Introduction
The realm of hacktivism is rapidly expanding, its contours continually shifting and adapting to the geopolitical climate. Within this dynamic landscape, specific regions and industry sectors face heightened risks. Hacktivism, by its very essence, thrives in the public eye, as its actors strive to effect political or social change. Notably, Telegram has emerged as a favoured communication channel for hacktivist collectives facilitating internal dialogues among groups and fostering connections across broader coalitions. Externally, these groups leverage Telegram to disseminate their activities to the media and the general public. CYJAX diligently monitors the Telegram-based hacktivist ecosystem, dissecting their outputs and shedding light on developments during the first quarter of 2024
Statistical analysis
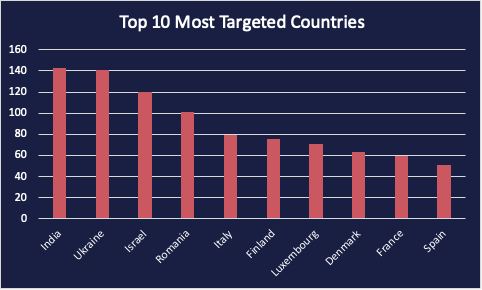
Countries that appeared most frequently in hacktivists’ DDoS claims in Q1 2024
Hacktivist groups using Telegram frequently engage in distributed denial-of-service (DDoS) attacks against organisations within specific industry sectors and countries where they aim to effect change. DDoS attacks involve overwhelming a resource by flooding it with a large volume of data packets, often through legitimate requests, causing the resource to crash or become unresponsive. These groups often share links to Check-Host reports a platform that displays the downtime experienced by a given URL as “proof” of a successful DDoS attack against the targeted organisation’s website. While Check-Host reports alone do not definitively prove a DDoS attack, they serve as compelling circumstantial evidence supporting the claim.
While not immediately evident from the targeted domains, obtaining sector-specific information about organizations can be challenging. However, Cyjax’s analysis reveals that at least 35% of the targeted domains belong to critical national infrastructure (CNI) organizations, and approximately 18% are associated with government entities. This likely reflects hacktivists’ intent to directly respond to government decisions related to social and geopolitical issues during the last quarter. Notably, attacking government organizations requires a higher level of technical sophistication. Interestingly, when compared to financially motivated actors (such as initial access brokers), government organizations appeared in only 4% of listings during Q1 2024. Analysing the top-level domains (TLDs) of the targeted domains featured in the Check-Host links allows analysts to determine the geographical location of the targeted organisations. Figure 1 illustrates the number of Check-Host reports posted by hacktivist Telegram channels, categorised by the countries to which the targeted websites belong.
#OpUkraine & #OpIsrael
Hacktivism, by its very nature, reacts swiftly to the ever-shifting geopolitical landscape. Consequently, it comes as no surprise that Ukraine and Israel, both countries facing crises, rank among the top three targeted nations in the last quarter. Organisations based in these countries have borne the brunt of frequent distributed denial-of-service (DDoS) attacks. The conflicts within these regions experienced significant shifts during Q1 2024, resulting in a surge of emergent hacktivist groups. These groups align themselves with various belligerents and conduct supportive cyber operations. In attack announcements, they often employ tagging schemes like “#Op[country name]” to signify their backing of specific operations. Occasionally, these tags include time periods or versions to distinguish them from previous campaigns.
India in the crosshairs
Despite ongoing conflicts in Europe and the Middle East, India became a primary target for Telegram-based hacktivist channels during Q1 2024, as evidenced by Check-Host reports. Several factors likely contribute to this trend. Firstly, India grapples with significant external and internal conflicts related to social and political issues. Additionally, the country is currently in an election cycle, with the ruling Bharatiya Janata Party (BJP) advocating Hindu nationalism, a stance met with opposition. The BJP’s appeal to India’s Hindu majority has intensified tensions between Hindu and Muslim communities. Hacktivist groups, both within India and externally, have responded to the perceived persecution of Muslims within the country, particularly in the disputed Kashmir region. As part of #OpIndia, groups like LulzSec Muslims, LulzSec Indonesia, GanoSec Team, and Garnesia Team conducted DDoS attacks and other cyber operations against government and Hindu-aligned organizations in protest. Beyond its internal conflicts, India’s foreign policy has sparked controversy. Historically, India stood in support of the Palestinian cause; however, the current government has shifted toward backing Israel in recent years. Additionally, Israel has actively favoured employing Indian nationals for both public and private-sector projects. As this alignment strengthens, numerous pro-Palestinian hacktivist groups have escalated their attacks against India in retaliation. CYJAX observed #OpIndia as one of the most significant decentralized hacktivist campaigns during the last quarter.
