Defenders often discuss security vulnerabilities on GitHub, Stack overflow, X (formerly Twitter), and other platforms to share knowledge of these threats and ensure users know when patches are available. Cybercriminals have a similar process, choosing to share vulnerability news, exploit code, and engage in technical discussions on cybercriminal forums. However, in contrast to defenders, these threat actors share this knowledge for the purpose finding unpatched systems and exploiting them. Additionally, initial access to systems is often obtained through the exploitation of vulnerabilities. This makes these discussions vital to other cybercriminals such as initial access brokers (IABs), who gain access to various organisations and then sell this access to other cybercriminals for profit.
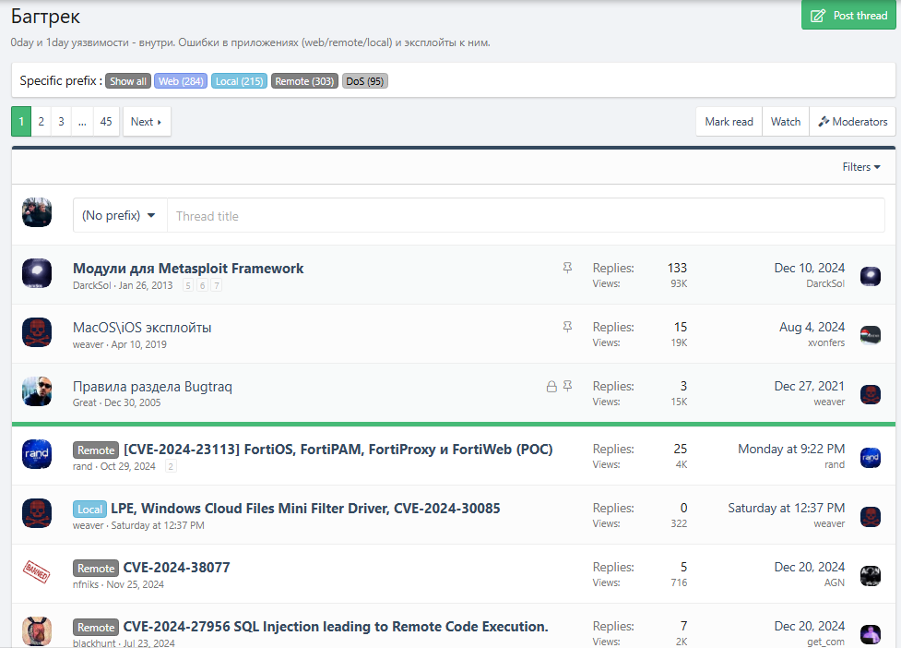
Whilst users typically cannot patch everything all at once, knowing which vulnerabilities are being commonly discussed and potentially abused can give key insights for defenders when deciding which CVEs patches to apply first. Cyjax monitors various sections of prominent Russian- and English-language cybercriminal forums, particularly the dedicated ‘bugtraq’ and ‘trade’ sections, where threat actors often discuss vulnerabilities, trade information on flaws, and buy or sell exploit code. Read on to learn how and why cybercriminal forum users discuss vulnerabilities.
What are CVEs?
CVE stands for Common Vulnerabilities and Exposures, and is used as an identifier to help track, identify, and define publicly disclosed security flaws in software. CVE numbers for vulnerabilities are assigned by a CVE Numbering Authority (CNA). Around 100 organisations are registered as CNAs, including security and research organisations, as well as IT vendors such as Microsoft, IDM, Red Hat, and MITRE.
Once a CVE is assigned, vulnerabilities are often disclosed by the organisation which they affect. Occasionally, researchers and organisations will also disclose a vulnerability that does not yet have an assigned CVE number, likely to inform the public that the flaw exists or has been patched despite not having an identifier.
