Key takeaways
- Cyjax discovered 104 unique IAB listings on cybercriminal forums selling access to organisations in a variety of sectors in the Middle East – most of which were based in the UAE.
- There were at least 63 claimed ransomware attacks targeting Middle Eastern organisations in 2024, the majority of which have been attributed to the LockBit and RansomHub ransomware groups.
- Middle Eastern IT and manufacturing sectors were targeted most often by ransomware groups during the period.
- Israel was by far the most targeted country in the Middle East by hacktivist groups in 2024, likely due to the ongoing Israel-Palestine conflict. This was followed by the UAE, Saudi Arabia, and Jordan.
Introduction
This report will provide an overview of the various extortion groups, hacktivists, and initial access brokers (IABs) targeting the Middle East throughout 2024 and highlight the relevant observed trends. Specifically, this report will look at incidents affecting Egypt, Iran, Iraq, Saudi Arabia, Yemen, Syria, Jordan, United Arab Emirates, Israel, Lebanon, Oman, Kuwait, Qatar, and Bahrain.
Extortion
Extortion attacks, including ransomware and data-leak incidents, are one of the largest and most costly cyber threats which organisations worldwide are facing in the current threat climate. Groups continue to target organisations opportunistically rather than conducting sector-specific targeting, though some threat actors engage in ‘big game hunting’ and are more selective with their victims. It is extremely common for most ransomware groups, both established and new, to use a double extortion model in attacks. Here, the groups steal sensitive data from targeted systems prior to encryption and threaten to leak it on a public-facing DLS if the ransom is not paid.
Middle East Focus
Cyjax tracks the data-leak sites of the main ransomware groups currently in operation. Between 1 January and 31 December 2024, Cyjax recorded at least 63 total attacks which solely targeted organisations in the Middle East.
Cyjax’s findings show that the LockBit and RansomHub ransomware groups listed the most attacks against Middle Eastern countries on its data-leak site in this period. Specifically, 22.22% of ransomware attack claims against the Middle East in 2024 were attributed to each group. This is followed by MalekTeam with 12.69% of attack claims. However, it should be noted that LockBit often posts both new and old listings on its DLS. As such, these figures may not purely represent new victims.
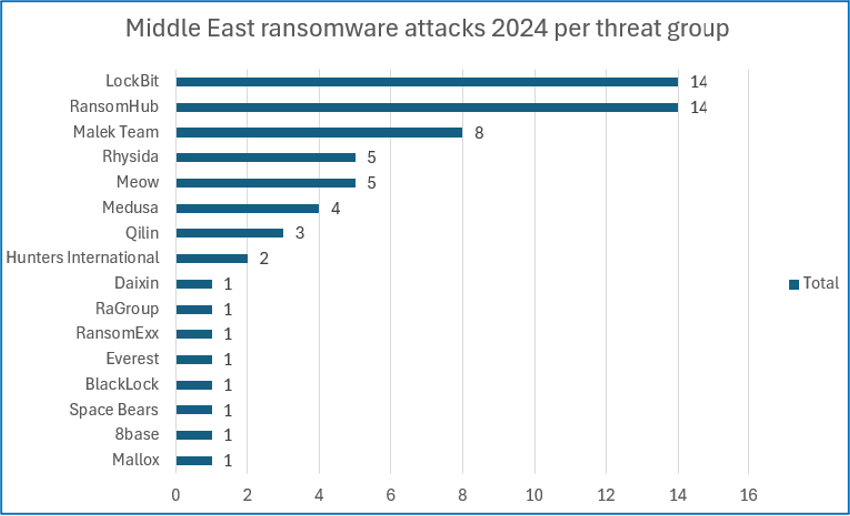
LockBit
LockBit is a Russian-speaking Ransomware-as-a-Service (RaaS) group which likely formed in September 2019. The group has targeted almost 2,000 organisations with large revenues in a range of Western geographies and industry sectors. This threat actor practises double extortion whereby it extorts its victims for a ransom after encrypting files and directories with bespoke cryptoviral ransomware and exfiltrating sensitive data. It then shares this data on its data-leak site (DLS). The group runs a Ransomware-as-a-Service affiliate programme where its operators provide the ransomware to affiliates, who carry out attacks in exchange for a percentage of the ransom profits.
In mid-February 2024, law enforcement organisations from 11 countries conducted a takedown operation named Operation Cronos. As a result, the LockBit data-leak site (DLS) was seized by the National Crime Agency (NCA). Despite this, the group continues to release attack announcements.