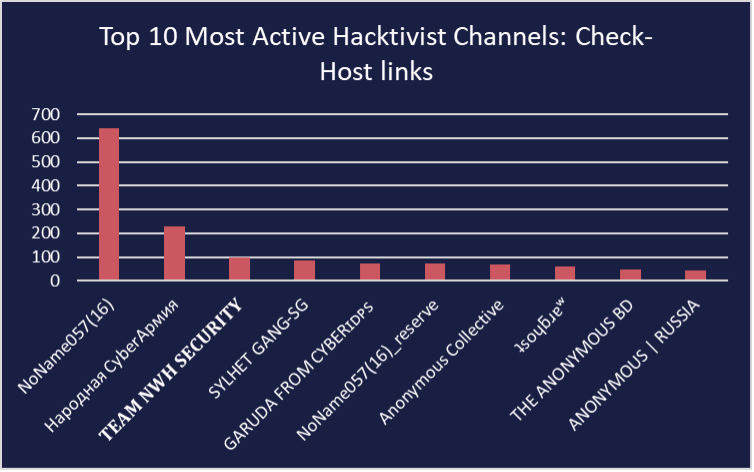
Most active hacktivist groups in Q1 by Check-Host links
NoName057(16)
During the last quarter, the Russian hacktivist group NoName057(16) stood out as the most active by a significant margin. Their prominence was gauged based on the number of links they shared to Check-Host reports. Throughout Q1 and into Q2, NoName057(16) consistently issued daily alerts via Telegram, announcing successful distributed denial-of-service (DDoS) attacks against numerous targets. Each post typically highlighted 5-15 specific targets, and the group often made multiple posts per day. Notably, attack notifications were often categorised by country, and occasionally, by the specific organisation. NoName057(16) demonstrated remarkable organisational prowess, unwavering effort, and unmatched consistency within the hacktivist landscape. Given these attributes, it comes as no surprise that they claimed the title of the most active group during the previous quarter.
NarodnayaCyberArmiya
The second most active group was the pro-Russia hacktivist group Народная CyberАрмия / Narodnaya CyberArmiya (National CyberArmy), also known as CyberArmyOfRussia_Reborn. Recent security research revealed that this group was among three hacktivist entities linked to Sandworm, a prominent state-sponsored Russian Advanced Persistent Threat (APT). Sandworm cleverly utilised Narodnaya CyberArmiya as a veil to conceal its operations, promoting Sandworm-orchestrated attacks under the guise of Narodnaya CyberArmiya. Among the three groups—XakNetTeam, SoIntSepek, and Narodnaya CyberArmiya—Narodnaya CyberArmiya maintained the closest operational ties with Sandworm. Additionally, a YouTube channel operated by Narodnaya CyberArmiya was discovered to have been created using infrastructure associated with Sandworm, further substantiating direct Sandworm involvement.
TEAM NWH Security
TEAM NWH Security, an Indian hacktivist group, maintains connections with several other pro-India groups, including TeamUCC, Team-Network-Nine, and BlackDragonSec. The tension between pro-Indian factions and hacktivist groups aligned with Palestine and the Muslim faith remains high. This tension arises from both geopolitical conflicts between India and Palestine and internal strife within India itself. Consequently, these groups engage in a perpetual cycle of attacking entities based in countries they perceive as opposing their causes. Their actions serve to demonstrate their relative strengths and advance their agendas.
Other groups highly active last quarter
- Sylhet Gang-SG: appears to be a pro-Palestine, anti-India, Bengali-speaking hacktivist group active since 2023. It heavily targeted perceived pro-Israeli organisations in Q1 2024.
- Garuda from Cyber: appears to be a pro-Palestine hacktivist group that first emerged in November 2023. It targeted Israeli and Indian organisations in Q1 2024.
- Anonymous Collective: appears to be a pro-Palestine hacktivist collective that started operations in October 2023. The group targeted Israeli and Indian organisations in Q1 2024 alongside its affiliates.
- The Anonymous BD: appears to be an anti-India and anti-Israel hacktivist group that first emerged in February 2023. The group targeted several countries in Q1 2024, including Sweden, Switzerland, India, and Israel.
- Anonymous Russia: appears to be a pro-Russia hacktivist group that operates several Telegram channels. The group conducted several DDoS attacks and website defacements in Q1, including against organisations in France, Belgium, Armenia, and Italy. However, activity has appeared to slow down from February 2024.
