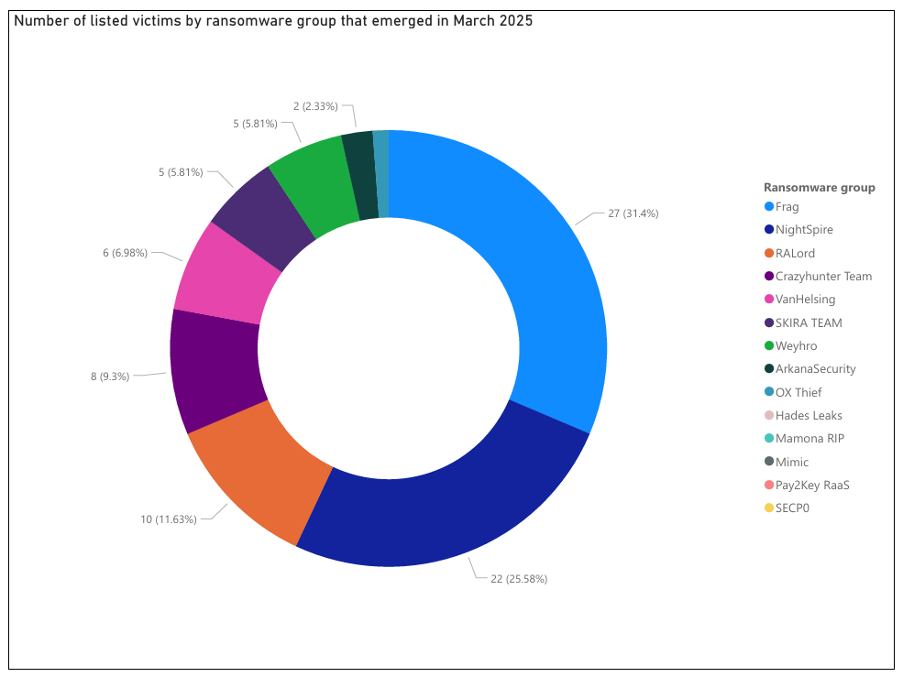
Figure 2 – The distribution of listed DLS victims in March 2025.
Notable threat groups
Cyjax has reported on new threat groups which have emerged in 2025, including ArkanaSecurity, Anubis, Babuk2, and Frag, among others. Each of these groups have entered the threat landscape with some notable activity within their operations.
ArkanaSecurity
ArkanaSecurity’s DLS first emerged in January 2025 with a post about the group, its processes, and contact details. As of late March 2025, the group’s DLS lists Wide Open West (WOW!) as its only victim. This organisation is the eighth largest cable operator in the United States. The detailed blog entry contains the name of the alleged victim, a description of files which have been leaked, a countdown timer, and details about the intrusion itself. It also includes sample images and a video allegedly demonstrating access to the organisation.
Notably, the group does not appear to have any accounts on prominent cybercriminal forums. ArkanaSecurity appears to work independently rather than as an RaaS, with no known ties to other cybercriminal groups. This contrasts with many other new groups, which tend to use a RaaS model to increase monetary gain through subscriptions and profit shares via successful extortion.
Some new groups immediately list multiple victims. However, as ArkanaSecurity appears to be operating as a standalone team and not as a RaaS, attacks may take longer to conduct. This is because only the core team will have access to the ransomware binary. As a result, ArkanaSecurity has only listed one victim on its DLS as of late March 2025.
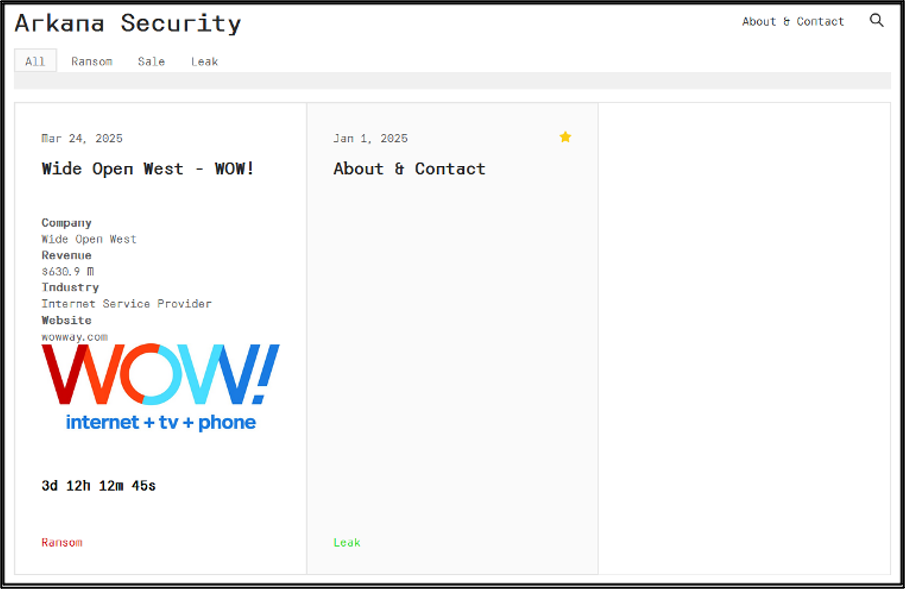
Figure 3 – AkranaSecurity’s landing page containing the WOW! listing.