Overall, LockBit is a highly credible ransomware group which poses a significant threat to organisations it wishes to target. Due to its large affiliate network, the group can conduct a large number of attacks by providing its highly technical tooling to multiple different hackers. Combining this with the powerful nature of its customised tooling, as well as the wide range of attack techniques, LockBit is a complex threat actor to defend against. This is only further exemplified when factoring in its numerous evasion techniques, rendering several traditional defences ineffective. Alongside this, the number of developments made with the original LockBit malware, such as LockBit Black and Green, show the group’s ability to change and develop its tactics and tooling as the security landscape changes.
RansomHub
RansomHub is a financially motivated ransomware group which likely formed in February 2024. The group operates a Ransomware-as-a-Service (RaaS) model, whereby the developers of the ransomware lease it to affiliates, who conduct the ransomware attacks and in return provide the developers a share of the ransom. RansomHub affiliates have targeted small to large enterprises in the marketing, media, hospitality, government, military, education, transportation, FMCG, agriculture, healthcare, sports, energy, professional services, information technology, retail, real estate, pharmaceutical, manufacturing, telecommunications, and financial sectors. Its victims span across Asia, the Pacific, South America, North America, Europe, the Middle East, and Africa. RansomHub affiliates practice a double extortion method involving file and directory encryption, as well as sensitive data exfiltration. RansomHub maintains a data-leak site (DLS), where it publicly names victims that have not complied with ransom demands and offers visitors the opportunity to obtain the data for a price.
The group uses cybercriminal forums and its DLS to recruit affiliates. RansomHub claims to be linked to Cuba, North Korea, China, and nations within the Commonwealth of Independent States (CIS).
The data of at least two alleged victims was allegedly successfully sold from the group’s DLS, and several victims have confirmed attacks. Additionally, some of these victim organisations operate in vulnerable sectors, including healthcare, government, financial, and energy. This heightens the level of risk posed by the group. Furthermore, RansomHub maintains a sophisticated DLS and has displayed a keenness to engage with experienced ransomware affiliates. It has also demonstrated a high level of technical capability, as the group has been able to customise the sophisticated Knight ransomware strain for its own purposes. RansomHub has shown a keen ability to exploit several vulnerabilities to gain unauthorised access to victim systems. This has been combined with the misuse of legitimate remote service tools and software such as Splashtop and AteraAgent, which adds further credibility to the capabilities of both the group and its associates.
Ransomware attack frequency
Cyjax has also assessed the frequency of recorded ransomware attacks in 2024 which targeted the Middle East. On average, five ransomware attacks were conducted in the region per month, with the lowest rate of attacks seen in January (two listings on DLSs) and December (one listing on DLSs). The highest rate of attacks was observed in October, which saw 71 organisations named on data-leak sites monitored by Cyjax.
It is possible that this relates to the origin of several known ransomware groups being in Russia and CIS countries. Many Russian-speaking cybercriminals have the tendency to pause operations from December and into the month of January due to the country celebrating Christmas on 7 January. Christmas is celebrated on this date in several Orthodox countries, including Russia, Serbia, Ukraine, Montenegro, Moldova, and Belarus due to the religious calendar following the old-standard Julian calendar. This means that 25 December corresponds to 7 January on the Gregorian calendar followed by most other Western countries. This would explain the low number of attacks in the first and last year of the month.
Attacks per Country
Cyjax found that Israel and the United Arab Emirates were the most targeted countries in the Middle East in 2024, making up 41.27% and 38.1% of attacks, respectively. This was followed by Bahrain, Oman, and Lebanon, with 4.76% of attack claims each.
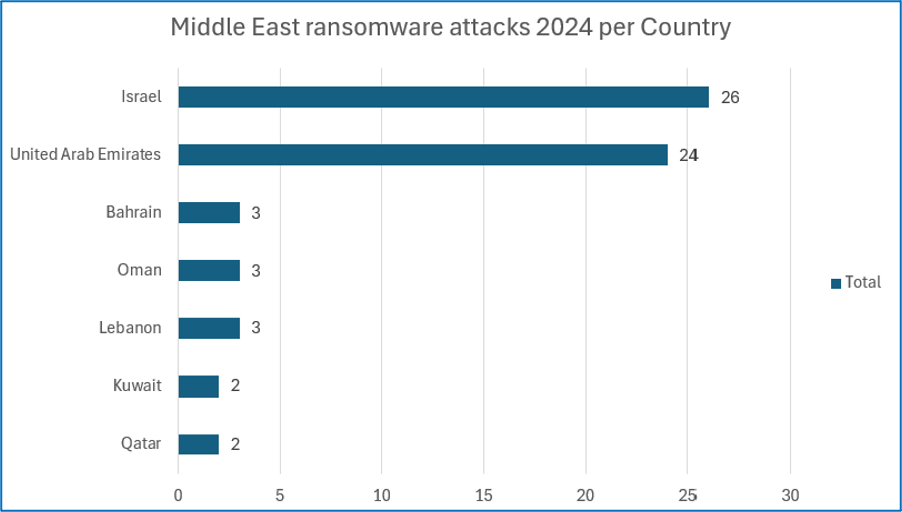
Sectoral targeting
Whilst analysing attacks against the Middle East in 2024, Cyjax uncovered that IT was the most targeted sector with 17.46% of attack claims pertaining to companies in the sector. This is closely followed by the manufacturing sector which had 15.87% of attack claims, and financial and professional services with 7.94% of attack claims each. Other targeted sectors included education, healthcare, legal, real estate, government, automotive, energy, media, sports, telecommunications, retail, infrastructure, military, FMCG, tourism, and maritime. The wide variety of targeting is due to ransomware attacks often being opportunistic in nature. Consequently, all sectors are vulnerable to potential compromise if their systems contain unpatched flaws or misconfiguration.
