Introduction
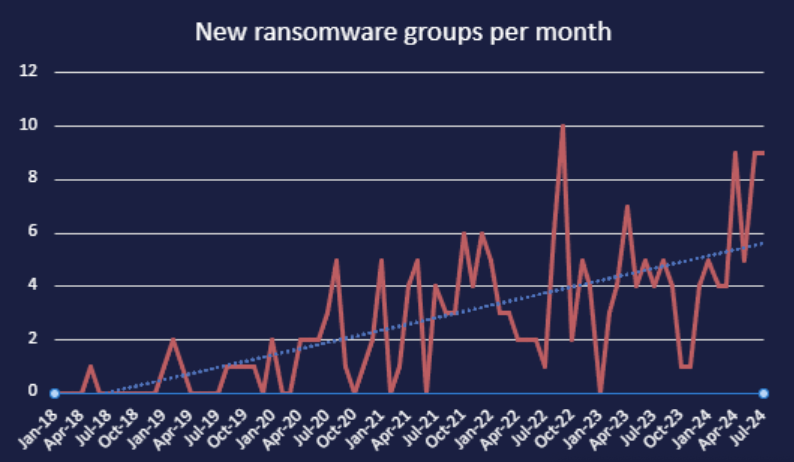
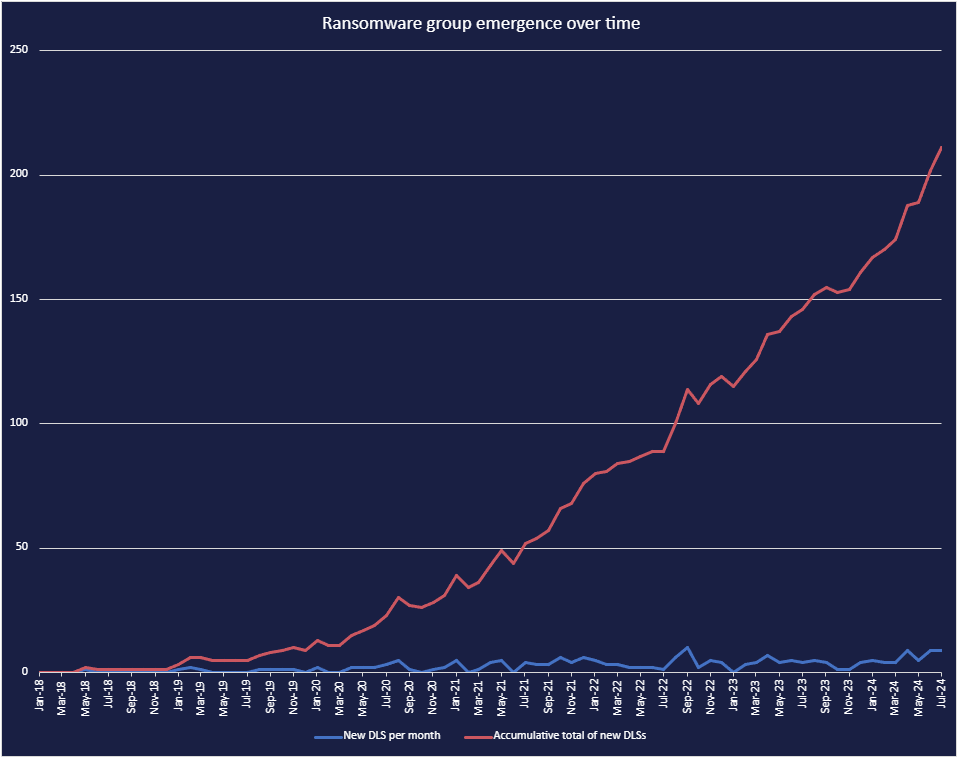
As the threat landscape continues to develop, ransomware and data brokerage groups constantly emerge, develop, and disband. Cyjax observed a relatively high level of data-leak site (DLS) emergence in July 2024, with a total of nine new sites. For reference, the highest observed number of ransomware groups that have emerged in a single month is ten (September 2022).