Anubis
Anubis’ DLS has listed five victims as of late March 2025. Each listing contains detailed blog entries that include a description of the victim and the files that have been leaked. The group has posted DLS listings for organisations based in the United States, Peru, and Australia. One of its victims, namely First Defense Fire Protection, has confirmed a data breach.

Figure 4 – Anubis’ landing page which contains five victim listings.
Anubis appears dedicated not only to conducting extortion, but also causing reputational damage to victims. The group’s latest purported victim listing is for US-based Ambleside, a support service organisation. This victim listing contained descriptions of the alleged mental and physical abuse by staff members towards patients. Anubis used this to cause reputational damage to the organisation and provide an alleged motive for the attack.
A group’s motivations may expand beyond financial reasons. In this case, there are two main possibilities surrounding this DLS listing. Firstly, Anubis could have expanded its attacks because of public sentiment alongside financial gain. As such, it may have conducted the attack because of alleged incidents within the organisation. However, it is also likely that it may have opportunistically used data within Ambleside to create negative sentiment towards the organisation. Subsequently, this may have allowed the group to provide a narrative for targeting a vulnerable sector organisation.
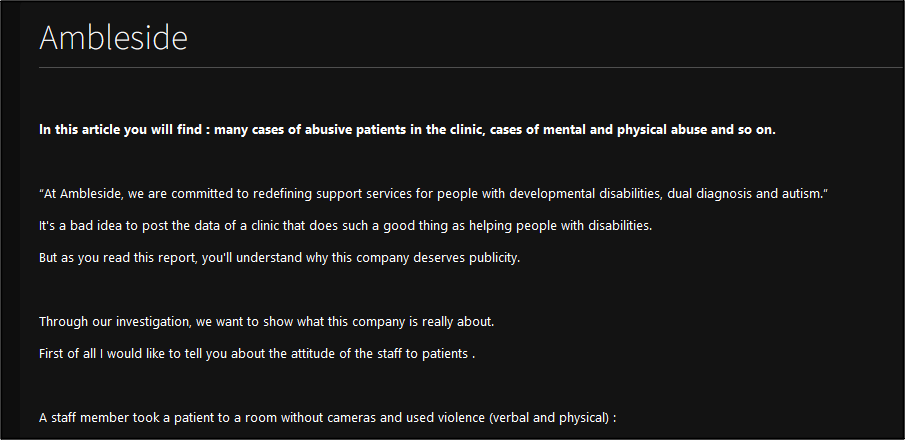
Figure 5 – Blog post for Ambleside, Inc on Anubis’ DLS.
Babuk2
A data-leak site bearing the name Babuk ransomware emerged in January 2025. It was used to state that the group has returned, with researchers naming it Babuk2 or Babuk-Bjorka. This is due to the new administrator of the blog operating as ‘Bjorka’ on cybercriminal forums and Telegram. There was scepticism about this return from the cybersecurity community, with researchers stating that the site was an impersonation of the group. Consequently, Cyjax assessed that the original Babuk group did not return. This is because victims on the site had previously been listed by extortion groups RansomHub, FunkSec, and the original Babuk.
Bjorka likely used the Babuk name to further their legitimacy rather than having a connection to the original ransomware group. At least three datasets previously leaked by Bjorka on cybercriminal forums and Telegram match listings on the Babuk2 DLS. This further indicates that this emergence falsely used the Babuk name.