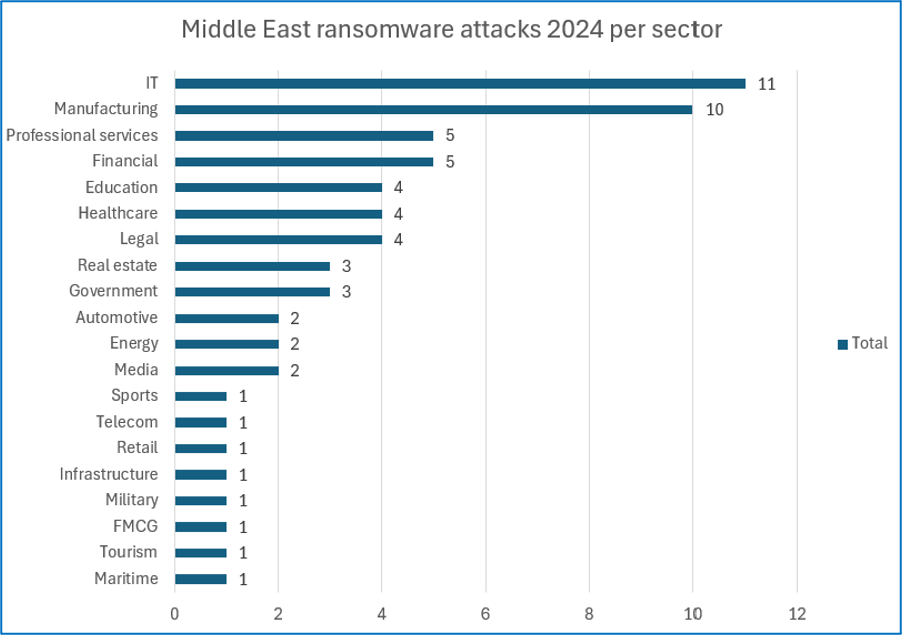
Whilst there are some groups that will not attack certain critical sectors such as healthcare, government, or critical infrastructure, likely due to fears of law enforcement action, most attackers will target sectors indiscriminately. Several critical sectors, including healthcare, infrastructure, and maritime, were allegedly compromised in 2024.
One such company is UAE-based Gulf Energy Maritime, which provides marine transportation for energy markets across the world. This organisation was allegedly compromised by the RAGroup. Another is Lebanon-based TETCO group, an infrastructure organisation which fabricates material to the management of projects in the oil and gas industry. This organisation was allegedly compromised by RansomHub. Targeting these types of organisations can cause a domino effect of supply-chain issues, resulting in disruption to the energy sector. This especially occurs if the group encrypts company systems. Furthermore, it could result in confidential and secret data from the company, or its clients being compromised and leaked to the public should an organisation choose not to pay a ransom.
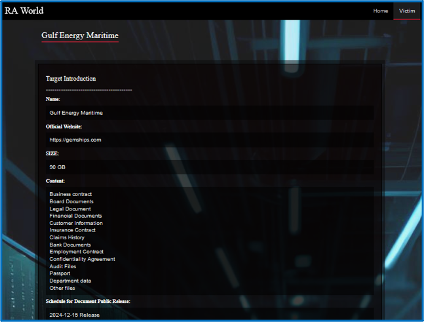
Figure 4 – RansomHub and RAGroup data-leak posts claiming attacks against Middle Eastern organisations.
Initial Access Brokers (IABs)
Cyjax conducts monitoring regarding the advertisement of initial access to corporate networks across the most prominent Russian- and English-language cybercriminal forums. Initial access brokers (IABs) do not typically name the organisations to which they advertise access, instead providing geographic, sectoral, revenue, and other types of information.