Of these identified threat groups, there are some that are entirely new, some that were previously active that have now released a Tor-based DLS, some potential rebrands of older groups, and some potential former affiliates that decided to diverge from their original group. However, not all these data-leak sites remain active for long, with some found this month being inaccessible. Additionally, Dispossessor-operated infrastructure was recently seized and disrupted in law enforcement action. This blog aims to examine these emerged sites, explore the different types of DLS emergence, and highlight the ongoing trends in this area in 2024.
DLS emergence vs new threat groups
Ransomware groups often start conducting attacks before creating a DLS, then decide to create one to facilitate the double extortion method, whereby groups encrypt victim systems and leak sensitive data, or increase potential damage to victim from not paying ransoms. Threat actors may not have originally intended to create a DLS, but following a successful ransom, may wish to add more pressure to victims and increase future profits. This is because a DLS provides a personalised, centralised way of leaking data from victim organisations.
The new data-leak sites
It is important to note that not all the below sites belong to ransomware groups. In particular, Pryx is believed to be a data brokerage group which uses malware to infect organisations and steal data, which is then sold on its DLS. Similarly, Dispossessor’s DLS largely consists of reposts of other ransomware groups’ victims.
Dispossessor
Dispossessor was first observed in February 2024 on cybercriminal forums advertising 330 alleged previous LockBit victim leaks. Here, it linked to a Clearnet data-leak site using Dispossessor branding.
At the time of writing, Dispossessor has listed 336 victims on its DLS, though the vast majority of these are reposted from other ransomware groups, such as LockBit, Snatch, Cl0p, and 8base. It is uncertain whether these victims have been targeted by Dispossessor, or if the group is reposting leaks from other ransomware groups and acting as a data broker, rather than a ransomware group.
On cybercriminal forums, representatives of the group appear to be actively recruiting affiliates under the Ransomware-as-a-Service (RaaS) model.
The Dispossessor DLS shares striking similarity with LockBit’s one. This, and the original forum post advertising 330 LockBit victim leaks, suggests that the group may consist of former LockBit affiliates. There is currently no public information regarding a ransomware binary Dispossessor uses.
The fact that the group may consist of former LockBit affiliates highlights a trend in which ransomware affiliates repost victims they were responsible for attacking. This is either for additional monetary gain, or to gain ransom payment from a victim which did not originally pay. For example, former ALPHV affiliates joined RansomHub following the group’s potential exit scam. The attacker allegedly responsible for the Change Healthcare attack used RansomHub’s DLS to relist the victim, as ALPHV reportedly stole the ransom payment from the affiliate.
On 12 August 2024, the FBI released a statement announcing the disruption and shutdown of several servers owned by the group, including its DLS.
Pryx
Pryx is a data brokerage group which operates on several prominent cybercriminal forums, with accounts being created in June 2024. These accounts were created prior to the group’s DLS, which was discovered in July 2024. Pryx states it is not a ransomware group, but rather a “cybercriminal or threat actor”, and is believed to use a remote access Trojan (RAT) to infiltrate organisations and exfiltrate sensitive data.
There are currently two victims named on the group’s DLS, including the UAE government and a US-based university; however, Pryx sells many more data leaks on cybercriminal forums. The DLS is used more as a blogspace for advertising these leaks, as well as promoting the group itself.
While public activity does not hold evidence of extortion, it is possible that the group extorts each victim before attempting to sell data leaks on cybercriminal forums.
Good Day & Chilelocker
While this DLS was identified in July 2024, it names no victims and is down as of August 2024.
It is possible that the DLS, from naming convention, is related to the Good Day ransomware. The ransomware is a variant of the ARCrypter family, and has previously had multiple Tor-based sites for corresponding attacks.
The Chilelocker DLS is also offline in August 2024, with no confirmed listings made on the site.