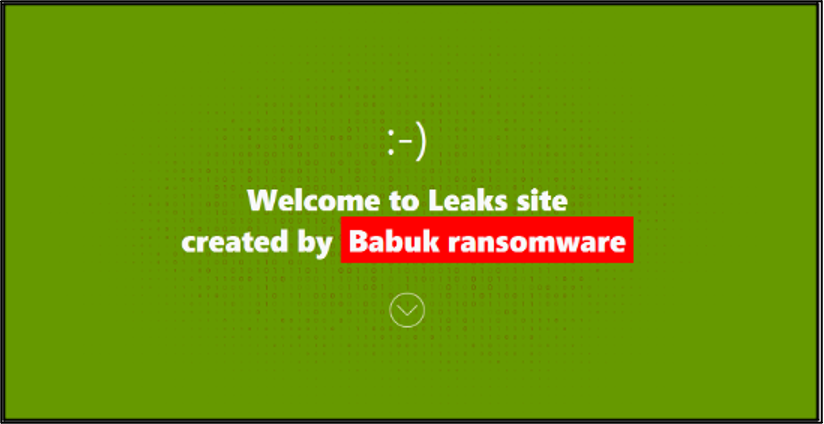
Figure 6 – Babuk2’s landing page.
Regardless of the likely false claims, Bjorka appears to have the capability to conduct ransomware attacks. The user states that they conducted a ransomware attack against a Pakistan government website. Here, Bjorka claims that they demanded a ransom amount of $500,000 and offered to sell the data to “serious buyers” for $50,000. The user purportedly conducted the attack by exploiting a zero-day vulnerability, stealing data in the form of PDFs and screenshots.
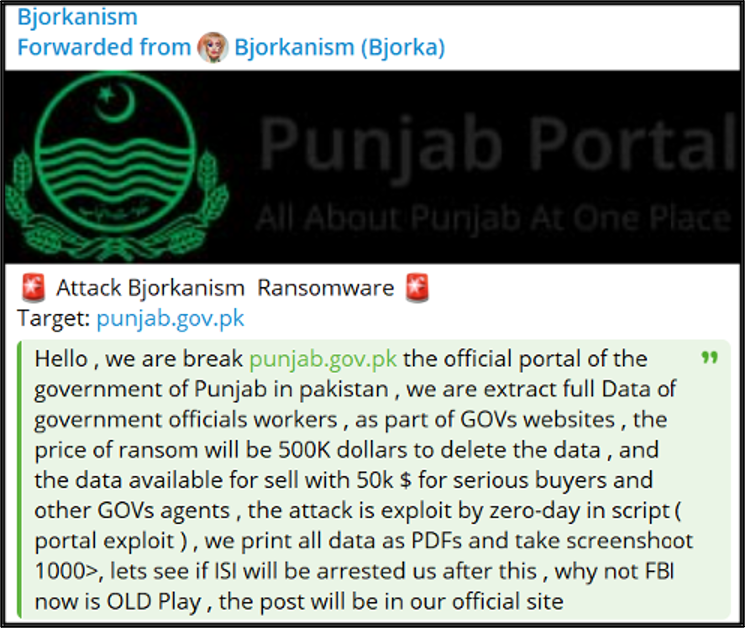
Figure 7 – Bjorka’s Telegram post claiming a ransomware attack against a Pakistan government website.
Frag
The Frag ransomware DLS first emerged on 28 February 2025, with the group listing a US-based manufacturing organisation as its first alleged victim. As of late March 2025, Frag has listed 27 alleged victims in the space of one month. This shows that the group is highly motivated and capable of compromising many organisations within a short period of time. However, it is also possible that Frag compromised these networks before the DLS was released. As such, the alleged victims may have been added after an incident occurred.
Frag provides detailed blog entries for each alleged victim, including its name, location, industry vertical, the types of data stolen, and sample files. Unlike other known ransomware groups, Frag does not provide a countdown timer to indicate when full datasets will be leaked.
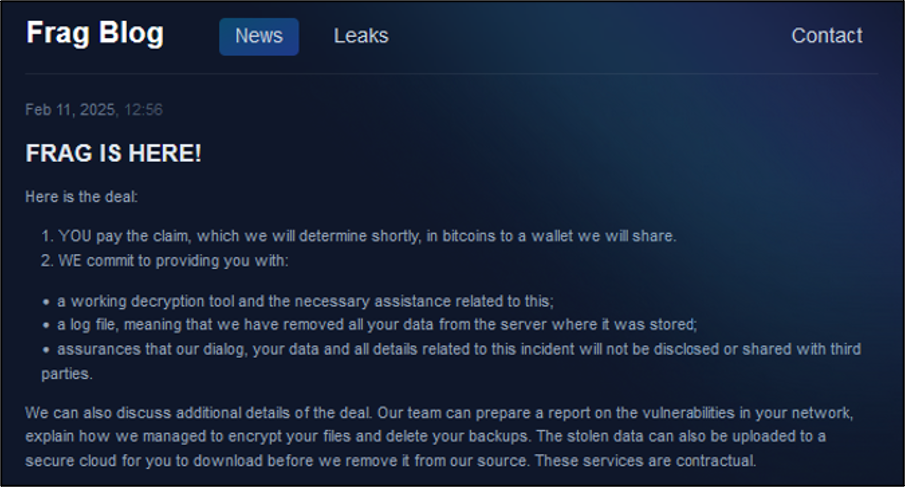
Figure 8 – The News section on Frag’s DLS.