Initial access brokers form a key part of the cybercriminal ecosystem. They facilitate access for ransomware groups, data leakers, and advanced persistent threat groups (APTs) into corporate networks. They are highly specialised, professional, and operate in an established, lucrative market often characterised by rigid rules and conventions. Every ransomware attack or data breach begins with initial access, following the reconnaissance phase of an attack. For a fee, IABs enable other threat actors to enter an organisation’s networks.
Initial access brokers targeting the Middle East
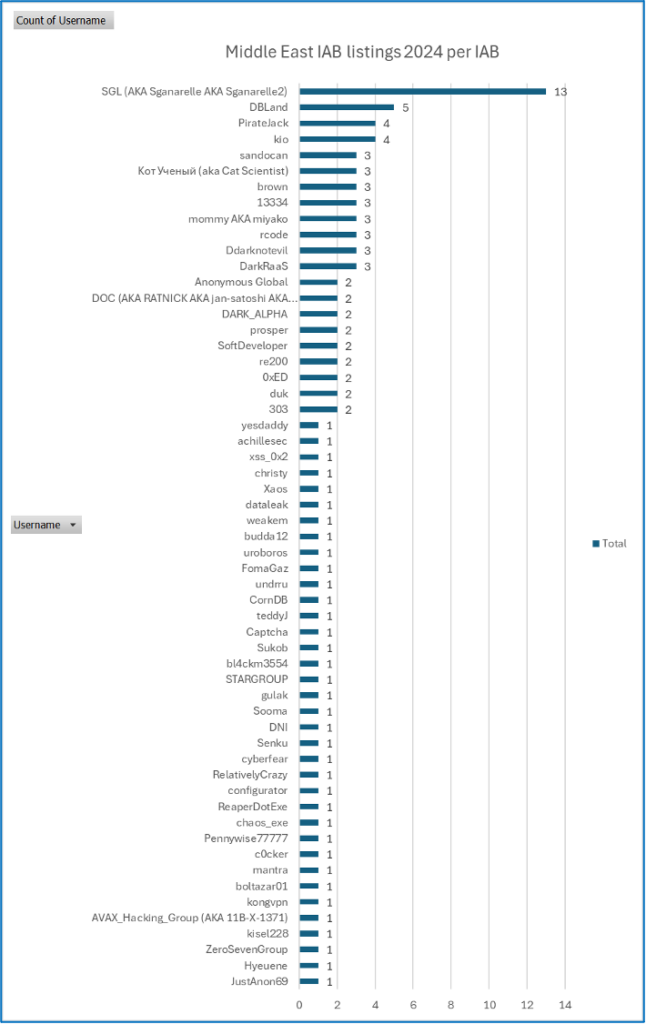
In 2024, Cyjax uncovered 104 IAB listings for Middle Eastern organisations from 57 different brokers. Of these listings, 12.5% were made by a user known as SGL, also known as Sganarelle. This is followed by DBLand, who made up 4.81% of listings, and PirateJack and kio, who made up 3.85% of listings each.
SGL
SGL, also known as Sganarelle, is an English-speaking initial access broker (IAB) which likely began advertising initial access to corporate networks on 10 August 2023. This IAB has been active on prominent Russian-language cybercriminal forums Exploit and XSS since August 2019. SGL has primarily advertised RDP and VPN accesses with domain user privilege levels to organisations in the United States and Spain. However, information around sectors is unavailable as their listings often do not contain those targeted. Whilst no information regarding SGL’s TTPs is available, it likely uses phishing or brute forcing software to gain access and harvest credentials.
SGL has posted a multitude of initial access listings on Exploit and XSS. These listings vary in geography, access level, and organisational revenue. It appears to be a highly credible broker, with a significantly high reaction score and very few negative reviews. The IAB has several won arbitrations and has regularly contributed to various threads outside of their own on the forums. The user also has at least 14 escrow deals, a number that cannot be forged. This indicates that at least 14 listings have been successfully sold, corresponding to the number of listings on the “Corp accesses” thread which have been edited to indicate a sale. SGL also appears to be technically capable and is able to consistently gain access to organisations, particularly through RDP and VPN access, whilst maintaining anonymity.