Types of vulnerability discussions on cybercriminal forums
Sharing news of the vulnerability
Threat actors often share news of the vulnerability disclosure, though oftentimes this is not accompanied by any other information such as exploit code or a tutorial on how to run it. Sharing articles is a simple act, but news is often a popular thing to post on these forums, allowing attackers to keep up to date with the most recent activity in the cyber threat landscape. It gives attackers insights and the opportunity to see and read about vulnerabilities which others seem to find interesting, as users and moderators are unlikely to share insignificant flaws. Users also often translate English-language articles into Russian, making these articles easier for non-English speakers to understand.
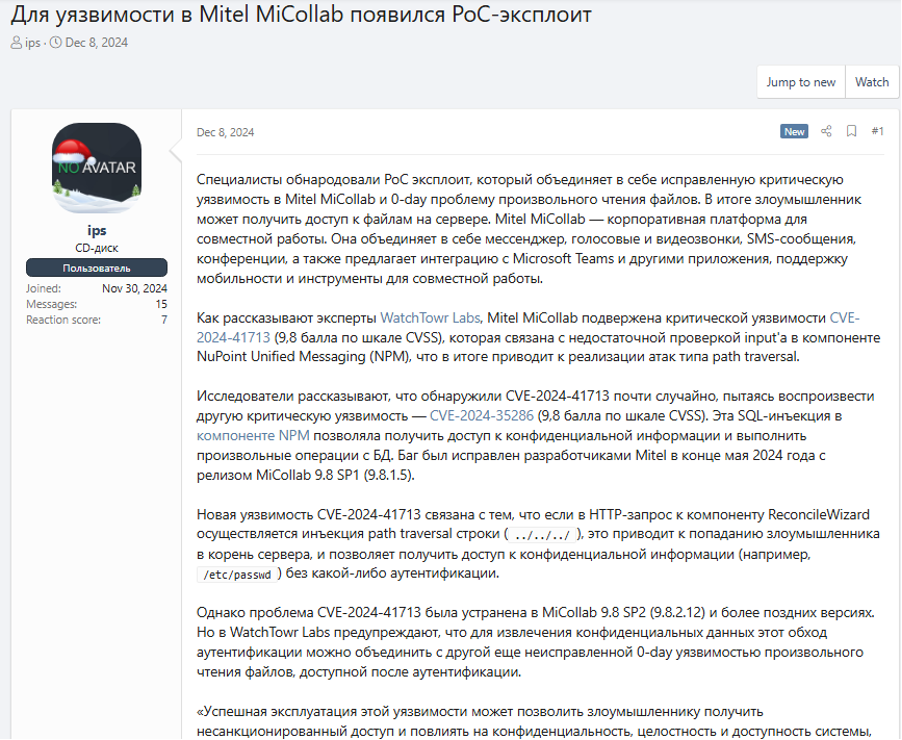
Technical discussion/analysis of the vulnerability and advice
Some of the more technically inclined users on these forums are known to share their own analysis and opinions about the vulnerabilities. These discussions can include details about the vulnerability itself and ways to exploit it. Oftentimes, the posts will have the most comments from other users that are giving their own opinions and technical expertise regarding the flaws, including sharing suggestions to improve any shared code.
These types of discussions and analysis can allow threat actors to contemplate other methods of exploitation which they may not have previously considered or attempted. It also provides the opportunity to receive potential suggestions to fix complex or non-working code.
These types of discussions often closely resemble discussions on legitimate help and support forums, where users often ask for help with patches, updates, or issues they are having with the product. On these forums, threat actors also ask for help in the same way, except the topics often include exploitation of the vulnerability and trouble with working the exploit code.
