Following the emergence of data-leak sites (DLSs) for Babuk Bjorka, GD LockerSec, and Morpheus in January 2025, a new extortion group called Kraken and its DLS has been observed in February.
Read on to find out what Cyjax knows so far about this new threat group.
Key takeaways
- A Tor-hosted DLS emerged for Kraken in February 2025.
- At the time of writing, the group has claimed attacks against five organisations. Four of these victims are based in the United States and one in Poland.
- Kraken has publicly released data for three of the five victims. The data from one other victim is being prepared for publishing. At the time of writing, the data for the final victim is up for auction. No victims have confirmed whether the attacks took place. · One purported victim is Cisco, which has stated that Kraken is sharing data from a breach which allegedly took place in 2022 and was conducted by HelloGookie.
- Kraken’s DLS names the previously inactive HelloKitty ransomware group in the website title. This has created speculation that Kraken may be a faction or offshoot of the group. HelloKitty rebranded to HelloGookie Ransom in April 2024.
- Kraken has shared content which may suggest that it is a rebrand of the now defunct Yanluowang ransomware group.
Context
Extortion groups commonly use DLS to further extort victims, typically proceeding in multiple stages. The first threat is that the victim’s name and news of a successful attack against it will be published on the extortion group’s website. Should this fail to motivate a victim to pay a ransom, the group’s next step is typically to provide proof of the successful theft of its data. This proof may include screenshots of internal file trees, samples of employee or customer PII, or other sensitive documents. The group may add a countdown at this stage, noting that should the victim fail to pay by the conclusion, it will make all stolen data available to DLS visitors, either for free or at cost.
Victimology
As of 11 February 2025, Kraken has claimed attacks against five victims. Four of these entities are based in the United States and one is located in Poland. Two of the victims, specifically Cisco and CD Projekt, were named on ransomware group HelloGookie’s DLSn April 2024. However, it is unclear whether these are comprised of separate or related attacks. At the time of writing, none of the alleged victims have confirmed that Kraken successfully gained access to their systems. The relevant posts on the Kraken DLS list the following:
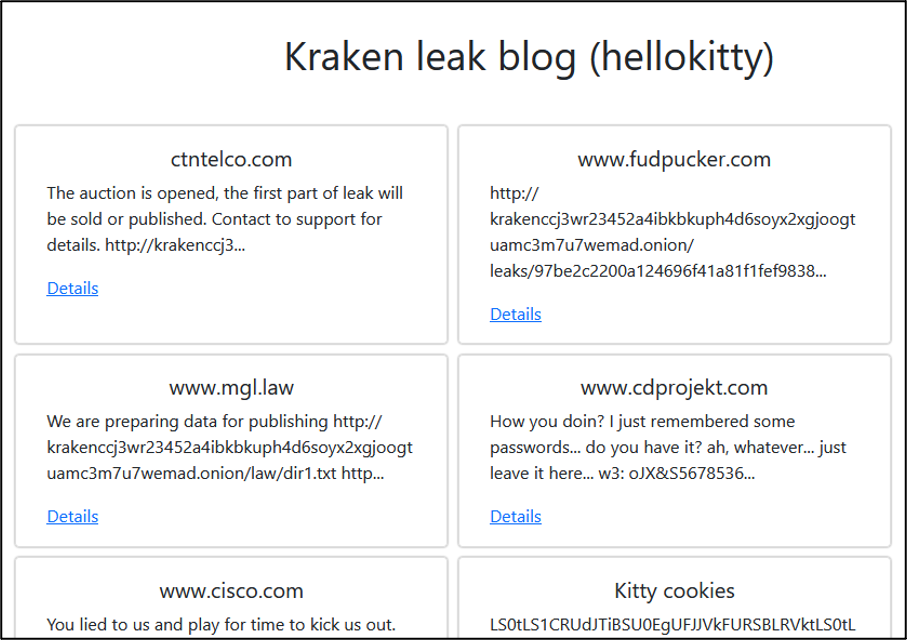
- US based technology company Cisco (www.cisco.com). The group stated, “you lied to us and play for time to kick us out”. Kraken has shared what appears to be logins and hashed passwords, most likely in an attempt to prove the group had access to Cisco’s systems. On 10 February 2025, Cisco stated that Kraken was re-sharing data which was breached in 2022.
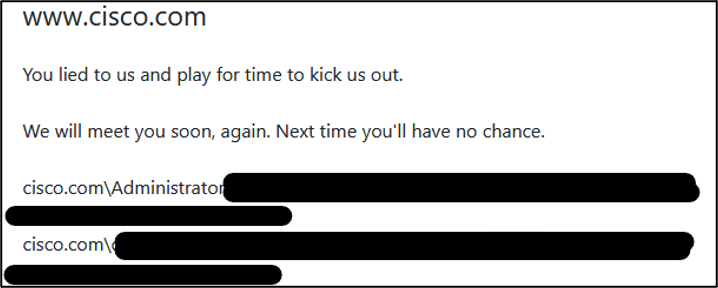
- Poland-based technology company CD Projekt (www.cdprojekt.com). The group has shared what appears to be hashed passwords.
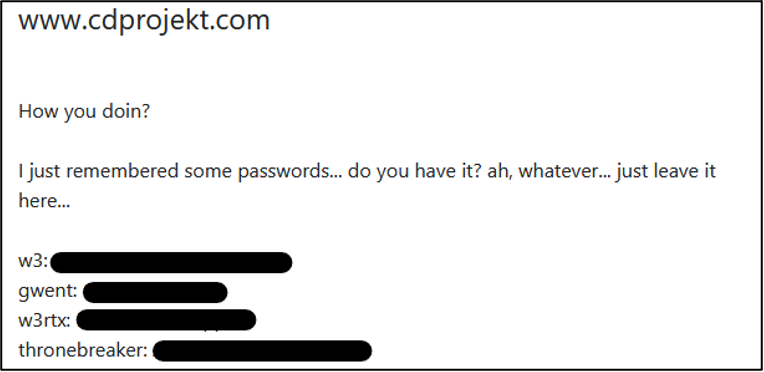
- US-based law firm Martin Golden Lyons (www.mgl.law). The group has stated it is currently preparing to publish the data. However, it has shared links which show the directories of the organisation.
- US-based bar and grill Fudpuckers (www.fudpucker.com). The group has leaked the restaurant’s files and visitors can download them for free.