Listings per country
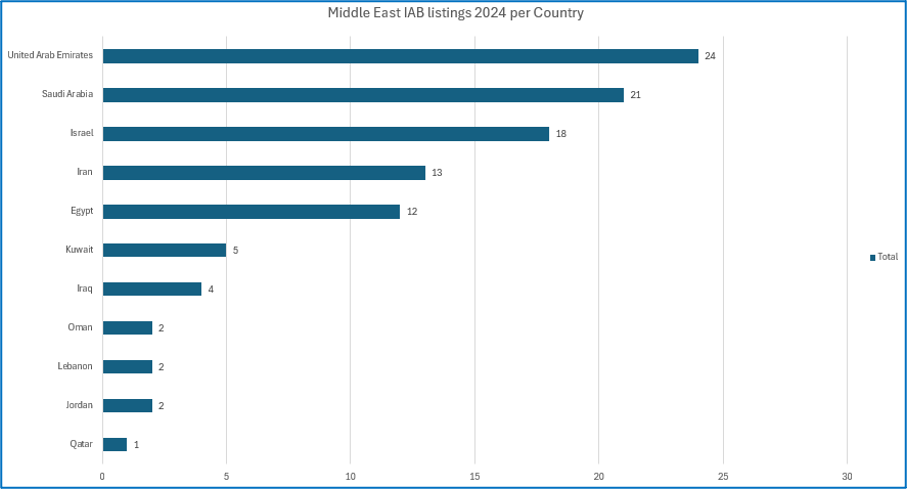
Cyjax found that in initial access listings, the most commonly targeted organisations were based in the United Arab Emirates, making up 23.08% of listings. This is closely followed by Saudi Arabia (20.19%), Israel (17.31%), Iran (12.5%), and Egypt (11.54%).
Initial access is an opportunistic market, with brokers finding victims of opportunity that are vulnerable to certain flaws or that can be easily compromised. It is unclear whether these countries were specifically targeted or whether they were opportunistic in nature.
Targeted sectors
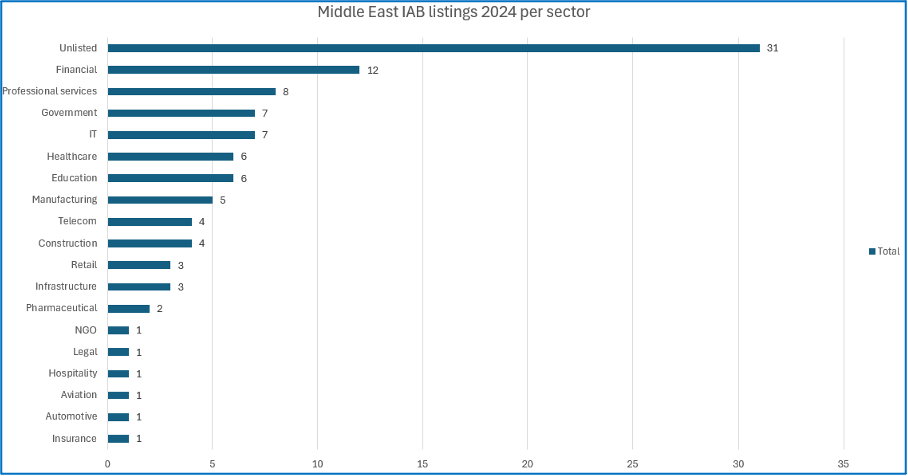
Middle Eastern organisation sectors which have been listed by initial access brokers (IABs) are not always named in the posts. In 2024, there were 104 Middle Eastern organisations listed by IABs, though 31 of these did not list a specific sector or organisation. Finance was the most targeted sector with 11.54% of listings pertaining to it. This was followed by professional services with 7.69% of listings, as well as government and IT with 6.73% of listings each.
Other targeted sectors include insurance, automotive, aviation, hospitality, NGO, legal, pharmaceutical, retail, infrastructure, construction, telecommunications, manufacturing, healthcare, and education. Due to the aforementioned opportunistic nature of IABs, specific sectors are not often targeted. This results in a wide range of sectors being listed.
Whilst IABs do not usually list the name of the organisation that they are offering access to, 11 of the 104 listings in 2024 named a specific company:
- Taqatpay – listed by c0cker.
- Orange Egypt – listed by DARK_ALPHA.
- Emirates Health Services – listed by DBLand.
- Kuwait Central Agency for Information Technology – listed by DBLand.
- Sharjah Customs UAE – listed by DBLand.
- UAE Ministry of Health and Prevention – listed by DBLand.
- Holly Makkah – listed by Hyeuene.
- Emirates Investment Bank – listed by JustAnon69.
- Jm3eia – listed by kisel228.
- Sepantafilter – listed by Senku.