Like Good Day, Chilelocker is also the name of an ARCrypter variant which was first reported in August 2022. However, it is unconfirmed whether the new DLS relates to this variant, or whether the same threat actor responsible for operating the ransomware has created the site.
Mad Liberator
Mad Liberator, which is allegedly “made up of hackers from around the world”, published its DLS in July 2024. It has listed nine victims as of August 2024. No details are available regarding the type of ransomware used in attacks, other than that files are reportedly encrypted with AES-RSA; however, it is clear the group likely uses the double extortion method. Mad Liberator allegedly gives victims one day to pay the ransom before listing their name on its DLS, then allegedly provides a five-day notice before publishing any data.

Nullbulge
Nullbulge claims to be “a hacktivist group protecting artists’ rights and ensuring fair compensation for their work”, specifically targeting organisations which have allegedly promoted cryptocurrencies, produced AI-generated art, or conducted any form of IP theft.
While Nullbulge has been active since early 2024, and the associated sites were created in June 2024, posts regarding the group’s activities, as well as links to data leaks, appear to have been uploaded on 12 July 2024.
Research indicates that Nullbulge uses commodity malware such as PlugX and AsyncRAT, as well as a leaked Lockbit Black builder to create payloads for facilitating attacks against its targets.
Ransomcortex
Ransomcortex began posting on its DLS on 11 July 2024, subsequently listing four different healthcare organisations as victims. This is particularly notable as large ransomware groups, such as LockBit, often avoid encrypting data from healthcare and critical infrastructure due to the potential physical harm it may cause and associated subsequent law enforcement attention. It is currently unclear whether the group exclusively targets healthcare organisations. It has stated that it does not allow attacks against Russia, the Commonwealth of Independent States, Cuba, North Korea, Iran, and China.
The group has previously stated that it does not operate under the Ransomware-as-a-Service model and uses third-party encryption software in its attacks. However, the specific TTPs and malware utilised by the group have not yet been identified.
