Strategic Foundation
Starting Out
Challenge: Establishing a robust security strategy from scratch can be overwhelming.
How We Help: We assist in building a solid foundation with tailored intelligence and early integration, setting up effective systems and processes from day one.
Better Cyber Decision-Making
Challenge: Aligning security measures with broader business objectives rather than just managing costs.
How We Help: Our contextual intelligence supports strategic decision-making, ensuring your security measures align with long-term business goals.
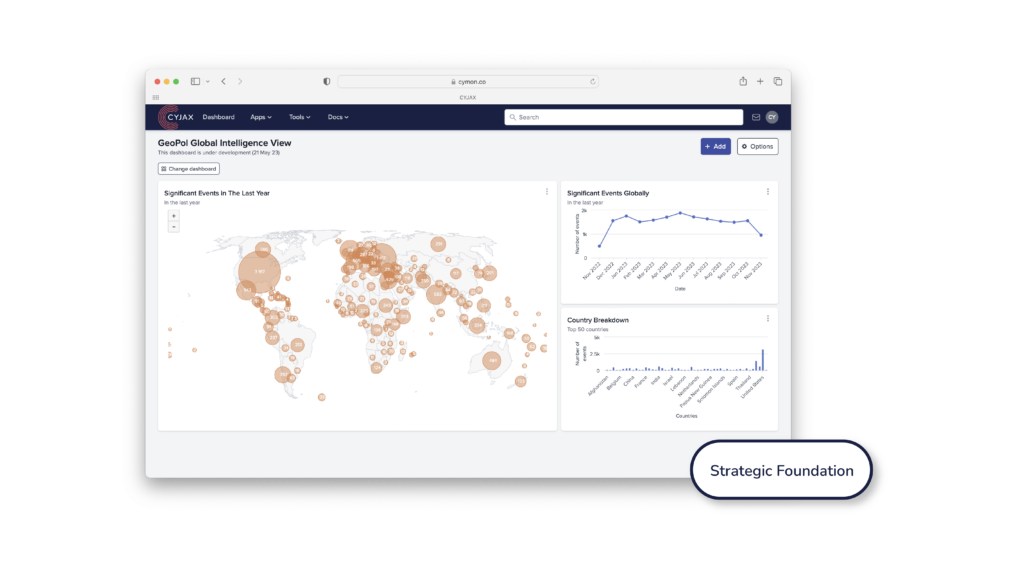
Incident Management and Coverage
Post-Incident Review
Challenge: Post-incident reviews can be complex and time-consuming, impacting your ability to improve security measures.
How We Help: We provide detailed insights and recommendations to analyse incidents, strengthen defences, and prevent future occurrences.
Known Unknowns & Coverage Gaps
Challenge: Uncovering hidden threats and addressing gaps in coverage is essential for comprehensive protection.
How We Help: Our solution identifies and fills coverage gaps, offering targeted insights to protect against emerging risks.
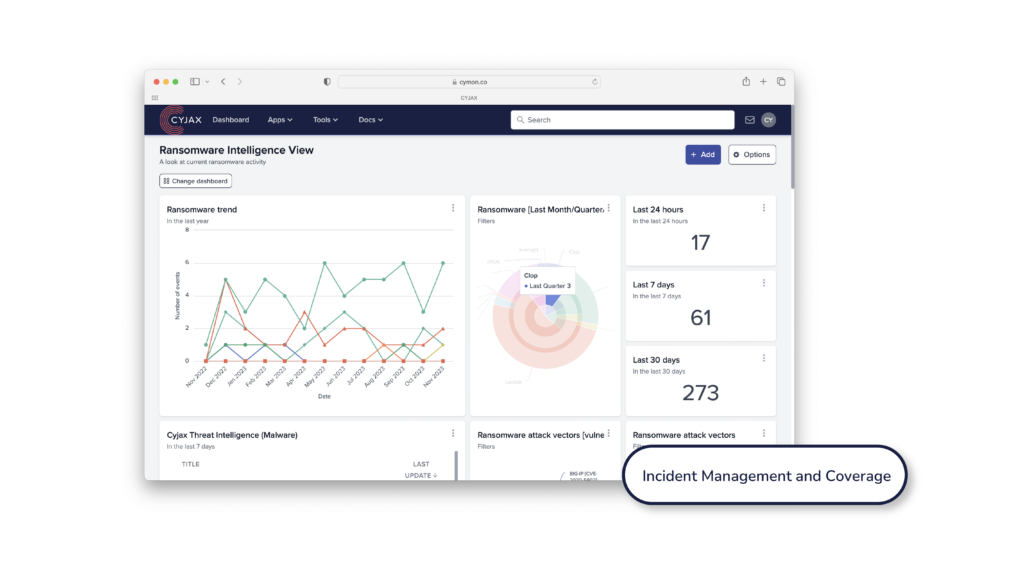
Operational Efficiency
Data Overload
Challenge: Managing and interpreting vast amounts of data can overwhelm teams and obscure critical insights.
How We Help: We streamline data processing, delivering actionable intelligence in a clear format to facilitate faster, more effective decision-making.
