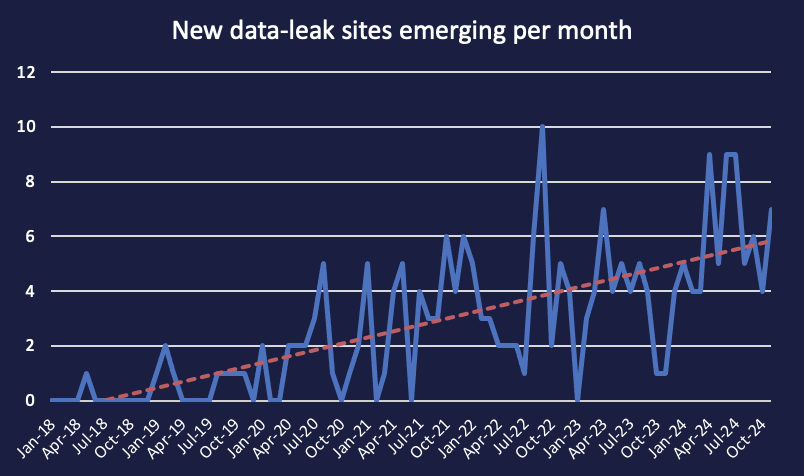
Following the emergence of data-leak sites (DLSs) for new extortion groups Kairos, Chort, Termite, and CONTfr, Cyjax has observed a DLS for a group going by the name ’Argonauts Group’. This group has claimed 10 victims so far. This brings the total of new DLSs discovered this month to seven, with a few days remaining in November. This continues the general trend observed by Cyjax of a greater number of DLSs making their way onto the scene, with an average of six groups emerging each month in 2024. Read on to find out what we know about the Argonauts Group so far.
Context
Extortion groups commonly use DLS to further extort victims, typically proceeding in multiple stages. The first threat is that the victim’s name and news of a successful attack against it will be published on the extortion group’s website. Should this fail to motivate a victim to pay a ransom, the group’s next step is typically to provide proof of the successful theft of its data, such as screenshots of internal file trees, samples of employee or customer PII, or other sensitive documents. The group may add a countdown at this stage, noting that should the victim fail to pay by the conclusion, it will make available to DLS visitors all stolen data, either for free or at cost.
Known locations
The Argonauts Group DLS consists of four main pages. The home page hosts a list of victims from which the group claims to have stolen data, which appears to advertise to visitors to the site should the visitors not comply with the group’s demanded ransoms. Clicking on victim names directs to a specific page for each.

Victimology
So far, the group has claimed attacks against 10 organisations. The victims primarily span the technology and manufacturing sectors and are located in Italy, but some are also based in Taiwan and Japan:
- 15 September 2024 – Taiwan-based medical research organisation Ivy Life Sciences.
- 20 September 2024 – Italy-based manufacturer BOCCHI S.R.L.
- 6 October 2024 – Taiwan-based technology company Hung Jie Technology Corporation (弘潔科技股份有限公司).
- 9 October 2024 – Italy-based manufacturer Contact S.R.L.
- 9 October 2024 – Japan-based technology company Zacros (藤森工業株式会社).
- 22 October 2024
– –Italy– based healthcare organisation Intermunicipal Avis Arnaldo Colombo. - 26 October 2024 – Italy-based aerospace and defence organisation company AIAD.
- 30 October 2024 – Italy-based transport organisation FIT-CISL.
- 8 November 2024 – US-based security solutions company NUUO
Argonaut Group has shared alleged samples of data for two victims, namely Ivy Life Sciences and Zacros. This data includes personally identifiable information (PII), internal documents and blueprints, and file names. The group claims to have stolen over 200GB of data from Ivy Life, and 140GB from Zacros, for which a PDF is available for visitors to download for free.
It is of note that this document is a Chinese-language letter dated 22 October 2024. Here, Zacros appears to acknowledge that its production systems had been restored from back-ups on 27 September 2024, following a ransomware attack that occurred on an unknown date. It is not clear from the letter whether this relates to an incident entirely separate from Argonauts Group’s alleged breach, or whether they are one and the same.
It has advertised the Ivy Life and Zacros data via the DLS “due to the company’s refusal to pay the ransom”. Regarding the other named victims, no data is yet available to view publicly; visitors must enter a password to uncover any other information on the page. Despite the group’s claims, Cyjax has not identified any of the named victims publicly acknowledging any recent cyber incidents.

Other pages on the site are:
- Leak, which lists all alleged victims for which Argonaut Group has shared data samples.
- Sale, which lists all alleged victims for which Argonaut Group is advertising data for sale.
- Sold, which is currently empty. It is assumed that this is the page where the group would list victims, the data of which Argonaut Group has sold.
The Argonaut site appears incomplete. A link to a page titled “About US”, simply resolves to the home page. The bottom of the home page lists icons that would appear to link to the group’s pages on Facebook, X (formerly Twitter), and WordPress, but at the time of writing these do not resolve. A link to “Argonauts Group” directs to 127.0.0.1, which is also known as ’localhost’.
Other locations
Cyjax has identified a user on a prominent English-language data-leak focused cybercriminal forum going by the name ’Argonauts’, who uses the same logo as the Argonauts Group as their profile picture. The account was registered on 21 November 2024 and a total of one post has been made, which has since been deleted. A copy of the post archived by Cyjax saw the user advertising data allegedly stolen from Hung Jie Technology Corporation. Given the shared name, date of account creation, and the naming of a victim initially advertised by Argonauts Group; Cyjax assesses that the same entity likely operates both the DLS and the forum account. The date of the group’s first post is unclear. The post’s date of 15 September 2024 may be accurate, or it may have been backdated following the creation of the DLS. Regardless, the group does not appear to have been actively marketing itself on other locations until 21 November 2024.
Motivation
The group has so far indicated only financial motivation. It has not published any manifesto detailing its goals or ascribed geopolitical ideology. Though the 22 October 2024 Zacros letter appears to refer to a ransomware incident, it is not clear whether such an attack was conducted by Argonauts Group. Given the lack of other references to encryption on the Argonauts Group DLS, Cyjax cannot categorically state whether Argonauts Group operates as a ransomware operation at this time.
Threat assessment
Argonauts group has claimed attacks against a moderate number of medium- to large-sized businesses, mostly in the vulnerable healthcare sector. None of its claimed victims have publicly confirmed the legitimacy of any breaches. The group operates a well-functioning DLS, though it is incomplete. There are no known concrete TTPs associated with the group at this time, and so it is unclear to what extent it is technically capable. As such, it is not presently clear to what extent the group presents a significant or credible threat.
To access our full intelligence repository containing detailed profiles like this one, covering extortion groups, advanced persistence threat groups (APTs), data brokers, hacktivists, initial access brokers, and more, click here to take a test drive of Cymon.
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