Of the victim listed on Frag’s DLS, 25 of the 27 are based in the US. This indicates that the country is a key geographical area for the group, something which is often seen in ransomware groups and initial access broker (IAB) listings for several reasons. As the most prolific cybercriminal forums are Russian language, targeting countries in the Commonwealth of Independent States (CIS) is strictly prohibited. As such, threat actors operating within these locations target enterprises based in what Russia perceives to be its principal adversary. However, Frag has no known connections to cybercriminal forums, though the group may be Russia-based or operating in the CIS.
Pay2Key RaaS
Pay2Key ransomware has been active since at least 2020 and was first identified after a large number of Israel-based organisations reported ransomware attacks. The group maintained a Tor-based DLS and listed seven organisations in 2021. However, this site has since been inactive and as of late March 2025, does not resolve.
On 25 March 2025, a user on a prolific ransomware-focused cybercriminal forum advertised a RaaS project named Pay2Key. However, it is not clear whether this is the same group, and the user allegedly provides free registration to the RaaS panel.
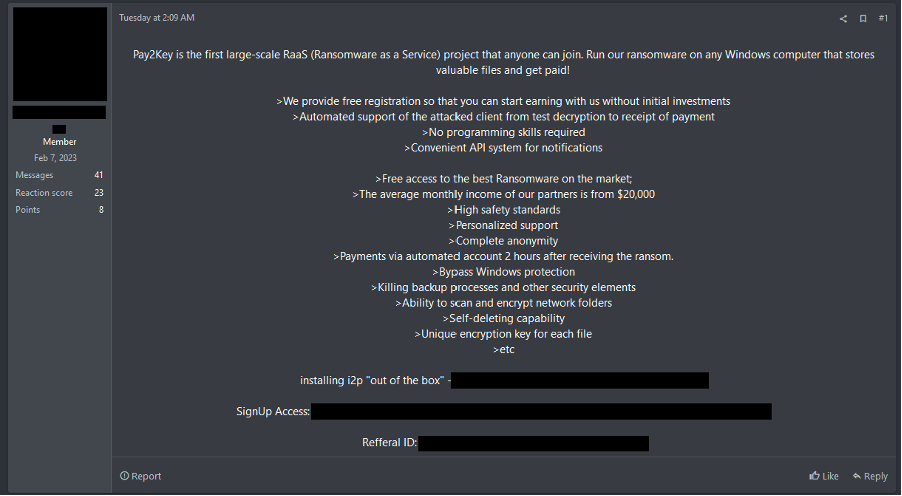
Figure 9 – Pay2Key RaaS advert on a cybercriminal forum.
Notably, the sign-up link provided in the post was an I2p-hosted site rather than Tor-hosted. I2P is a decentralised anonymous network; however, it cannot be used to access Clearnet services. This provides a more specialised area of operation and adds credibility to the group’s claims.
This user has previously advertised several ransomware builders with varied names, including EyeLocker, Legion, ZagreuS, and Nevermore. This suggests that the user may be sharing cracked or leaked versions of the builders, rather than operating the RaaS. This is further implied through the user’s replies to other members of the forum, stating in one post that “this tool is modified based on a source that leaked online.” (Translated from Russian)
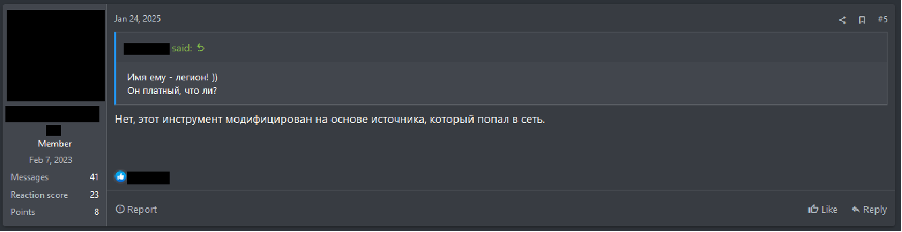
Figure 10 – Forum user’s response in a thread sharing the Legion ransomware builder.