At the time of writing, the Ransomcortex DLS is active, but shows an “offline” status, with no available data leaks or further information. It is unclear whether the group is stopping attacks, has not successfully infected any new victims, or is encountering another form of disruption.
Vanir group
Vanir Group operates a Tor-based DLS that has the appearance of a command-line tool, a style previously used in the Akira ransomware group DLS. As of August 2024, Vanir Group has three victims listed on the site, each stating the alleged date that data was exfiltrated.
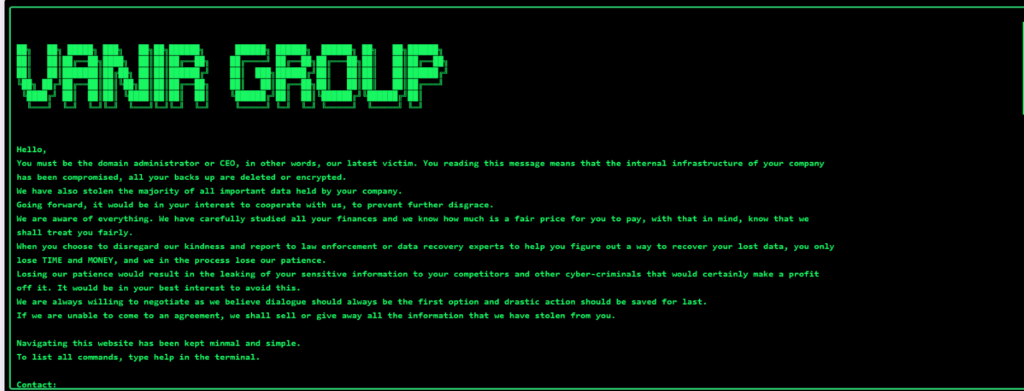
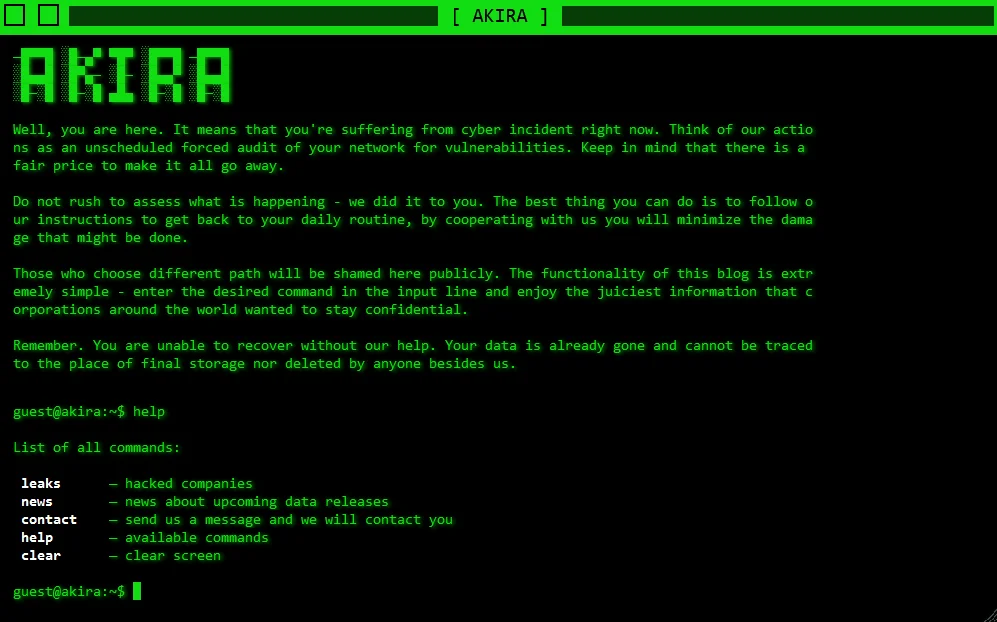
Vanir Group operates under the RaaS model and advertises on its DLS for new affiliates. If ransom demands are not met, the group lists allegedly exfiltrated data such as source code on the DLS and advertises it to other threat actors.
As with other groups which emerged in July 2024, there is little information regarding the group, other than its claimed victims. Its TTPs and victimology have yet to be determined.
Lynx
While the Tor-based DLS operated by Lynx is unavailable as of August 2024, the unsecure Clearnet mirror is active. Lynx purports to be a financially motivated threat actor that does not target the government, healthcare, and NGO sectors.
The group first posted on its DLS on 17 July 2024, and has since published a total of seven victims, each containing samples to act as proof of compromise. For several of the listings, a filetree is available to view exfiltrated data. Upon accessing a specific file in the filetree, the site redirects to a cloud storage site potentially operated by the group, from which the data is available.
Lynx appears to use its own ransomware binary to conduct attacks, with encrypted files given the extension ‘LYNX’. There is no current indication that the group is using the same style, TTPs, or malware of another threat group.
Are data-leak sites necessary?
Ransomware groups may find success in extorting their victims without requiring a DLS. For example, a ransomware group that emerged in late June 2024 called Volcano Demon reportedly uses an encryptor named LukaLocker to attack organisations. Notably, Volcano Demon uses phone calls to directly communicate with the affected organisation, calling high-level executives to negotiate payment. These anonymous calls have been described as “threatening in tone and expectations”.