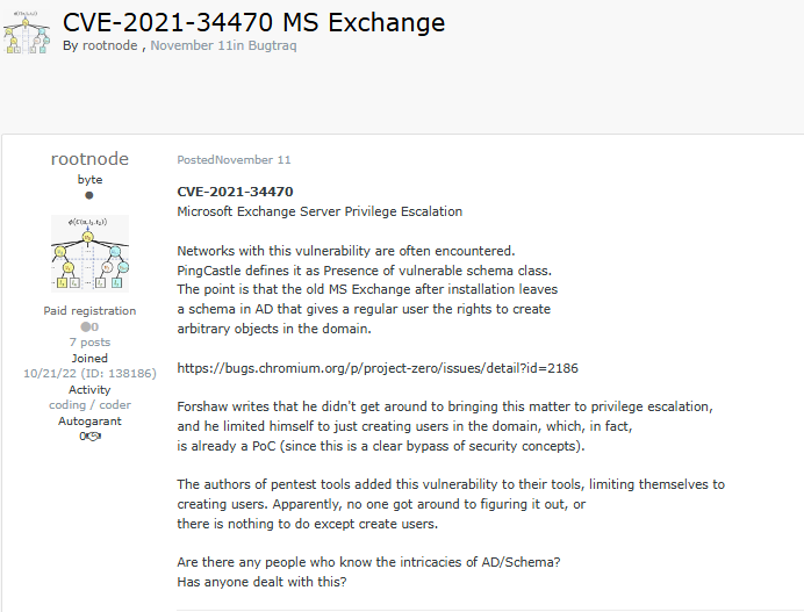
Threat actors sometimes ask users for help with exploiting vulnerabilities. Some users simply ask for general advice around exploitation whilst others ask for help with writing specific exploits or question why exploits are not working. There are also users who offer to pay for private exploits to be created for them by other users, often offering thousands of dollars for the work. Both of the above options can allow less sophisticated users to learn or buy from technically sophisticated threat actors and conduct exploits they would not have been able to do on their own.
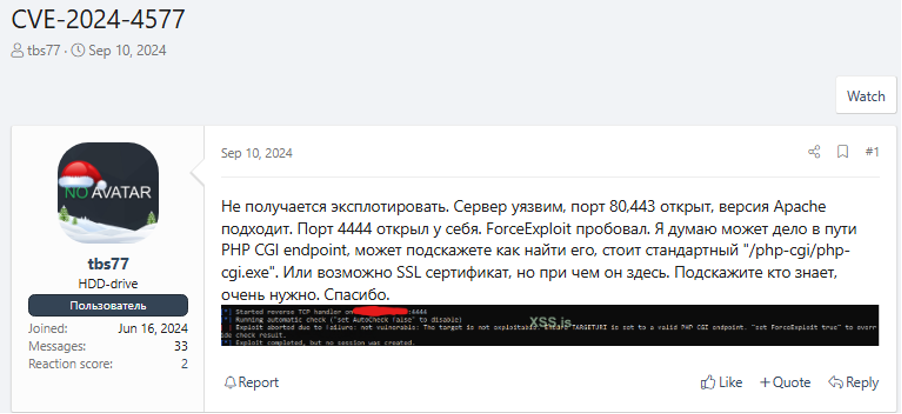
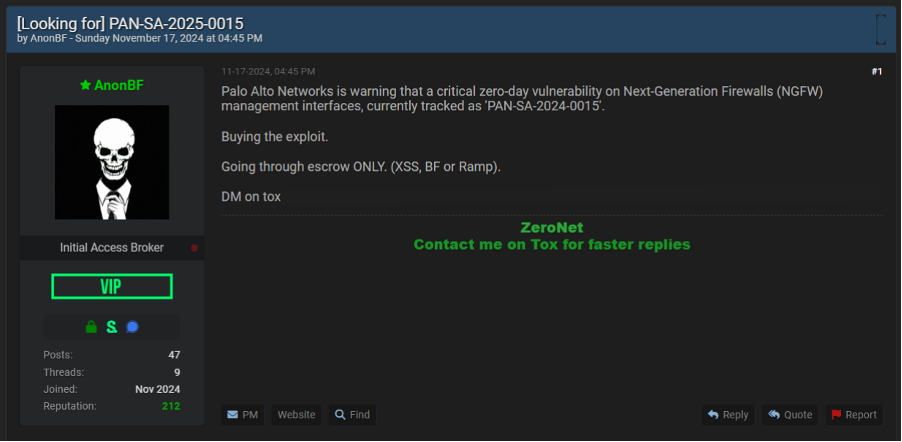
There are some users on the forums that do not have any issues with sharing knowledge and providing help or advice for free. These users will often answer technical questions that others have, sharing known public exploits and more.