Hacktivism and conflict
CYJAX has noted that partisan hacktivist groups associated with significant conflicts are collaborating more frequently in coalitions, commonly referred to as “collectives”, during 2024. They aim to enhance the impact and efficiency of their attacks by pooling resources and technical capabilities. The belief is that this collective effort will lead to more potent attacks against larger entities.
Hacktivism surrounding the Russia-Ukraine conflict
Since Russia invaded Ukraine in February 2022, partisan hacktivism has played a significant role in the ongoing conflict. During Q1 2024, this trend continued. UserSec, a group that emerged in February 2023, has persistently targeted organizations in Ukraine and its allied countries. UserSec maintains connections with other pro-Russia hacktivist entities, including AnonymousRussia, with whom it collaborates on joint attacks. In the same quarter, UserSec expanded its cooperation further by conducting joint operations alongside select members of the NoName057(16), National CyberArmy, and 22C hacktivist groups. The extent of UserSec’s awareness regarding National CyberArmy’s operational ties to Sandworm remains uncertain. Nevertheless, this situation raises intriguing questions about state-sponsored influence over hacktivism, prompting us to consider the Russian government’s level of involvement in these pro-Russia groups often perceived as tolerated but not directly controlled by the Kremlin
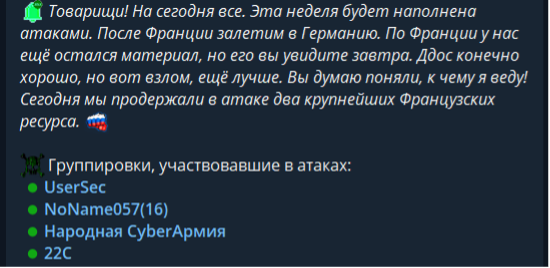
Translation: “Comrades! That’s all for today. This week will be filled with attacks. After France we will fly to Germany. We still have some material left on France, but you will see it tomorrow. DDoS is good, of course, but hacking is even better. I think you understand where I’m going with this! Today we kept two of the largest French resources under attack.”
Hacktivism surrounding the Israel-Palestine conflict
In the context of the Israel-Palestine conflict, partisan hacktivism has emerged as a significant force in cyberspace. During Q1 2024, numerous groups, often operating from locations beyond the conflict zone, shifted their focus towards attacking Israel and organisations perceived to be aligned with Israel. These attacks were driven by developments in the ongoing conflict. A common motivation cited by these hacktivist groups is religion, particularly among those adhering to the Islamic faith, who tend to align with Palestine.
Notably, the intensity of attacks against Israel increased during this period. However, it’s important to recognize that other countries also became targets. For instance, the United States faced denunciation and targeting by several hacktivist groups. This response was triggered by the United Nations’ decision to veto Palestine’s request for full United Nations membership in April of the previous quarter.
The Cyber Operations Alliance (sometimes stylized as “C.O.A. Agency”) stands out as a prominent name in the hacktivist landscape related to the Israel-Palestine conflict. This alliance was established by a member of the pro-Palestine Garnesia Team hacktivist group and comprises 11 hacktivist groups: Garnesia Team, Toxcar Cyber Team, Garuda from Cyber, LulzSec Indonesia, Garuda Cyber Operations, From Lammer to Mastah, Ketapang Gray Hat, StarsX Cyber Team, Islam Cyber Team, Moroccan Black Cyber Army, and Hacktivist Jatim. These groups within the alliance share similar views and actively engage in attacks that support Palestine. Their primary targets include India, the United States, and Israel.
Notably, the Cyber Operations Alliance operates in a decentralised manner, lacking centralised leadership. Each group continues to pursue its own agenda while collaborating within the broader framework of the alliance.It is worth noting that the #OpIsrael and #OpIndia tags pre-date the current stage of the conflict, having been commonly used for several years. CYJAX conducted an analysis of these campaigns and the participating hacktivist groups in May 2023.
Additional Insights from Q1 2024
The Five Families
The Five Families, a hacktivist coalition, originally comprised five groups: GhostSec, ThreatSec, Stormous, Blackforums, and SiegedSec. However, SiegedSec was removed from the coalition in late December 2023 after being publicly denounced via the coalition’s Telegram channel. As of the current time, no new group has replaced SiegedSec, leaving the coalition with only four known members.
During Q1 2024, The Five Families primarily focused on promoting their members’ ransomware activities. Additionally, the coalition utilised their channel to advertise initial access brokerage services, including listings for Fortinet VPN access to corporate networks. Notably, The Five Families has expanded beyond Telegram, using cybercriminal forums to market stolen data for sale.