Skill Shortage
Challenge: A shortage of skilled professionals can limit your organisation’s ability to manage and respond to threats effectively.
How We Help: We act as an extension of your team, providing expert support and real-time assistance to bridge skill gaps.
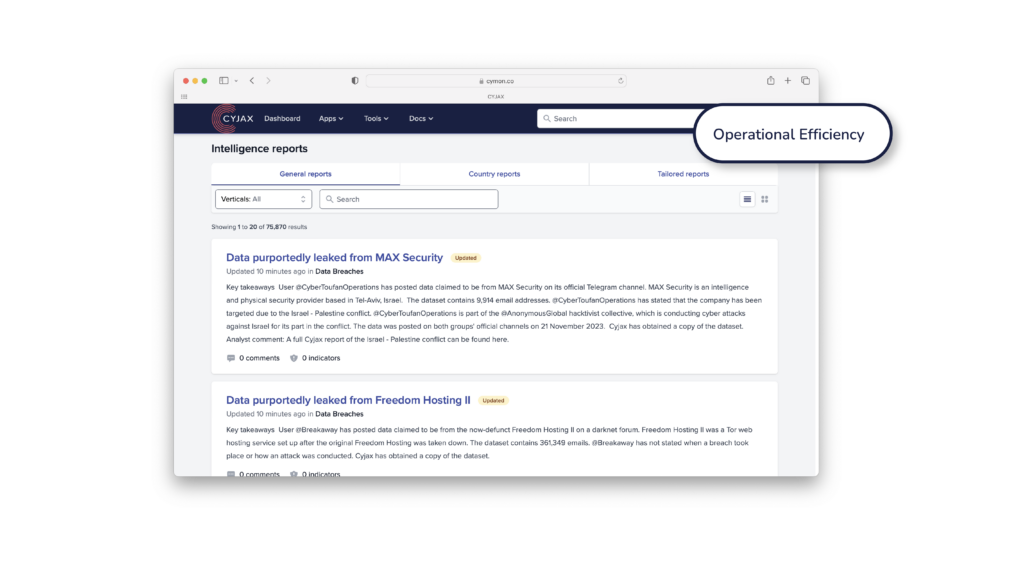
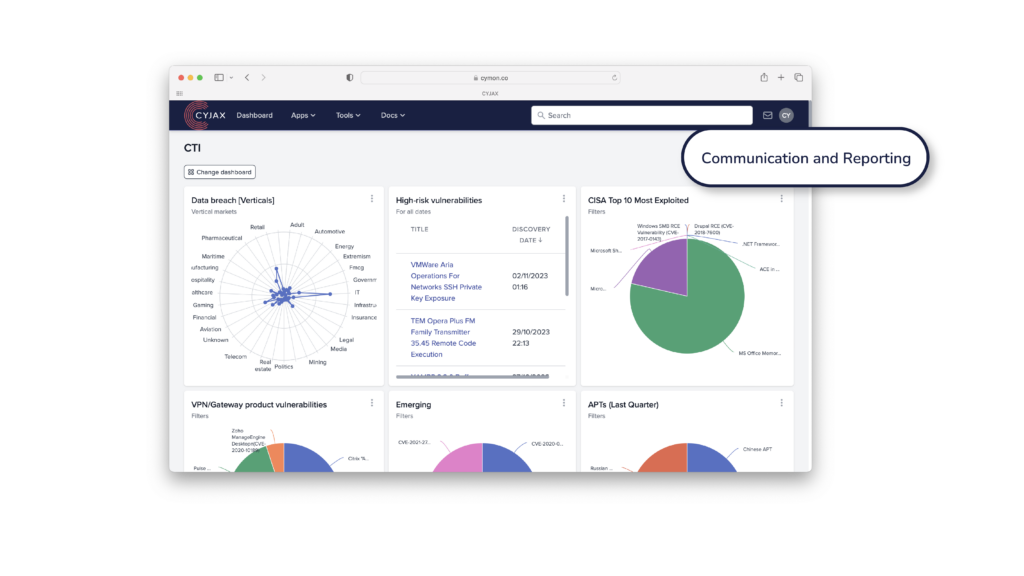
Communication and Reporting
Executive & Board Reporting
Challenge: Distilling complex security data into clear, actionable summaries for executives and boards can be challenging.
How We Help: We provide concise, tailored summaries that make it easier to communicate critical information and align security strategies with executive priorities.

How We Supported a Government Agency in Combatting Brand Misuse
Targeted brand protection
CYJAX deployed Cymon and expert analysis to tackle online brand misuse. We provided real-time, actionable intelligence to identify and address scams, phishing, and reputational threats effectively.
Latest Research
Featured in



-
The ROI of threat intelligence: Measuring the Value Beyond Detection
View More: The ROI of threat intelligence: Measuring the Value Beyond Detection -
The Future of Threat Intelligence: Trends, Tools, and Tactics To Watch
View More: The Future of Threat Intelligence: Trends, Tools, and Tactics To Watch -
Core access: an analysis of the UK government’s demand to Apple
View More: Core access: an analysis of the UK government’s demand to Apple
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.