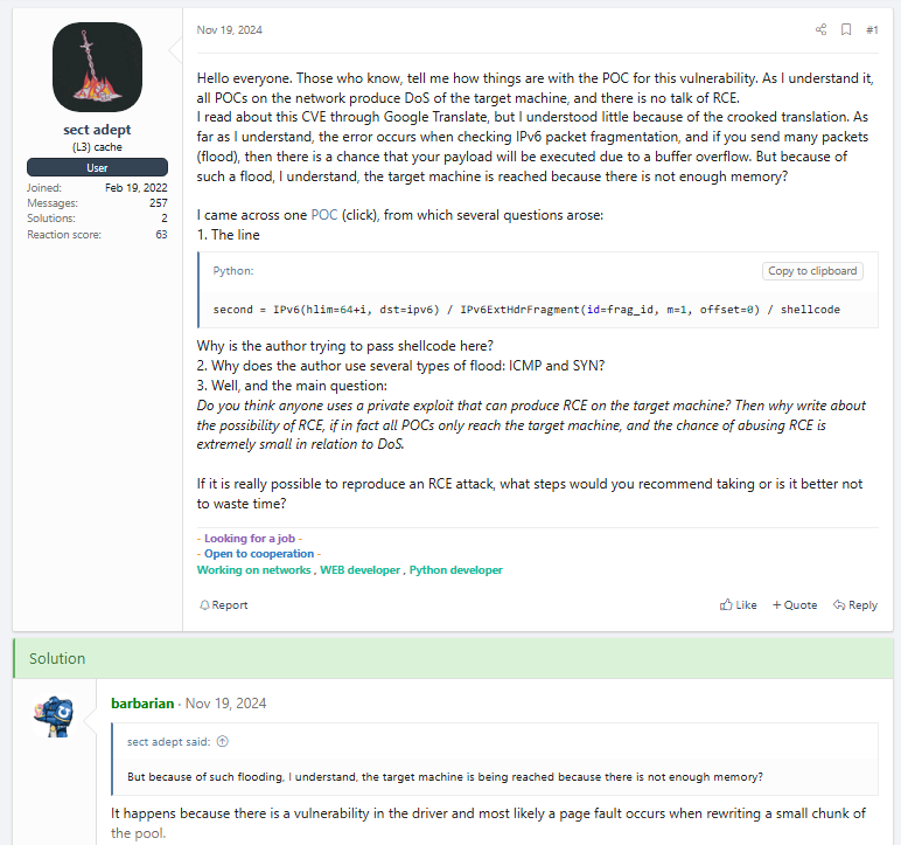
Exploit/PoC/GitHub repository shared for the vulnerability
Threat actors will regularly upload public Proof-of-Concept (PoC) code, exploits, and GitHub repositories to these forums. These will often also include tutorials on how to conduct the attacks or find vulnerable instances to target. While these PoCs, exploits, and GitHub links are usually originally posted by legitimate security researchers, they can be adapted and used by malicious threat actors in attacks against a vulnerable target.