GhostSec continues ransomware expansion
GhostSec, a pro-Palestine hacktivist group originally founded in 2015, has primarily focused on launching Distributed Denial of Service (DDoS) attacks and leaking data via Telegram. In October 2023, GhostSec made headlines by introducing a new ransomware-as-a-service (RaaS) called GhostLocker. This RaaS continued to evolve during Q1 2024, culminating in the release of version 2.0 on January 19.
During the same quarter, GhostLocker underwent another update through a collaborative effort with Stormous, a fellow RaaS group and member of The Five Families. The result was STMX_GhostLocker, the third iteration of GhostLocker. Notably, both groups contributed to its development, leading to two significant updates in the ransomware within the last quarter alone. Despite this shift towards ransomware operations, GhostSec continues to operate within the hacktivist sphere, maintaining a similar approach to its activities prior to GhostLocker’s emergence.
DDoSaaS providers in the hacktivist sphere
SkyNet / Godzilla Botnet
Skynet, also known as the Godzilla Botnet, operates as a DDoS-as-a-service (DDoSaaS) provider within the hacktivist domain. In DDoSaaS, a botnet’s computational power is rented out to other cybercriminals for executing distributed denial-of-service attacks. The SkyNet operators offer DDoS capabilities to multiple targets daily, charging a flat rate. Their claim of having “up to 1TB power” suggests significant potency if accurate.
The SkyNet botnet has reportedly been involved in large-scale attacks, targeting organisations such as Facebook, Steam, and even the official Cloudflare site. The operators have even asserted possession of a functional exploit capable of taking down any Cloudflare-protected site. Notably, the pro-Russia hacktivist group AnonymousSudan played a key role in promoting this service. In Q1 2024, AnonymousSudan partnered with SkyNet to claim attacks against major companies, including OpenAI, Fox News, and Telegram. Despite this collaboration, SkyNet seems to be transitioning toward independent operations while continuing to offer its services at a fixed price.
InfraShutdown
InfraShutdown, another DDoS-as-a-service (DDoSaaS) provider, operates within the hacktivist sphere. The service came to light in February 2024 and was swiftly endorsed by AnonymousSudan. The group even renamed its Telegram channel to “Anonymous Sudan – InfraShutdown,” a name that remains unchanged as of now. Although AnonymousSudan asserts that the service is separate from their group, CYJAX speculates that either AnonymousSudan or one of its members is behind the operation. The sudden promotion of InfraShutdown following its initial emergence and the apparent close relationship between the group and the service contribute to this suspicion, especially when compared to their association with SkyNet.
InfraShutdown operates on a pricing model based on timeframes, offering different tiers of attacks. The operators claim that the service can execute robust layer 3, layer 4, and layer 7 attacks, while also evading DDoS protection measures. In Q1 2024, AnonymousSudan attributed several attacks to the InfraShutdown service, including an assault on Bahrain’s mobile operator Zain and Telecom Armenia.Sandworm APT posing as multiple hacktivist groups
In April 2024, researchers established a connection between the Russian state-sponsored APT Sandworm and three Telegram hacktivist channels. Although these channels operated independently and in parallel, it was discovered that Sandworm was using them as a cover for its operations. Under the guise of various hacktivist groups, Sandworm promoted orchestrated activities. The groups associated with Sandworm operations included XakNetTeam, Narodnaya CyberArmiya, and SolntSepek. These groups amplified Sandworm’s activities and disseminated pro-Russia content.
This discovery represents a significant shift in the hacktivism landscape, blurring the lines between hacktivists and state-sponsored APTs. The Kremlin appears to have weaponised these hacktivist groups, leveraging their existing following among civilian populations. This strategy can be effectively employed during times of warfare. It marks a novel form of cyber warfare that has now been demonstrated to work within the context of geopolitical conflicts. Notably, CYJAX’s prediction in December 2023 that hacktivism would continue to play a crucial role in Russia’s cyberwarfare strategy seems to hold true.
While hacktivism’s ties to state-sponsored entities are not entirely new, this situation represents a notable development. It is the first time a known state-sponsored APT has been positively identified as using Telegram-based hacktivists as a veil for its operations.
Conclusions
The hacktivist landscape remains in constant flux, adapting to the ever-changing geopolitical climate. Various approaches characterise hacktivism, ranging from anarchical to methodical or purely reactionary. In the last quarter, we witnessed a notable trend: formerly disparate hacktivist groups are now organising more effectively. Smaller groups are forming formal alliances, aiming to enhance the volume and efficiency of their attacks. Additionally, intriguing developments involve state-sponsored interference within this space.
Hacktivism, once the domain of civilian entities seeking political or social change, now faces vulnerabilities. Q1 2024 demonstrates that it can be manipulated, with belligerents weaponising this form of cyber activism.