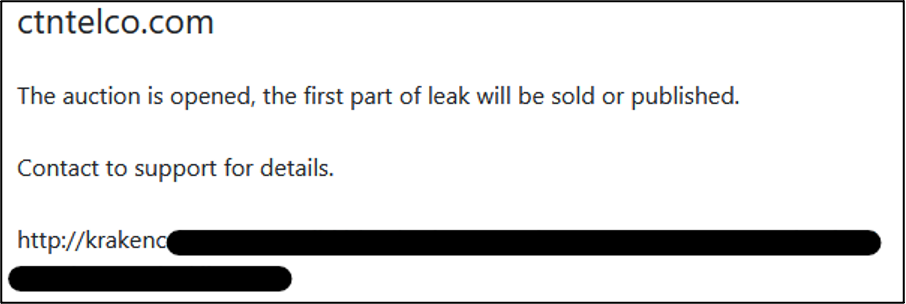
- US-based telecommunication company Converged Telephony Networks (ctntelco.com). The data is currently up for auction, with the group implying that there will be more than one part to this dataset.
Locations
It is unclear when the DLS was established, though posts were uploaded to it by 9 February 2025 at the latest. The TOR-hosted Kraken DLS consists of only a landing page, which hosts a list of organisations the group claims to have targeted. The posts often ask for potential buyers to get in contact; however, no details are visible on the site. As such, it is likely that the group directly makes initial contact with victims following an attack. Clicking on each victim post takes the visitor to a page from which allegedly stolen data can be downloaded. There is a lack of rules or manifesto on the group’s DLS, meaning few insights can be gleaned surrounding its motivations.
The DLS also has a counter at the bottom of the page which shows the current page views. As of 11 February 2025, the count is at 223,020.
Associations
HelloGookie (HelloKitty)
Kraken has shared a post titled “Kitty Cookies” which contains a page of private keys. This presumably allows previous victims to gain access to data. However, it should be noted that the purpose of these keys is not stated. This was also observed in April 2024 on the HelloGookie DLS.

HelloGookie, which was previously known as HelloKitty before its rebrand in 2024, is a Ukraine-based ransomware group that likely formed in 2020. It has targeted both large and small enterprises, with its victim including the Poland-based games developer CD Projekt. Geographies targeted include the United States, Australia, and Italy.

The group encrypts victims’ files and directories, and exfiltrates stolen data. It maintains a data-leak site (DLS) where stolen data is made available to visitors for free. HelloGookie may also operate as a Ransomware-as-a-Service (RaaS) operation, though this has not been confirmed.
The HelloGookie ransomware is frequently delivered as a second-stage payload after previous malware attacks. It operates in a notably non-stealthy way while it encrypts the victim’s system. The HelloGookie DLS is down as of February 2025. The group made its last post on 20 April 2024.
Yanluowang
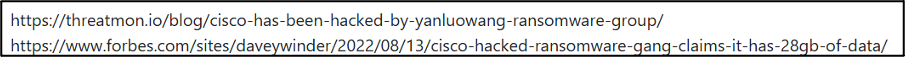
On the Cisco data-leak page of the Kraken DLS, the group has attached links to two articles which state that Cisco was “hacked by the Yanluowang ransomware group”. It is possible that the data allegedly stolen by Kraken differs to that stolen by Yanluowang. Cyjax is unable to verify whether the two datasets are identical because the Yanluowang DLS has been shut down.
Yanluowang, which is also known as Dryxiphia, is a ransomware group that was first observed in October 2021. On 2 November 2022, Cyjax recorded that the group’s DLS was defaced and a significant amount of data from Yanluowang was leaked online. Since the leak, Yanluowang shut down all its operations. Included in this leak was that Yanluowang was Russian-speaking rather than Chinese-speaking. This could mean that if the group was rebranded as HelloKitty, HelloGookie, and now Kraken, then it is of Russian origin.
Threat Assessment
It is possible that the groups mentioned within this blog are distinct, with Kraken adopting an existing name to enhance its credibility. Another possibility is that Kraken consists of former members from one or both of HelloGookie or Yanluowang. Kraken may also be a direct successor to these groups and uses the same infrastructure and personnel. The similarity between the HelloGookie and Kraken DLS further supports this theory.
Kraken has so far claimed attacks against five organisations and has shared download links for data allegedly stolen from three of them. However, two of these organisations were purportedly breached by the HelloGookie ransomware group. This could mean that the data is not new, and Kraken members did not gather it. At the time of writing, no victims have confirmed that Kraken successfully gained access to their systems.
Cyjax has not identified any concrete information surrounding any tactics, techniques, or procedures (TTPs) the group may use, and subsequently cannot assess the extent to which Kraken is technically capable.
To access our full intelligence repository containing detailed profiles like this one, covering extortion groups, advanced persistence threat groups (APTs), data brokers, hacktivists, initial access brokers, and more, click here to take a test drive of Cymon.
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