IABs often obfuscate the true name of the organisation to prevent researchers from alerting the victim to the access sale. This is so that malicious activity can be conducted on the infected network or device. However, there are cases, as evidenced above, in which the brokers name the victim in the listing. This could be for several reasons, such as the victim organisation being of particular interest or value, such as a government sector organisation or an otherwise high-profile victim that may increase the price the IAB can charge for the access. Alternatively, the organisation might be named because the IAB is new or inexperienced. As such, they may not be aware of the potential operational security issues that come with naming the victim, potentially compromising the longevity of their access.
Most prominent locations
In 2024, 52.85% of the IAB listings uncovered by Cyjax targeting the Middle East were found on Russian-language cybercriminal forum XSS. Following this, 27.88% of listings were found on English-language forum BreachForums, 11.54% were found on Russian-language cybercriminal forum Exploit, and 6.73% were found on Russian-language cybercriminal forum RAMP.
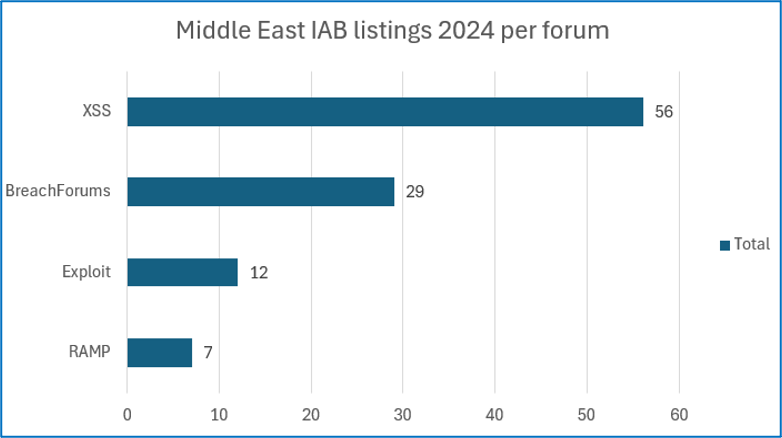
XSS and Exploit are the two most prominent forums on the market. They are characterised by longevity, strict rules, and competent forum administration and moderation teams. Both forums are both predominantly Russian-speaking and have been running since 2013 and 2005, respectively. RAMP is also a high-profile Russian- and English-language cybercriminal forum, which is used to focus on the ransomware industry. BreachForums is also a high-profile cybercriminal forum but is predominantly in the English language.
Initial access types
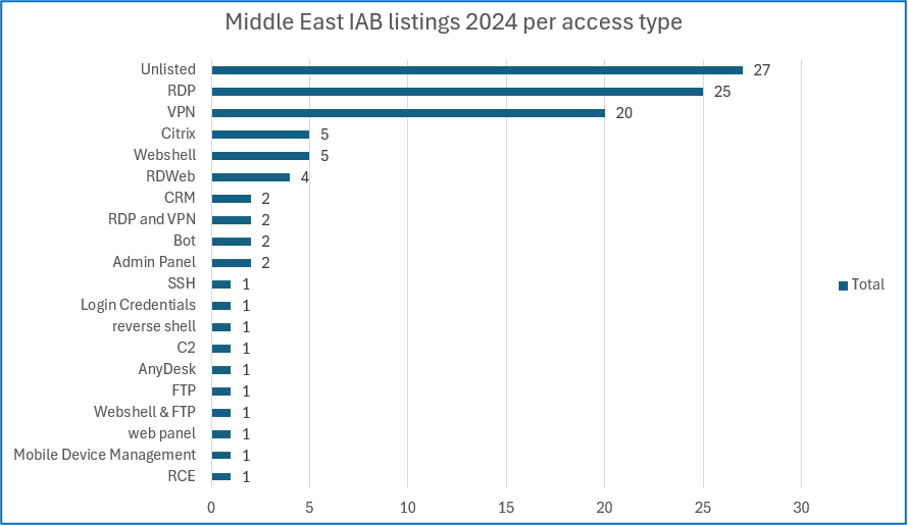
Most of the listings found by Cyjax which target the Middle East in 2024 offered RDP access (24.04%), followed by VPN access (19.23%). Of the listings in 2024, 27 did not specify the type of access being offered. Occasionally, IABs will offer a combination of access types in their listings.
Remote Desktop Protocol (RDP) is a protocol that was developed by Microsoft which allows users to access a graphical user interface (GUI) to a desktop over the internet. It operates on port 3389 and encrypts sessions using transport layer security (TLS). As such, RDP is employed by organisations to allow employees to remotely interact with their work laptop or sever from another location, often from a different office or from home. It allows users to remotely control a desktop as if it was their own. Connecting through RDP, an employee can control a powerful server from their comparatively weak personal laptop. IT helpdesks commonly use RDP to remotely connect and take control to employees’ machines when diagnosing and fixing computer problems.
