Ransomware is one of the most prominent cybersecurity threats today, often spreading via phishing emails, malicious links, infected attachments, or exploiting software vulnerabilities. It is a type of malware designed to block access to files, data, or entire systems until a ransom is paid, usually in cryptocurrency. Beyond the financial impact, ransomware causes operational disruption and long-term reputational damage.
The frequency and scale of ransomware attacks have surged in recent years. In 2020, attacks rose by 435%, with a fourfold increase in cryptocurrency payments. This increase is driven by factors like remote work, more sophisticated techniques (e.g. stealer logs), and high-profile payouts encouraging copycat attacks.
Advancements in AI are also empowering attackers by automating phishing, malware obfuscation, and vulnerability exploitation, increasing attack scale, complexity, and precision. Machine learning models can even analyse victim behavior to optimise ransom demands, while AI-powered tools bypass traditional security systems, amplifying the global ransomware threat. Examples include malware variants like Emotet that use AI to modify their code in real time, evading signature-based detection tools.
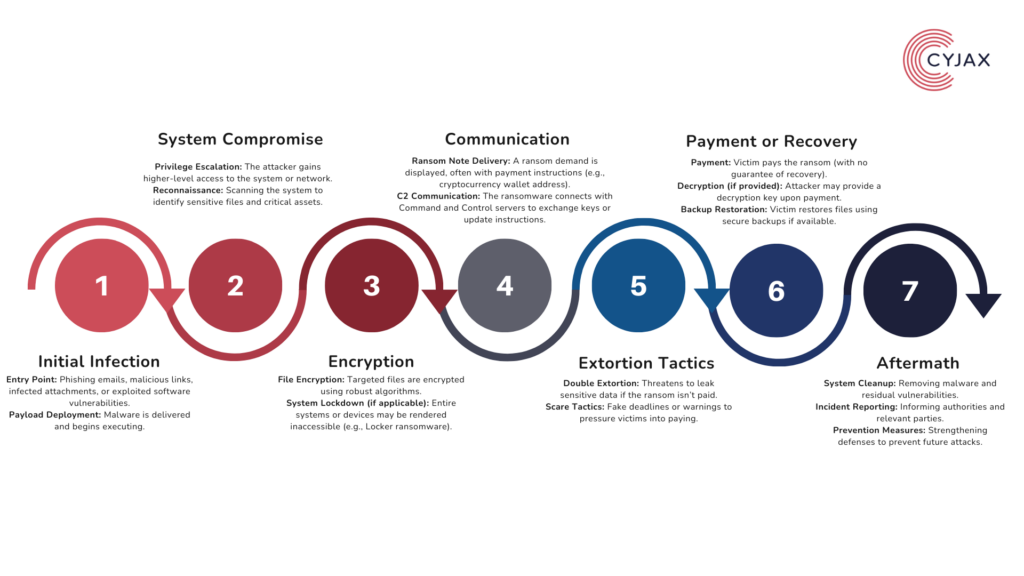
How does ransomware work?
While the goal of ransomware remains the same, attackers are employing increasingly sophisticated strategies to maximise payouts:
- Crypto Ransomware: The most common type encrypts files, making them inaccessible until a cryptocurrency payment is made. Cryptocurrency’s decentralised and untraceable nature makes it a very attractive payment method. One of the largest attacks in history saw REvil demanding $70m in bitcoin after infecting Kaseya IT systems.
- Locker Ransomware: Locks entire systems or devices. A notable example is WannaCry, which exploited a Microsoft Windows vulnerability (EternalBlue) to infect over 200,000 systems across 150+ countries.
- Ransomware-as-a-Service (RaaS): Criminals outsource attacks by selling ransomware kits via subscriptions, one-time fees, or profit-sharing. Examples include LockBit (responsible for 25% of ransomware attacks in 2023–2024), DarkSide (Colonial Pipeline DarkSide attack, $4.4M ransom), and ContFR.
- Doxware: Encrypts files and threatens to publicly release sensitive information unless payment is made, also known as double extortion. The Colonial Pipeline attack is one example where both RaaS and Doxware strategies were used.
- Scareware: Tricks users into downloading software under false pretenses, such as fixing a fake issue. Some variants lock systems and demand payment for restoration. Studies estimate one million people fall victim to scareware daily.
Preventing and identifying threats
Ransomware attackers often target industries like banking, healthcare, government, and education due to the societal impact of their disruption. However, no organisation is immune. Small businesses are vulnerable due to limited resources, making them easier targets with less media and law enforcement attention. And while enterprise and multinational organisations might have greater budgets and in-house expertise, they remain a target regardless of industry.
Governments combat ransomware by securing systems and aiding businesses. Measures include zero-trust frameworks, strict cybersecurity standards, incident response teams, and penetration testing. To prevent attacks, organisations must adopt their own comprehensive strategies as well, including:
- Regularly backing up data on secure servers.
- Training employees to recognise phishing scams and suspicious links.
- Using robust endpoint protection solutions.
As cyberattacks evolve, staying ahead of emerging threats is challenging. However, advancements in prevention technology and human expertise are helping to counter ransomware’s growing sophistication.
The Role of Threat Intelligence
Threat intelligence is essential for proactively defending against ransomware by providing actionable insights into emerging threats and vulnerabilities. Instead of merely reacting to attacks, it enables organisations to anticipate and mitigate risks through:
- Early Threat Detection: Analysing data from sources like the dark web and malware samples to identify suspicious activity, enabling early intervention.
- Contextualised Insights: Linking raw data to broader trends and industry-specific risks, allowing the prioritisation of defenses based on relevance.
- Faster Incident Response: Intelligence about attackers’ tools, tactics, and vulnerabilities accelerates response times, minimising damage.
- Improved Defense Strategies: Identifying vulnerabilities and attack trends helps strengthen systems and prioritise patching.
- Informed Decision-Making: Threat intelligence guides resource allocation and long-term cybersecurity planning.
Ransomware attackers often rely on speed and surprise to overwhelm their targets. Threat intelligence flips the script, keeping you a step ahead. It enables the detection and neutralisation of threats before they cause harm, minimising disruption and financial loss.
Investing in robust threat intelligence capabilities ensures that cybersecurity teams are not just reacting to threats but actively working to prevent them. Take control of your cybersecurity strategy today by learning more about threat intelligence here.
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