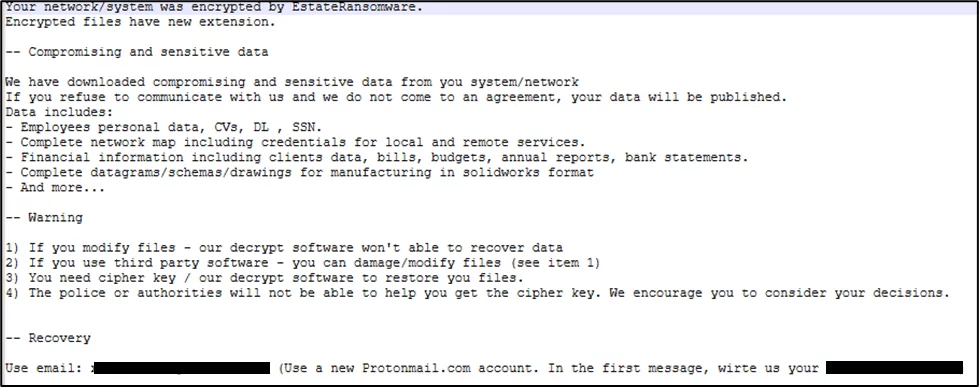
Another notable tactic used by a recently emerged ransomware group is to state that files will be published, without the presence of a known DLS. EstateRansomware, which was first identified in April 2024, does not appear to have a DLS. However, its ransom note states that data will be leaked if ransoms are not met. EstateRansomware may later decide to create a DLS to leak victim data; however, as of August 2024, a site does not appear to exist, suggesting that its current tactics may be successful.
The note may have been copied from another ransomware group, with EstateRansomware erroneously hinting to the existence of a DLS. However, this ransom note indicates that double extortion is being used against the victim, whether real or not. Regardless of the existence of a DLS, the threat of data leakage exists. Therefore, victims would likely be under the impression that data will be leaked upon not paying the ransom, potentially urging payment.
Continued emergence vs. continued degradation
Cyjax has noted the trend of increasing ransomware DLS emergence in “Here, There, Ransomware: The Surge of New Ransomware Groups”, with an average of 5.5 new groups emerging per month in January to May 2024. This has now increased to 6.7 per month. The rate at which DLSs emerge appears to be increasing, though these sites may not remain active in the long term, as highlighted by ChileLocker and Good Day.
There seems to be two types of ransomware groups regarding activity and DLS existence. The first group comprises those that have existed for a relatively long time, such as Clop, LockBit, BlackBasta, Medusa, Play, and Akira. These are unlikely to stop conducting attacks and posting victims, unless the group publicly splits apart or is targeted by law enforcement, though groups such as Lockbit remain active following law enforcement action.
The other group is a rotating cast of new and small ransomware groups that appear to remain active for around a month, then either disband or rebrand. It is unclear whether these groups are the same, or different members each time.
For example, ransomware group Trinity created a DLS and published three victim posts on 12 June 2024. The DLS itself remains active as of August 2024; however, the production value, capabilities, and content appear minimal in nature. The three victims had a “publication date” of 30 July 2024; however, no further details, or any data leaks, were published after this date. While it is possible that the group remains active and will continue posting on the DLS, it is possible that the group did not find sufficient monetary gain through ransomware attacks to remain active.
Similarly, Zero Tolerance Gang was identified in May 2024, with only one victim posted on its DLS. At the time of writing, the DLS appears to be inactive, or offline, and no further victims were released on the site.
Also, considering those observed emerging in July, Dispossessor’s DLS contains misconfigurations which highlight usage of React templates to create the site, for which evidence was not removed. Good Day and ChileLocker did not have accessible data-leak sites as of August 2024, with the Lynx Tor-based DLS similarly inactive, though the Clearnet version was active. Finally, the Ransomcortex site was active, but claimed to be offline and no longer had previously listed victim data hosted on the site. This may indicate that these threat actors do not have the technical capabilities or available time to create a complete, secure, and functional DLS. It may also indicate that new ransomware groups may focus more on conducting attacks to facilitate short-term monetary gain, before moving onto the development of the DLS.
Conclusion
DLS emergence appears to be increasing, regardless of how long each DLS remains active. Cyjax has observed that many of these newly emerging sites typically do not remain active for long in comparison to their elder peers, with several of the sites that emerged in July 2024 already showing a lack of activity.
The ransomware ecosystem continues to develop. There is a constant battle between law enforcement and large ransomware groups. Newer groups are starting to gain more prevalence and threat actors are emerging into cybercrime with open-source ransomware and pre-built binaries, as well as under the RaaS model.
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