This type of access can be used to cause significant damage, as it offers the attacker full control over the compromised host and any data hosted on it. They may use this data or applications such as email to conduct Man-in-the-Middle (MITM) attacks to gain access to additional hosts in the target environment. Advanced attackers may pivot from this entry point to other hosts within an organisation’s network if the machine is unpatched, other machines in the local network have weak or default passwords enabled, or principles of least privilege (POLP) are not adhered to.
It is important to clarify that on cybercriminal forums RDP appears to be used more generically as a catch-all term for any type of remote desktop access, rather than specifically Microsoft’s RDP. While this is not technically accurate, the premise of this is the same and allows users to simply access graphical interface to a networked desktop within a corporate network.
Virtual Private Network (VPN) is a mechanism for creating a secure connection between a computer and a network, or between two networks. This typically occurs over an insecure channel of communication, such as public internet. VPNs allow organisations to build a logical local network over a physical global network. Organisations use VPNs to securely connect their remote workforces and branch offices to the applications, data, tools and resources they need as if they were connected to a local network.
Whereas a compromised RDP provides remote access to a computer or device, a compromised VPN provides an attacker with access to a secure network. This likely contains an organisation’s internal systems, including shared files and directories. This can have a significant impact if POLP is not followed, and lower-level employees can access sensitive documents stored on the network. As such, any organisation operating a VPN needs to ensure appropriate firewalling and privilege assignment. It should also conduct logging to maintain visibility into who and what is connecting to its network, and what they are accessing.
Pricing
Several of the listings in 2024 did not state a price for the access, which is likely due to the price being negotiable over private messages with the IAB. There is a large discrepancy between the largest and lowest price listed by any one threat actor in 2024. The highest price listed was $150,000, while the lowest was $15. Price variation often comes down to the individual broker, the quality of the access, and the value of the company.
The higher priced listing offered RDP and VPN access to a large unnamed Israeli IT organisation’s cloud infrastructure. This listing has since been deleted from the forum. It is possible that this is the result of a successful sale, or due to the access vector no longer being viable.
Hacktivism
Cyjax tracks hacktivist activity and alleged Distributed Denial-of-Service (DDoS) attacks conducted by these groups as parts of various operations and campaigns. In 2024, 876 targeted DDoS attacks were claimed by hacktivist groups against Middle Eastern organisations. These types of groups often post claimed attacks with CheckHost links included as proof that the services have been taken offline. Check-Host.net is an online tool used for checking the availability of websites, servers, hosts, and IP addresses at a given point in time.
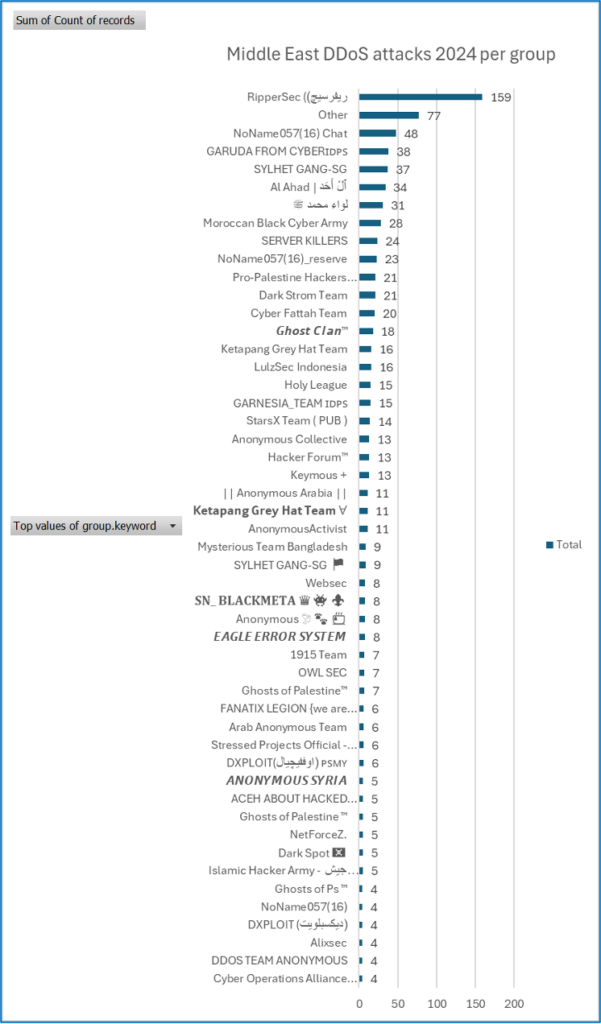
Over 50 different groups conducted targeted attacks against the Middle East, with most of these being conducted by RipperSec (18.15% of total attacks), followed by NoName057(16) (5.48%), and GARUDAFROMCYBERIDPS (4.34%).