Longevity of new groups
As explored in Cyjax’s previous blog regarding DLS emergence, some groups appear to remain active for around a month before disbanding or rebranding. Additionally, newer threat groups may not have a DLS as they are not necessary to conduct extortion attacks. However, most choose to create a DLS to advertise leaked data, cause reputational damage to victim organisations, and gain a reputation. It also means that groups can provide a centralised resource for victim communication and data leak notifications.
A number of newly emerged threat actors have notably decided to use the branding and reputation of long-standing and prolific ransomware groups. This is likely in an attempt to increase their own reputation, identity, and credibility. A prime example of this is Babuk2 and Bjorka. Whilst Bjorka may not be a Babuk member, they have posted legitimate data leaks from organisations not claimed by other threat groups. This highlights that the user likely conducted several successful attacks and is capable of compromising enterprise networks. However, Bjorka masqueraded as a prolific group to appear like a credible threat within the cybercriminal community.
Threat actors often discuss general trends and debate the threat landscape on cybercriminal forums. Cyjax has observed discussion of the increased DLS emergence rate on a prominent English-language cybercriminal forum, highlighting the general consensus towards new groups. The author of the post within Figure 11 claims that approximately 90% of new groups are “a bunch of skids in costumes”, which refers to unskilled individuals masqueraded as professional threat actors with successful operations. The user continues to show negative sentiment towards new groups. In particular, the user accuses new RaaS operations as having AI generated binaries which are sold under a highly priced subscription model.
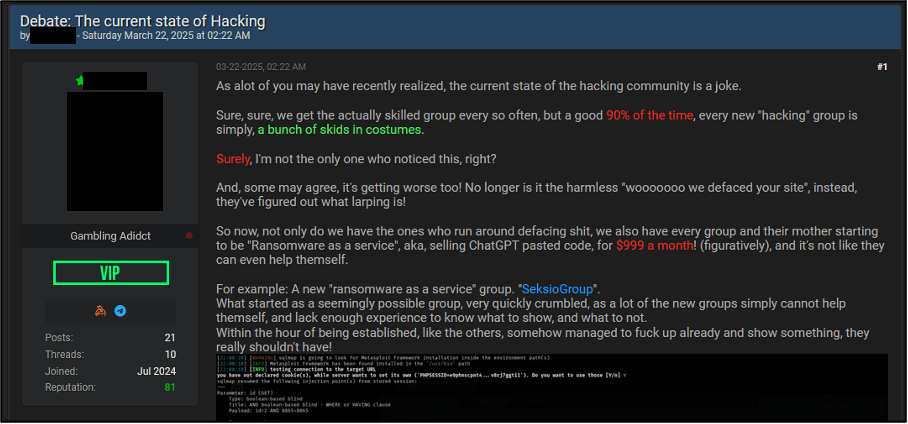
Figure 11 – Cybercriminal forum post on the current state of hacking.
This sentiment appears to be shared with other members of the forum, with one user replying that the state of hacking has become a “playground for script kiddies”. These individuals have been labelled as “inexperienced wannabes who slap together some half-baked code throw on a spooky mask and call themselves a “group.””.
Whether this sentiment is true, notable threat groups identified in 2025 have listed prominent and impactful organisations on their DLSs. This highlights that regardless of skill level and reputation, new groups can conduct attacks against organisations and monetise operations through ransom demands and extortion.
Conclusion
New threat actors and extortion groups seem to be appearing at an increased pace, as the next generation of attackers appears to be developing. The extortion market is unsaturated; therefore, any new groups can have a wide range of potential target organisations. This is something that will only increase in the future. As there will always be more organisations to extort, the constant emergence of new threat groups is unlikely to stop.
It is vital to monitor the emergence of new extortion groups, particularly because they pose a significant threat to organisations of all sizes. Whilst these new attackers may not become permanent fixtures within the threat landscape, they remain highly motivated and are compromising organisations at a high pace. Alongside this, they remain innovative and extort victims for high ransom prices, as well as often finding other forms of monetary gain by selling data leaks to other attackers. As such, it is vital that organisations assess the threats posed by these new groups.
Cyjax monitors DLS emergence and victims allegedly compromised by these threat groups. To access our full intelligence repository covering extortion groups, advanced persistence threat groups (APTs), data brokers, hacktivists, initial access brokers (IABs), and more, click here to take a test drive of Cymon.
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
