Transforming threat intelligence into action to prevent attacks.


















We summarise the complex threat landscape, empowering your team to act fast to prevent attacks
Our solutions cut through data overload, seamlessly integrate with your systems, and turn raw data into actionable insights.



Rapid response.
Real-time intelligence.
Simple and effective
No complexity, no delays. Just insight, simplified.
Speed that saves
Faster detection, faster decisions, faster response because every second counts.
Complexity to Clarity
We turn complex data into clear, consumable outputs you can use and share with your board.
CYJAX is your team
We act as an extension of your security function, multiplying capabilities without increasing headcount.





“CYJAX provided the additional context and filtering we needed to rapidly triage and qualify which alerts need actioning. This freed our team up to make adjustments to our security controls, vastly reducing the number of alerts coming in.”



"CYJAX added depth to the broad coverage we already have. We are now able to take quicker and more informed actions as CYJAX is typically 12–36 hours ahead on reportings and key findings."
%20(1).avif)

"CYJAX enabled us to identify which threats were most relevant, helping our team prioritise threats and increasing the efficiency of our security spending."

%20Large.avif)
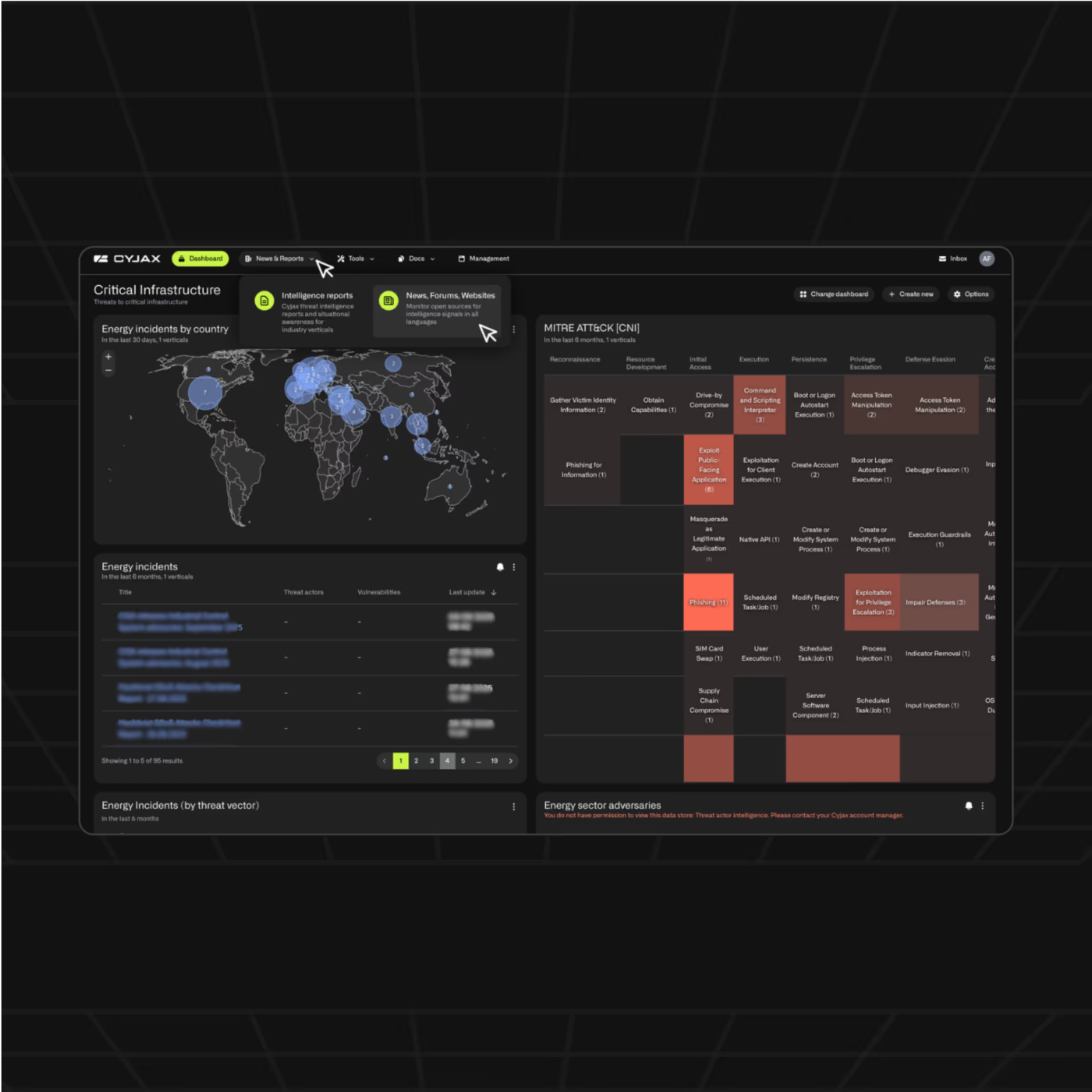
CYJAX Threat Intelligence Hub
Your central source for expert insight, strategic analysis, and deep technical content on the evolving cyber threat landscape
See CYJAX in action
The Gold Standard in Clear, Actionable Intelligence
Centralised dashboard
Automated alerting
Deep-dive research tools
Custom reporting & integrations