RipperSec
RipperSec is an English-, Indonesian-, and Malaysian-speaking hacktivist group which is active on the encrypted messaging platform Telegram. It has roots in Malaysia but has since started to expand globally. The group likely formed in October 2021, with its current main Telegram channel created on 17 June 2023 and its backup channel created on 13 October 2021. RipperSec is a pro-Palestine group which mainly targets Israel and organisations that support it in the ongoing Israel-Palestine conflict.
The group has targeted media, government, and other sectors across numerous countries, with most of its DDoS attacks being aimed at Israel and India. More recent attacks have been targeted at those which the group views as supporting Israel. RipperSec uses the Medusa botnet to conduct its DDoS attacks and has also conducted a small number of website defacements against India-, UK-, and Vietnam-based organisations. It has also leaked data from a company in Singapore.
While RipperSec appears to conduct numerous DDoS attacks on a near-daily basis, attacks by these types of hacktivist groups often have a limited lifespan. Nevertheless, there is still a level of threat to the organisation being targeted, with short website outages being a common consequence of these attacks. This group targets both large and small organisations, with a focus on those that support Israel.
RipperSec likely possesses a moderate level of technical capability, having conducted defacement attacks and data exfiltration. This almost certainly indicates that the group can gain initial access into organisations. Additionally, it often posts on its channels about programming and various attack types; however, it has not yet displayed an ability or the sophistication to develop its own toolset.
Attacks per Country
Cyjax’s analysis shows that Israel was by far the most targeted country in hacktivist DDoS attacks in 2024, with 89.04% of attacks being conducted to target the country. This is followed by the UAE with 4% of attacks, Saudi Arabia with 2.63%, and Jordan with 2.17%.
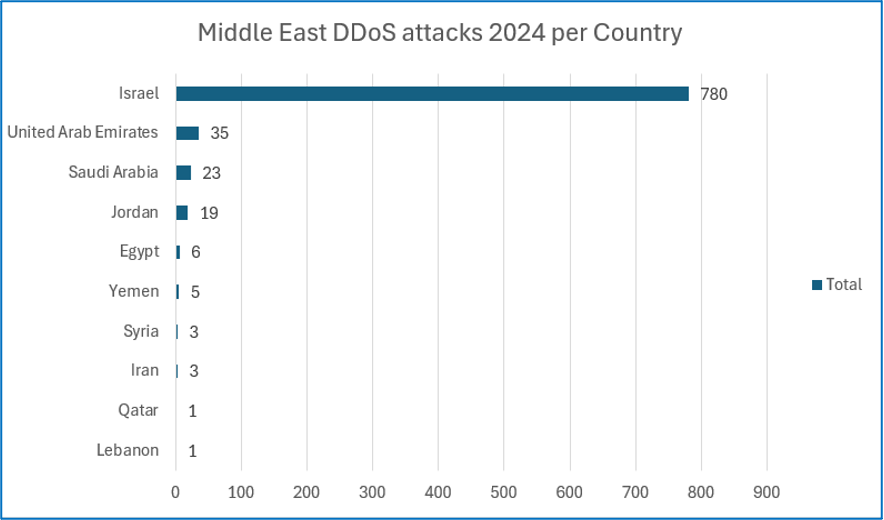
It is highly likely that this level of targeting aimed at Israel is due to the ongoing Israel-Palestine conflict. A large-scale invasion against Israel began on 7 October 2023, which was led by the Palestinian militant group Hamas. As such, many hacktivists took sides and started attacking the opposing country in solidarity with their chosen cause. Many hacktivists based globally have supported Palestine and conducted DDoS attacks against Israeli websites. Cyjax started a rolling report documenting cyber-attacks related to the war, along with other major developments which is available to clients.
Sectoral Targeting
Targeted organisations in the Middle East have been found in the education, government, sport, retail, automotive, healthcare, telecommunications, NGO, finance, IT, aviation, transportation, politics, maritime, and legal sectors, among others. In several cases, groups have attacked a certain website more than once. This could indicate that the site remains more vulnerable to DDoS attacks than some of the other targeted services.
These attacks can be opportunistic in terms of sectoral targeting, though they are firmly targeted in terms of countries. Many hacktivist groups are not very technically sophisticated and will conduct attacks against easier and more opportunistically available victims. The attacks can also often be specifically targeted to disrupt website access to certain services which are deemed highly valuable to the country.
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
