CYJAX’s open-source intelligence team collects data from social media, instant messaging platforms, gated communities, and dark web locations to safeguard clients from threats stemming from online locations.
What is an Insider?
An insider is an individual who leverages their position in an organisation to intentionally or unintentionally harm it. This often occurs through the abuse of access to premises, critical computer systems, organisation products, and company records.
Organisations across industries, size, and locations face the hidden threat of employees becoming insiders.
What do fraud threat actors gain through insider access?
- Access to customer records, payment information, and PII.
- The processing of fraudulent applications, refunds, and sim swaps unimpeded.
- Access to company IP, confidential data, and financial information.
- Intelligence on anti-fraud related matters, such as controls, initiatives, and upcoming projects.
Threat actor recruitment through social media.
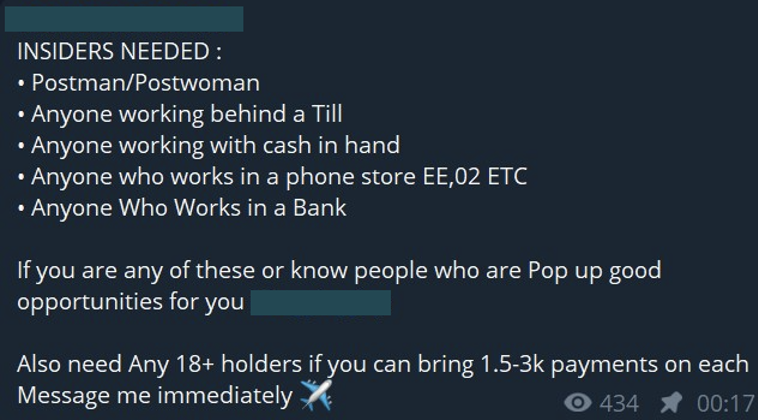
CYJAX’s open-source intelligence team has identified an increase in the number of threat actors using online platforms to recruit, request, and advertise insider access. No longer does a threat actor need to meet a target to understand their role, goals, financial situation, and motivations. Instead, should they choose to, a threat actor can remotely conduct reconnaissance on targets by leveraging publicly exposed information online. By going remote first, threat actors can recruit individuals anonymously and further safeguard themselves from law enforcement, whilst also diversifying their income.

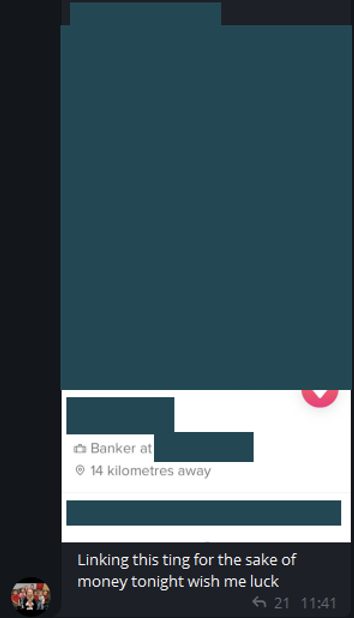
LinkedIn has recently become a hotbed for threat actors to identify, contact, and convert staff into insiders, both willingly and unwillingly. LinkedIn is noted as a useful tool for threat actors seeking to remotely recruit insiders, as a targeted employee’s location information, employer, job role, seniority and, most importantly, contact information are available for public viewing. CYJAX has found threat actors urging other to “DM for Innys” aggressively on LinkedIn within vetted channels of the UK fraud scene which we have unique access to. Fraud threat actors who operate on LinkedIn primarily target employees who have high access to customer data or can approve applications in the financial services, retail, telecommunication, and insurances sectors. Through CYJAX’s research, we have found threat actors direct messaging employees on LinkedIn with the offer of extra money in return for information.
Should an employee show interest in the extra money on offer by the threat actor, communication is swiftly moved over to WhatsApp or Telegram to evade any moderation by LinkedIn. CYJAX analyst note that the move towards WhatsApp and Telegram is due to the voice calling options both platforms offer. Through voice calls, threat actors can instruct an insider without leaving a digital trail of instructions.
Threat actor recruitment through dating platforms.
CYJAX has identified threat actors using dating platforms to recruit insiders. Using platforms such as Tinder, threat actors can target single mothers and recently divorced individuals who work in banking, telecommunications, retail, and government sectors. On many platforms, including Tinder, employment information is displayed for would-be matches to view. Using such information, threat actors can channel their resources towards users of interest. Unlike LinkedIn, platforms such as Tinder pose OPSEC risks for threat actors, as they must meet the intended victim in-person and develop a relationship before they begin slowly turning them into an insider.
CYJAX has noted that threat actors opt to target single mothers for insider recruitment, as they are viewed as ‘easy’ targets within the fraud community. The threat actor starts a normal relationship with the intended insider, subsequently providing financial support for the child. Once the connection has developed into a position of trust, and to keep the relationship going, the threat actor coerces the prospective insider into divulging information under the pretext of a personal business interest. Once the threat actor is confident about the sincerity of the victim, they will begin plans for a large-scale campaign with the insider’s support. Where the victim is unwilling, the threat actor will frame the campaign as a way to pay back all the monetary support the victim and their child received.
Upon completion of several large-scale campaigns, the threat actor will cut their relationship with the victim and return to their home locations.
Post-Recruitment
Typically, a threat actor will offer small payments for low-risk information until trust is established. Once trust is established, the threat actor will subsequently raise the value of payment immediately for slightly higher risk information. This higher risk information includes how to send a fraudulent application such that it is approved or what flags as fraud during a retail order online. Once the threat actor and the individual have an established relationship, the fraudster will offer a significant sum to the insider to take part in upcoming fraudulent campaigns. This includes sim-swap support in telecoms, approving fraudulent orders in retail environments, assisting the approval of fraudulent tax returns, or divulging customer card details in banking environments.
Initial campaigns
As trust is built through small-scale activities into larger scale fraud, threat actors typically seek to fully exploit the insider access they have developed. The first initial major campaign is often kept between the insider, the threat actor, and close associates. The first major campaign, from the visibility CYJAX has unique access to, is the largest earner for both the insider and threat actor. Historically, CYJAX has seen claims of initial campaigns within the UK fraud community earning in excess of £250,000+ in several weeks. This initial campaign is subsequently recreated, only with more threat actors providing data, offering card information, and resources. This consequently cuts the percentage of the profit gained by the insider and principal threat actor.
As the principal threat actor continues to ‘sweat’ their access increasingly, the risks become far greater for the insider themselves. Ruthlessly, threat actors will ramp up their offering of access to other fraudsters within the wider community by responding to insider access requests. Offering access to the wider fraud community historically leads to a lower percentage of profits per campaign. However, it is noted amongst established members of the UK fraud community that this generates income with less risk.
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