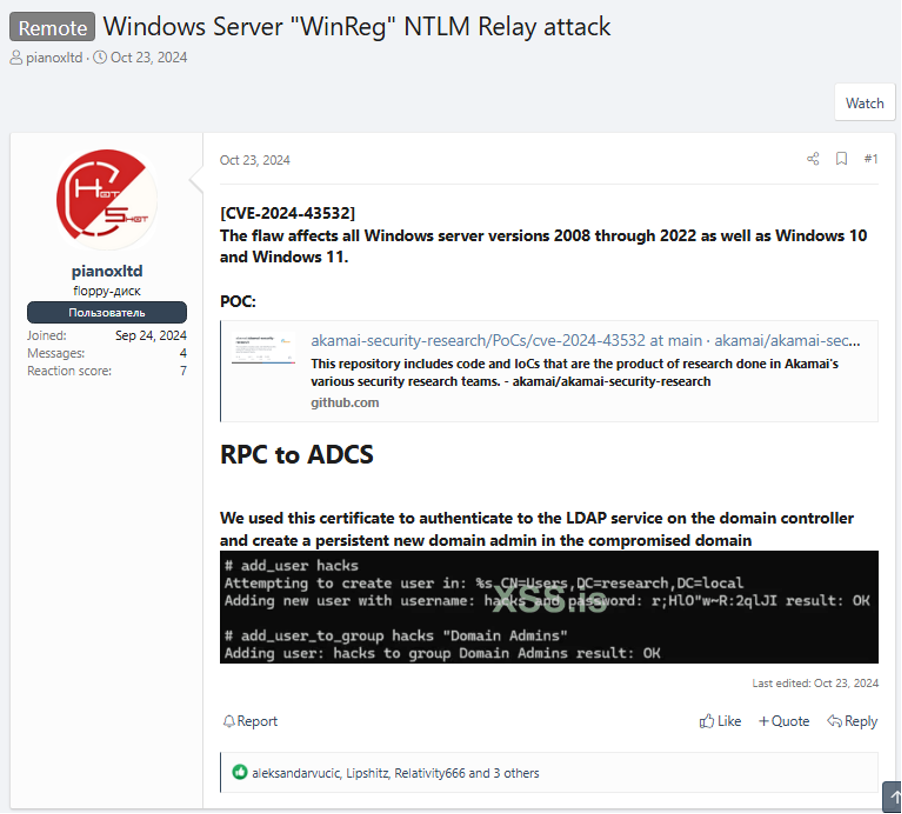
Exploit or vulnerable target advertised for sale and other trade/sale discussions
Threat actors do not always share information for free on these forums. Some users prefer to make a profit from their knowledge and technical capabilities. These users often advertise private exploits for specific vulnerabilities which are for sale, asking for a certain amount of money which is set by them and requesting to be contacted via private messaging. A lot of the time, sales on the forum are conducted through the forum’s escrow service. This service usually entails the use of a neutral third-party that makes sure the transaction payment is made to the seller on completion of the sale. This protects both the buyer and the seller, as the buyer can check that they are receiving the correct goods, and the seller knows that they will be paid if the sale terms are met. This neutral third-party will often offer arbitration services if there is a dispute between the buyer and seller.
In some cases, threat actors have offered to sell intelligence regarding targets that are vulnerable to specific vulnerabilities for a set price, or a percentage of the profits derived from attacks against the vulnerable organisations. In other cases, this type of intelligence is also offered free of charge.
Giving thanks
Responses to a post about a vulnerability, whether it is an exploit or just general information, will often include users thanking the original poster for the share. Whilst this does not aid threat actors in any way, it shows that the information shared by the original poster has been deemed useful by the community. As such, the original poster’s credibility is improved.
What does this mean for security teams?
The sale of exploits and hiring of coders shows that it is likely that the flaws are being exploited in the wild or will be in the near future. Even knowing which vulnerabilities are being generally discussed is a benefit, as it shows which flaws are popular amongst threat actors. These types of exploits are often also beneficial to initial access brokers who look to gain initial access to an organisation and sell that access to other cybercriminals for further malicious activity. This can result in the theft of sensitive data, extortion attempts, and ransomware or other malware deployment. Furthermore, if researchers observe known ransomware and extortion groups, affiliates of these groups, or malware operators interacting with specific vulnerability posts on forums, it could provide further insights into the group’s tactics, techniques, and procedures (TTPs).
Knowing which vulnerabilities are being discussed on these forums can aid in cyber defence. Oftentimes, large businesses are unable to apply patches as soon as they are released because it could take systems down for a considerable amount of time. By providing IT teams with knowledge surrounding which vulnerabilities are being talked about and sold, it can allow for the patch prioritisation of more critical and exploitable vulnerabilities. Consider the example of two similar vulnerabilities affecting the same product, one might consider patching the on that is being discussed on cybercriminal forums before patching the one that isn’t.
To access our full intelligence repository containing detailed vulnerability insights, click here to take a test drive of CYJAX.
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
